A Clever Phishing Attempt is Concealed by a Fake DocuSign Email
A Clever Phishing Attempt is Concealed by a Fake DocuSign Email
During my daily rounds, I came across a phishing attempt that employed a smart delivery strategy that wasn’t quite out of the ordinary. What started as an ordinary DocuSign notification evolved into a complex scam that included Webflow, a dubious redirect, and a genuine Google login page.
Designers and developers can construct unique, responsive websites with Webflow, a visual website builder. Users may create, develop, and launch websites visually in the browser with this no-code solution.
The attack begins with an email referencing a finished DocuSign document that purports to be from a known contact.

The email had a false impression of validity because it passed DMARC, DKIM, and SPF. A Webflow preview URL was accessed by clicking on the “View the completed document” link. These URLs allow designers to display their work and create website prototypes. By this time, it began to appear dubious but not explicitly malevolent.
However, preview links should always raise questions because they are not normal for DocuSign. A valid DocuSign request would indicate:
- com
- net
- eu (for European users)
However, the phishers ensured that their initial stage was unlikely to be blocked by using the authentic Webflow domain.
I clicked through (on a virtual machine, not my real computer), even though I often tell others not to do that.
A simulated DocuSign-style interface with just one button, “View Document,” was shown in the Webflow preview.
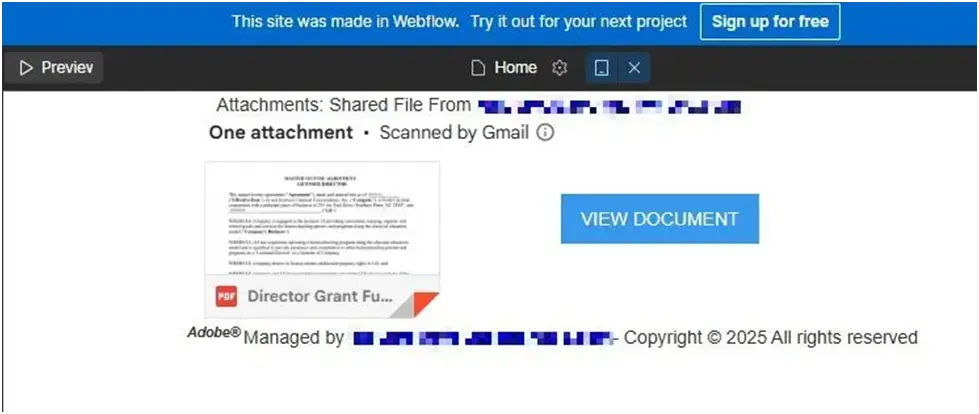
It was becoming hairy now. That button pointed to sjw.ywmzoebuntt.es, a domain that raised a red flag.
The domain appears to be a random string, which is a well-known phishing infrastructure technique to get around reputation-based security.
I was directed to this phony Captcha when I clicked the “View document” button, which is obviously not intended to prevent anyone from continuing.
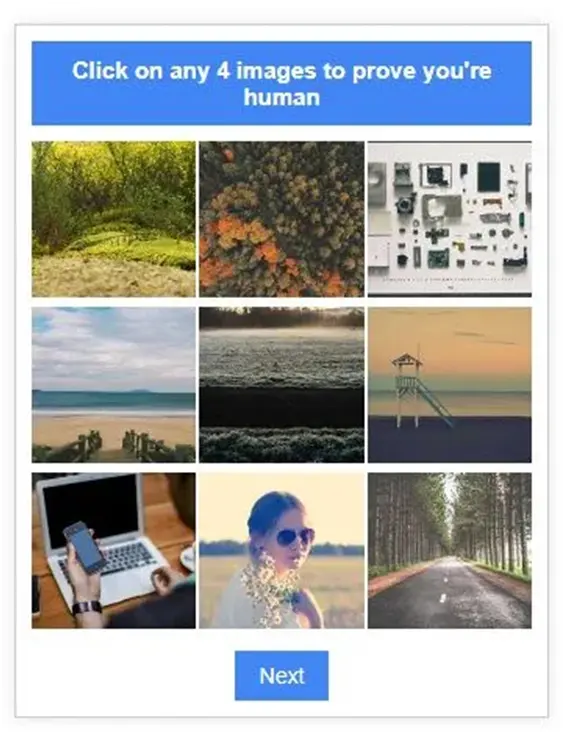
Although captchas are frequently employed in phishing schemes to trick victims into believing they are undergoing a genuine security check, it is obvious that the phishers did not want to overwhelm any potential targets. The lowest bar for a security check may be “click on any four images to prove you’re human.”
I was taken to Google’s actual login page after this lengthy intellectual battle.
Just Google, no malicious downloads, no phony forms. Because of this, attacks of this nature are simple to overlook and even simpler to undervalue.
Most likely, a veiled page for fingerprinting was momentarily shown by the fraudulent link. To complete the appearance of security, it collected browser metadata such as IP address, user agent, language, and screen resolution and sent it to Google. I was sent to a “safe place” since my system was probably rejected based on my system fingerprint, indicating that I was not the intended target.
A data reconnaissance operation that scopes a target and hones follow-up attacks is phishing with a twist. The URL set off a series of questionable actions, including changing user registry entries, probing browser storage, and requesting BIOS and CPU IDs (all while I was wondering why all Captchas are not like that).
If you click on a link similar to this:
- Empty the cache and cookies in your browser.
- Examine your past login history.
- If you haven’t already, turn on 2FA.
- Do a thorough malware and antivirus scan.
Remember: The attempt did not fail just because there was no visible virus. It could indicate that the attackers are only beginning their work.
This attack appeared to be very focused. To prevent being a victim, you ought to:
- Do not open unsolicited emails and click on links. Before continuing, get in touch with the purported sender via a different route.
- Learn the standard operating procedure so that unusual occurrences will be cause for concern.
- To stay safe, use an active antimalware program with web protection.
How To Secure Yourself from Such Phishing Attempts?
If you wish to hire a professional to provide the necessary Penetration Testing Service for you, then it is highly recommended that you contact Craw Security, the leading VAPT Services Provider in India and many other prominent nations in the world, and the sister vertical of News4Hackers. Individuals with the full intention of becoming a fear-free entity from any possible cyberattacks due to the presence of vulnerabilities and loopholes in the varied IoT devices of the target IT infrastructure should contact us as soon as possible.
To know more about the best price for you or your organization, kindly contact us at our hotline number, +91-9513805401, and have a word with our superb penetration testers with more than 8 years of qualitative work experience.
Read More:
Sri Lanka Arrests 60 Indian Nationals for Cybercrime Activities