Maverick, WhatsApp Malware Target Brazil’s Biggest Banks by Hijacking Browser Sessions
“A WhatsApp Malware ‘Maverick’ is targeting Brazil’s Biggest Banks by hijacking browser sessions.”
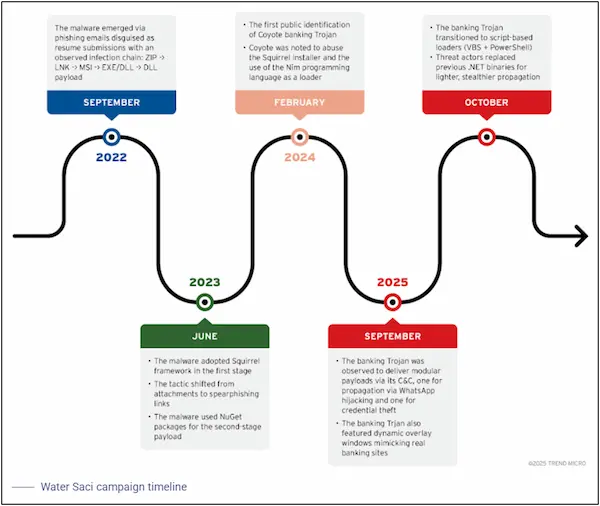
Threat hunters have seen parallels between a recently revealed harmful program called Maverick that has spread via WhatsApp and a banking trojan known as Coyote.
CyberProof, Report
| Both malware variants are built in .NET, target Brazilian banks and users, and have the same decryption and monitoring capabilities for banking URLs. More significantly, both have the capacity to propagate via WhatsApp Web. |
Trend Micro initially reported Maverick early last month, linking it to a threat actor known as Water Saci. There are two parts to the campaign: SORVEPOTEL is a self-propagating malware that spreads using WhatsApp’s desktop browser version and delivers a ZIP archive that contains the Maverick payload.

The malware’s purpose is to keep an eye on open browser tabs for URLs that correspond to a hard-coded list of Latin American financial institutions. If the URLs match, it connects to a distant server to retrieve more orders to collect system data and deliver phishing sites to obtain login credentials.
In a later investigation, cybersecurity company Sophos was the first to question whether Maverick is a development of Coyote and whether the behavior might be connected to previously documented operations that spread Coyote to users in Brazil. Maverick and Coyote did share a lot of code, according to another Kaspersky investigation, but it is being treated as a brand-new threat that targets Brazil collectively.
According to CyberProof’s most recent research, the ZIP package includes a Windows shortcut (LNK) that, when the user launches it, launches PowerShell or cmd.exe to connect to an external server (“zapgrande[.]com”) and download the first-stage payload. The PowerShell script can fetch a .NET loader and initiate intermediate tools intended to disable Microsoft Defender Antivirus and UAC.
For its part, the loader uses anti-analysis methods to detect the existence of reverse engineering tools and, in the event that they are discovered, self-terminate. The attack’s primary modules, SORVEPOTEL and Maverick, are subsequently downloaded by the loader. It’s important to note that Maverick is only installed after confirming that the victim is in Brazil by examining the infected host’s time zone, language, region, date, and time format.
Additionally, CyberProof reported that it discovered indications of the virus being used to target specific hotels in Brazil, suggesting a potential increase in targeting.
Water Saci’s new attack chain, which uses an email-based command-and-control (C2) infrastructure, multi-vector persistence for resilience, and a number of sophisticated checks to avoid detection, improve operational stealth, and limit execution to only Portuguese-language systems, was disclosed by Trend Micro.
CyberProof, Report, Last Month
| “Additionally, the new attack chain has an advanced remote command-and-control system that enables threat actors to monitor, pause, and resume the malware’s campaign in real-time. This effectively turns infected machines into a botnet tool for coordinated, dynamic operations across multiple endpoints.” |
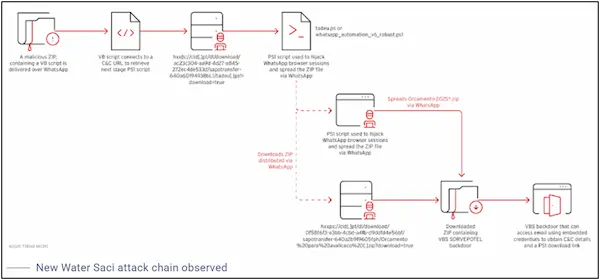
Instead of using .NET binaries, the infection sequence uses PowerShell and Visual Basic Script (VB Script) to take over WhatsApp browser sessions and distribute the ZIP file through the messaging app. The WhatsApp Web hijack is carried out by downloading ChromeDriver and Selenium for browser automation, just like the previous attack chain.
