Latest Open Source Bug Bounty Projects Launched by Google to Control Supply Chain Attacks

Last Monday, Google introduced its latest Open-Source Bug Bounty Projects, paving the way for bug bounty hunters for a payout ranging anywhere from $100 to $31,337 (a reference to Eleet or Leet) to safeguard the cyber environment against Supply Chain Attacks.
Widely termed the Open Source Software Vulnerability Rewards Program (OSS VRP), which is one of its kinds as the first open source-based vulnerability program.
It is intended that this OSS VRP Project targets to distribute awards to major vulnerability findings that could certainly have a genuine impact on the greater open-source market as Google – the supergiant in the tech industry has already maintained some of the premium projects such as Angular, Bazel, Golang, Protocol Buffers, Fuchsia, etc.
Moreover, the other primetime projects monitored by Google which are hosted on public depots like GitHub as better than the third-party addictions, which are comprised in those particular projects are also eligible.
However, there are certain guidelines that need to be followed by bug hunters to meet the following aspects:
- Shortcomings that lead to supply chain compromise in any possible sense.
- The varied design concerns that generate product vulnerabilities.
- Moreover, some other kinds of security concerns like sensitive or leaked credentials, feeble passwords, or unsafe installations
Whining up open-source elements, specifically third-party libraries that operate as the structure block of many software, has appeared as a top preference in the name of the constant increase in Supply Chain Attacks nicely focusing on Maven, NPM, PyPI, and RubyGems.
Taking Learning from the Past
In the same vein, a December 2021 example could be taken nicely from the very renowned Log4Shell vulnerability in the Log4j Java logging library that resulted in extensive chaos that became a clear call for enhancing that particular time conditions of the software supply chain.
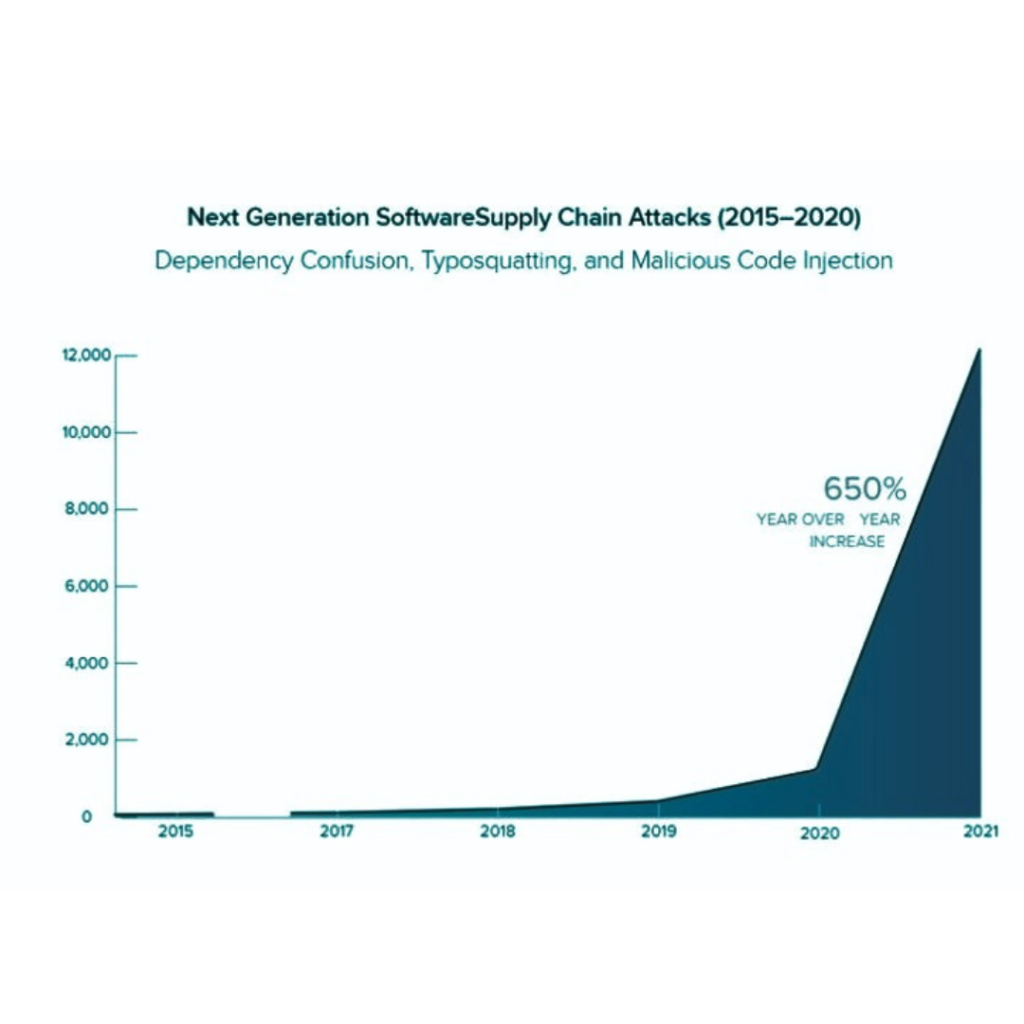
As per Google’s Francis Perron and Krzysztof Kotowicz, “Last year saw a 650% year-over-year increase in attacks targeting the open source supply chain, including headliner incidents like Codecov and the Log4j vulnerability that showed the destructive potential of a single open source vulnerability.”
The famous tech giant had also shown the same kind of interest last November 2021 for revealing high-end escalation and Kubernetes escape exploits in the Linux Kernel. In addition, the same project has upped the maximum amount from $50,337 to $91,337 going until the end of the current year.
Read More: Windows Users are requested to conduct a patch for DogWalk Zero-Day Vulnerability by Microsoft
Watch more news : https://www.news4hackers.com/akasa-data-hacked-airline-asks-customers-to-be-vigilant-against-possible-phishing-attempts/
FTC Sues Data Broker Over Selling Location Data for Hundreds of Millions of Phones







