Attackers Phishing Industrial Manufacturing Companies Using Fake NDAs and “Contact Us” Forms
Attackers Phish Industrial Manufacturing Companies Using Fake NDAs and “Contact Us” Forms
Check Point researchers have alerted enterprises involved in industrial manufacturing and other vital supply chains to a newly discovered phishing effort that is meticulously crafted to evade security measures and evade detection by its targets.
The phishing campaign(s)
The experts think that threat actors with financial motivations are behind the initiative.
In order to deliver a proprietary in-memory implant/backdoor known as “MixShell,” it will first provide a malicious ZIP archive containing a PowerShell script that will run in memory. The malware performs remote file manipulations and command execution using DNS TXT tunneling with HTTP fallback for C2 interactions.
The effort made to persuade staff members at the victim organizations to believe the email and download and execute the infected ZIP file is what makes this campaign the most intriguing.
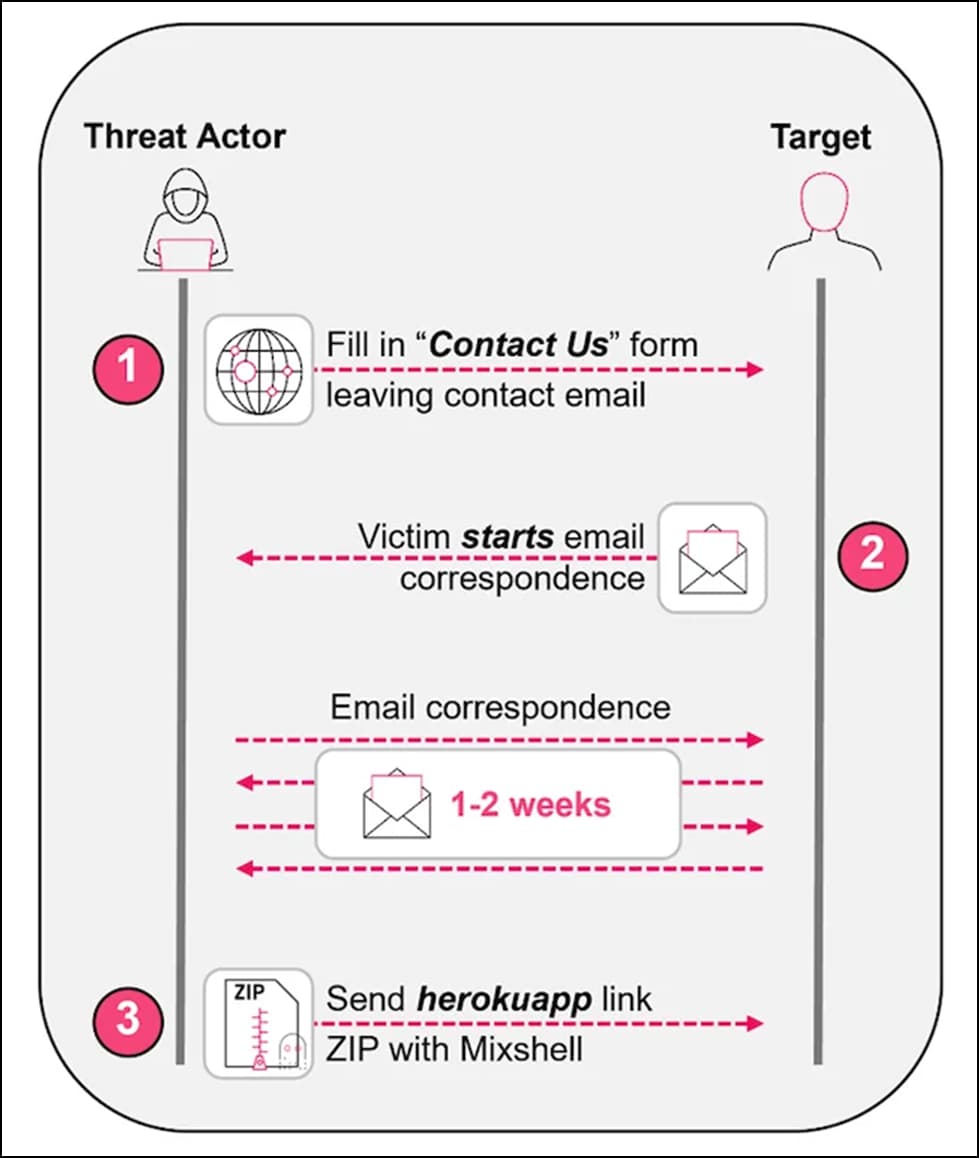
The attackers successfully tricked victims into starting email interaction and automatically got over reputation-based email filters by contacting them using the “Contact Us” form on the target companies’ website.
According to the study, “Attackers spend days or weeks having professional, credible conversations, frequently asking the victim to sign a Non-Disclosure Agreement (NDA).” (The NDA paperwork can be used as both a decoy and a bait.)
The domains that the threat actors use to send emails seem to have been deliberately chosen for validity and trustworthiness. Some of these domains may have once belonged to actual firms, and many of them match the names of LLCs registered with US-based companies.
Over five years have passed since these domains were first registered. The attackers were able to deceive security filters and potential victims thanks to their well-established reputations and authentic corporate histories.
