Google Ads Utilized to Inject Trojan Malware Disguised as TradingView Premium

Google Ads Utilized to Inject Trojan Malware Disguised as TradingView Premium
Bitdefender cautions that YouTube and Google advertisements are now the targets of the TradingView Premium ad fraud, which uses authenticated channels to propagate adware.
Security researchers caution that a malicious advertising campaign that has been deceiving content creators and gullible users into installing malicious software by promising “free access” to TradingView Premium has significantly increased the scope of its activities.
According to reports, this continuous campaign, which Bitdefender Labs has been monitoring for the past year, has shifted from Meta’s Facebook Ads to show up on Google Ads and YouTube, endangering a lot more individuals.
This campaign has changed its strategies after Hackread.com first exposed it for utilizing Facebook Ads to distribute malware by using phony cryptocurrency websites and celebrity photos.
How the Scam Works
According to research, the highly organized cybercriminals responsible for this attack post thousands of malicious advertisements daily in several languages (primarily English, Vietnamese, and Thai) and use more than 500 distinct internet addresses.
They use authentic, verified business accounts on Google and YouTube to broadcast their advertising, such as the Google advertiser account of a Norwegian design firm that was taken over. Just so you know, TradingView Premium is a premium service that provides sophisticated features and tools for financial trading research.
Fake ad and the hijacked accounts used in the attack (Via Bitdefender Labs)
The scammers take over a legitimate YouTube channel, remove all of its original content, and rename it to resemble the official TradingView page—complete with the appropriate banners and logos—in order to make it seem authentic. They even exploit the verified logo to deceive users into thinking the phony channel is authentic by copying playlists from the real one to make it look current.
Then, in order to evade discovery, they use sponsored advertisements to promote unique videos that are not visible to the general public. Through this relentless advertising, one such video, “Free TradingView Premium – Secret Method They Don’t Want You to Know,” received over 182,000 views in a matter of days.
On closer examination, though, there are warning signs that the well-known trading platform could not have, like a different channel handle (not @TradingView) and a low total number of registered views.
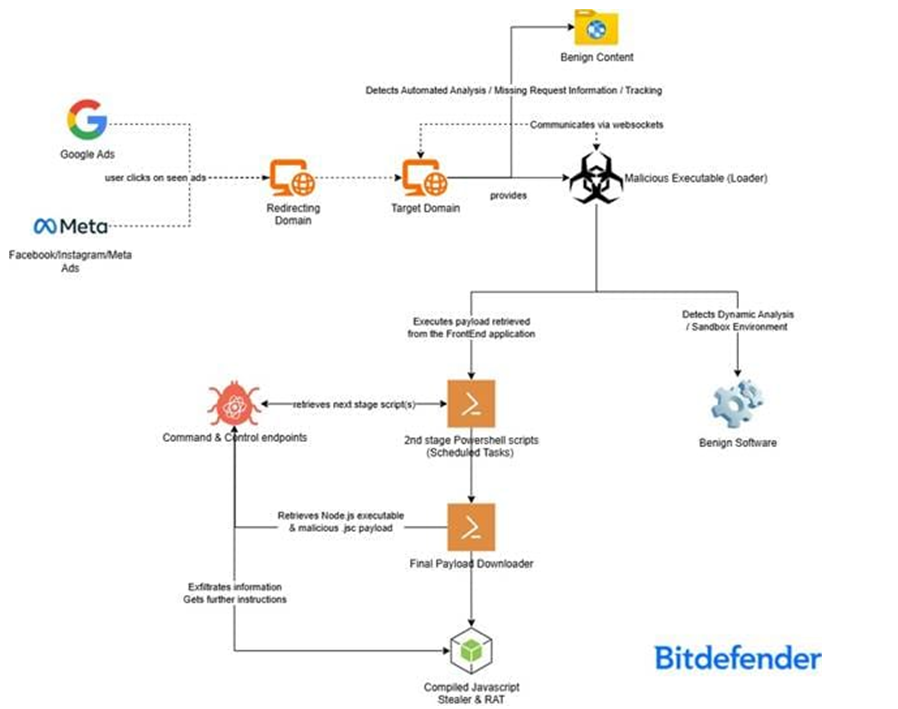
Attack Flow (Image Credit: Bitdefender Labs)
The Threat
It appears that the main goal of this campaign is to trick consumers into downloading a malicious file under the guise of a free premium app. This file is actually a Trojan.Agent.GOSL is a sort of spyware that has the ability to take over a victim’s computer remotely. Passwords, personal information, and cryptocurrency wallet details are among the extremely sensitive data that this malware is intended to acquire.
This study, which was shared with Hackread.com, cautions content producers that having their business accounts hijacked might harm their reputation and provide scammers access to the verified, connected YouTube channel, enabling them to use it as a weapon.
Software should therefore only ever be downloaded from official websites. Users are advised by Bitdefender to carefully examine the channel handle and subscriber count, and to be extremely wary of any advertisement that offers free premium access to an app that is typically paid for.
About The Author:
Yogesh Naager is a content marketer who specializes in the cybersecurity and B2B space. Besides writing for the News4Hackers blogs, he also writes for brands including Craw Security, Bytecode Security, and NASSCOM.
READ MORE HERE