The assault begins when a user downloads and extracts the ZIP archive, which contains an obfuscated VBS downloader (“Orcamento.vbs” aka SORVEPOTEL). This downloader then issues a PowerShell command to download and run a PowerShell script (“tadeu.ps1”) directly in memory.
The victim’s WhatsApp Web session is taken over by this PowerShell script, which then distributes the malicious ZIP files to every contact connected to their account while disguising its nefarious objective with the “WhatsApp Automation v6.0” banner.
Additionally, the software exfiltrates contact lists and retrieves message templates by contacting a C2 server.
Trend Micro
| “The malware moves the victim’s valid Chrome profile data to its temporary workspace after ending any active Chrome processes and deleting previous sessions to guarantee clean functioning.”
“Cookies, authentication tokens, and the saved browser session are examples of this data.”
“By using this method, the malware can completely circumvent WhatsApp Web’s authentication and obtain instant access to the victim’s WhatsApp account without setting off security alerts or necessitating the scanning of QR codes.”
“According to Trend Micro, “the infection methods and ongoing tactical evolution, along with the region-focused targeting, indicate that Water Saci is likely linked to Coyote, and both campaigns operate within the same Brazilian cybercriminal ecosystem,” characterizing the attackers as aggressive in “quantity and quality.”
“When the Water Saci campaign is connected to Coyote, a larger picture emerges that shows a notable change in the banking trojan’s propagation strategies. Threat actors now use legitimate browser profiles and messaging services to launch covert, scalable attacks instead of depending on conventional payloads.” |
According to the cybersecurity firm, the virus also employs an advanced remote control mechanism that enables the attacker to stop, restart, and track the spread of WhatsApp in real time, transforming it into malware that can take over the infiltrated hosts like a bot.
In terms of how the ZIP archive is actually distributed, the PowerShell function iterates over each contact that has been harvested and looks for a pause command before sending customized messages by replacing variables in the message template with contact names and time-based greetings.
Another important feature of SORVEPOTEL is that, instead of utilizing a conventional HTTP-based communication method, it uses IMAP connections to terra.com[.]br email accounts using hardcoded email credentials to connect to the account and retrieve commands. Multi-factor authentication (MFA) has been used to protect some of these accounts from unwanted access.
Because the threat actor must manually enter a one-time authentication token for each login in order to access the mailbox and save the C2 server URL used to send the orders, this additional security layer is reported to have caused operational delays.
The C2 server is then periodically polled by the backdoor to retrieve the instruction. The following is a list of commands that are supported:
- INFO: to collect detailed system information
- CMD: to run a command via cmd.exe and export the results of the execution to a temporary file
- POWERSHELL: to run a PowerShell command
- SCREENSHOT: to take screenshots
- TASKLIST: to enumerate all running processes
- KILL: to terminate a specific process
- LIST_FILES: to enumerate files/folders
- DOWNLOAD_FILE: to download files from an infected system
- UPLOAD_FILE: to upload files to the infected system
- DELETE: to delete specific files/folders
- RENAME: to rename files/folders
- COPY: to copy files/folders
- MOVE: to move files/folders
- FILE_INFO: to get detailed metadata about a file
- SEARCH: to recursively search for files matching specified patterns
- CREATE_FOLDER: to create folders
- REBOOT: to initiate a system restart with a 30-second delay
- SHUTDOWN: to initiate a system shutdown with a 30-second delay
- UPDATE: to download and install an updated version of itself
- CHECK_EMAIL: to check the attacker-controlled email for new C2 URLs
With over 148 million active users, Brazil is the second-largest market in the world after India, which contributes to the campaign’s extensive reach.
About The Author
Suraj Koli is a content specialist in technical writing about cybersecurity & information security. He has written many amazing articles related to cybersecurity concepts, with the latest trends in cyber awareness and ethical hacking. Find out more about “Him
Read More:
The NSA is looking into a possible cyberattack that caused flights at Delhi Airport to stop