How the attackers trick the recipients (Source: Check Point Research) {Make Similar Image}
After gaining the users’ trust, the attackers requested that they download the malicious file via a subdomain of herokuapp.com.
A more recent wave of phishing emails linked to the same effort has also been observed by the researchers: The attackers are emailing staff members directly, claiming to be collaborating with the company to assist in executing AI-driven operational changes, rather than contacting them through the “Contact Us” form.
The email asks the recipient to complete a brief survey regarding the potential effects of artificial intelligence on their team’s workflows. It is presented as an internal initiative and is titled “AI Impact Assessment.” The attacker specifically claims that the company’s leadership asked the receiver for their personal feedback, suggesting that their viewpoint will impact future choices, in order to provide credibility and urgency, the researchers observed.
The researchers were unable to verify that the malicious payload (that will be used) is identical because this campaign is still in its early stages.

The victims
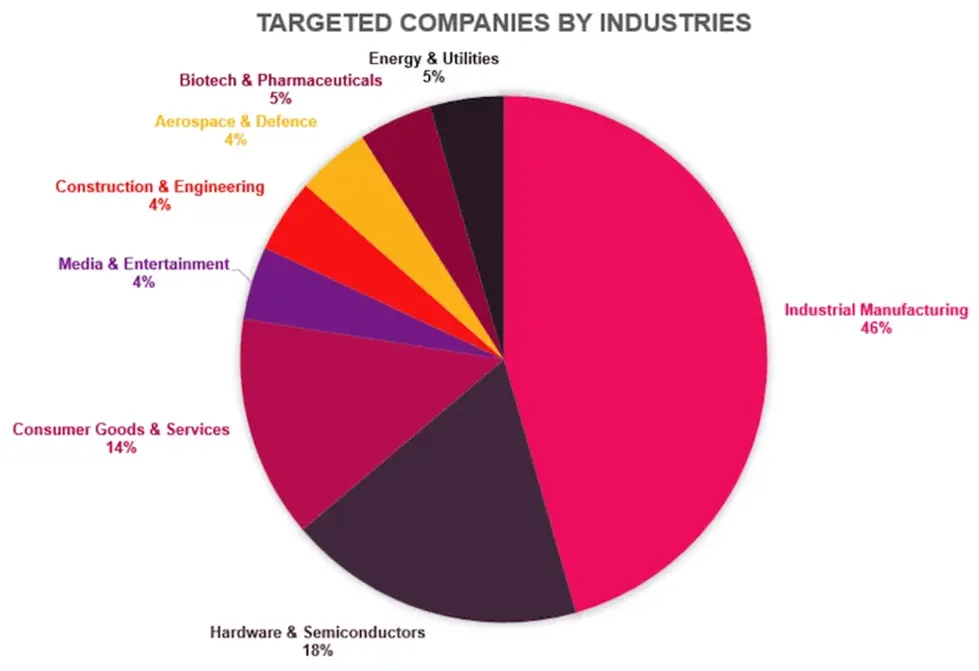
Though mostly in the US, the attackers have attacked businesses in a variety of industries.
They mostly target enterprise-level businesses, but they have also targeted small and medium-sized enterprises (SMBs).
According to the researchers, “the attacker is willing to invest time cultivating the relationship regardless of company size, possibly tailoring their efforts based on perceived value or ease of compromise,” given the length of time they spent speaking with the victim (multi-week discussions).
While businesses in Singapore, Japan, and Switzerland were also targeted, over 80% of the targets in this campaign are situated in the United States, highlighting a distinct regional emphasis. In terms of initial access points, communication style, and infrastructure, the interaction patterns were primarily U.S.-centered.
Find Out If Your Organization’s Security Levels Against Such Phishing Attacks Targeted by Remote Cybercriminals Now!
All MFA systems are vulnerable to hacking, and in certain situations, it only takes sending a phishing email. Knowing the precise security threats your MFA solution poses and how your users’ accounts could be compromised is crucial.
Here’s how Craw Security’s Phishing Simulation Services works:
- We have a credential capture mode that tricks users into submitting crucial information.
- A bulk of templates that mimic MFA/ 2FA using time-based storing and authenticator code algorithms.
- Our MFA also has a multi-form interface that makes it feel legitimate in the eyes of the targets.
- Adaptive MFA Challenge Scenarios, such as geo-location, device fingerprinting, or time-of-day anomalies, to deliver targeted training to users.
You just need to give us a call at our 24X7 hotline mobile number, +91-9513805401, to have a word with our high-tech group of penetration testers with more than 7 years of classic work experience in pentesting more than 1200 IT infrastructures for 850+ organizations. Here, Craw Security is the sister company of News4Hackers, delivering quality VAPT Solutions in India, including Phishing Simulation Services in India. Make a call now for our best prices and customized plan for diverse niche organizations!
About The Author:
Yogesh Naager is a content marketer who specializes in the cybersecurity and B2B space. Besides writing for the News4Hackers blogs, he also writes for brands including Craw Security, Bytecode Security, and NASSCOM.
Read More:
Google’s Warning Users To Turn On 2SV: 2.5 billion Gmail Users at Hacking Risk






