UNC6229 “Fake Career” Campaign Hacking Advertising A/cs with Fake Jobs Exposed by Google
“A Fake Career Campaign is hacking advertising accounts with fake jobs exposed by Google.”
An ongoing social engineering campaign run by the Vietnamese-based, financially driven threat cluster UNC6229 has been made public by Google’s Threat Intelligence Group (GTIG).
The organization deceives digital marketing and advertising experts into installing malware or disclosing corporate credentials by promoting phony job openings on reputable recruitment portals. This compromise ultimately jeopardizes valuable advertising accounts for financial gain.

GTIG (Google’s Threat Intelligence Group)
| “By advertising fictitious career possibilities on well-known job boards, freelance markets, and their own job posting websites, this campaign takes advantage of the trust that comes with the application process.”
“Threat actors can obtain access to company accounts if the target is logged into a personal account on a work computer or uses a personal device that has access to company advertising accounts.”
“This campaign’s success depends on a traditional social engineering technique in which the victim makes the initial contact.” “UNC6229 fabricates firm profiles on reputable job boards, frequently posing as a digital media agency. They advertise appealing, frequently remote, work opportunities that appeal to their target market.”
“To send these initial emails and oversee their campaigns, GTIG has seen UNC6229 and other threat actors misuse a variety of trustworthy business and customer relationship management (CRM) platforms,” the report states.
The organization has even used Google AppSheet and Salesforce to coordinate campaigns, taking advantage of their reputations to get past email security measures. To improve ecosystem security, GTIG responded by stating that it “shared insights about these campaigns with CRMs UNC6229 has abused, including Salesforce.”
“With high confidence, GTIG concludes that this activity is carried out by a group of financially motivated individuals based in Vietnam.” |
The attackers target remote workers in digital advertising, who are frequently contractors or freelancers and are more likely to handle several client accounts and utilize personal devices for work-related tasks.
Once inside, the attackers either sell access to other cybercriminals or take over the company’s digital advertising accounts, making money off the credentials they have stolen on black markets.
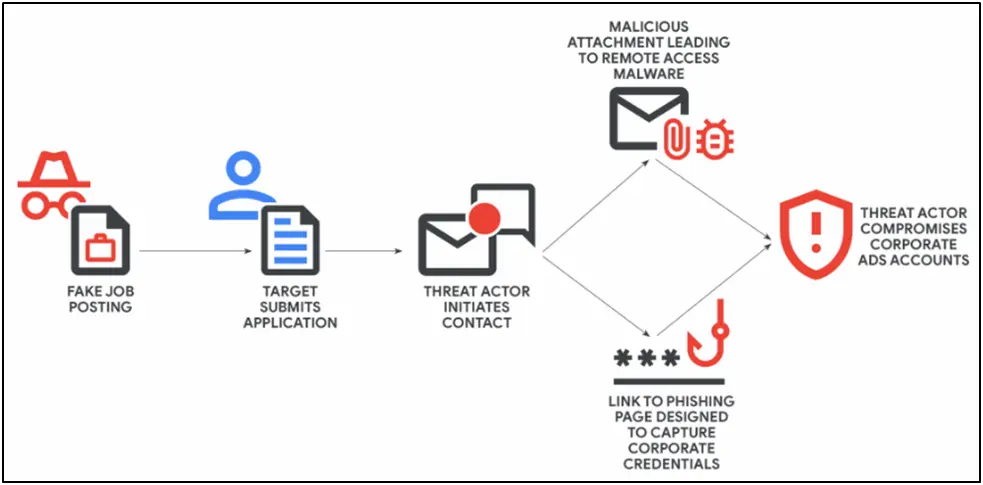
Internally known as “Fake Career,” the scheme starts with extremely well-crafted job postings on reputable websites like Indeed and LinkedIn. These ads mimic digital marketing firms, complete with fake social media profiles and websites that are meant to look real.
After a prospect applies, attackers pose as recruiters and utilize the contact details they have provided to get in touch, frequently through chat platforms or email. Before releasing the actual payload, these first communications are purposefully innocent to foster confidence.
UNC6229 has been seen misusing reputable commercial SaaS systems to distribute payloads and handle communications, which makes detection much more difficult.
After establishing confidence, the attackers go on to the payload distribution stage, delivering phishing URLs or malware-laden attachments that appear to be part of the employment process.
- Malware Delivery: A ZIP file known as a “skills test” or “job application form” is sent to victims. There is a Remote Access Trojan (RAT) within that can take complete control of the victim’s device once it is executed.
- Phishing Page: In other instances, candidates are sent to convincing interview scheduling websites that imitate Google or Microsoft’s branding. These phony websites can even get around multi-factor authentication (MFA) solutions like Okta by harvesting login credentials.
About The Author
Suraj Koli is a content specialist in technical writing about cybersecurity & information security. He has written many amazing articles related to cybersecurity concepts, with the latest trends in cyber awareness and ethical hacking. Find out more about “Him.”
Read More:
The “Infinite Money Glitch”: The Way a Well-Known ATM Hack Becomes a Federal Offense







