North Korean Hackers Use JSON Services to Disseminate Malware Covertly
North Korean Hackers Use JSON Services to Disseminate Malware Covertly
The Contagious Interview campaign’s North Korean threat actors have once again modified their strategies by staging malware payloads using JSON storage services.
According to a paper released on Thursday by NVISO experts Bart Parys, Stef Collart, and Efstratios Lontzetidis, “the threat actors have recently resorted to using JSON storage services like JSON Keeper, JSONsilo, and npoint.io to host and deliver malware from trojanized code projects, with the lure.”
Under the guise of conducting a job assessment or working together on a project, the campaign basically entails contacting potential targets on professional networking sites like LinkedIn and instructing them to download a demo project hosted on platforms like GitHub, GitLab, or Bitbucket.
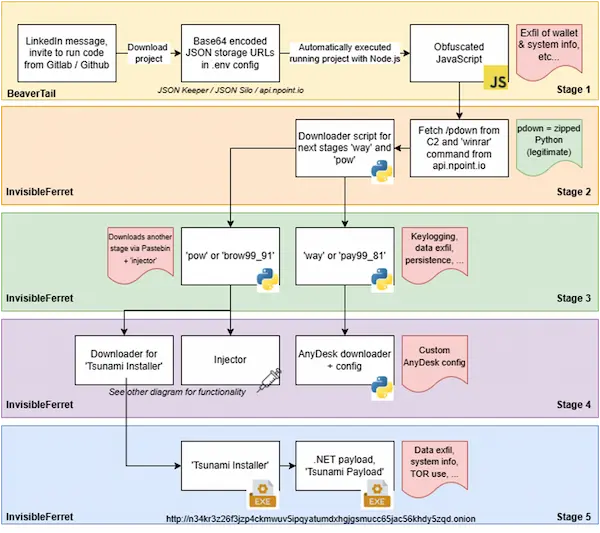
A file called “server/config/.config.env” in one such project that NVISO discovered has a Base64-encoded value that appears to be an API key but is actually a URL to a JSON storage service like JSON Keeper, where the next-stage payload is kept in an obfuscated format.
The payload is BeaverTail, a JavaScript virus that can gather private information and release InvisibleFerret, a Python backdoor. The backdoor’s behavior hasn’t changed much since Palo Alto Networks first revealed it in late 2023, but one significant modification is that it now retrieves an extra payload called TsunamiKit from Pastebin.
It’s important to note that in September 2025, ESET emphasized the use of TsunamiKit as part of the Contagious Interview campaign, which also dropped AkdoorTea and Tropidoor. The toolkit may gather data, perform system fingerprinting, and retrieve additional payloads from an offline hard-coded.onion address.
“It’s obvious that the actors behind the infectious Interview have not fallen back and are attempting to cast a very wide net to compromise any (software) developer that might seem intriguing to them, leading to exfiltration of sensitive data and crypto wallet information,” the investigators found.
“The usage of trustworthy sites such as JSON Keeper, JSON Silo, and npoint.io, along with code repositories including GitLab and GitHub, emphasizes the perpetrator’s intent and continuous attempts to operate stealthily and blend in with normal traffic.”
About The Author:
Yogesh Naager is a content marketer who specializes in the cybersecurity and B2B space. Besides writing for the News4Hackers blogs, he also writes for brands including Craw Security, Bytecode Security, and NASSCOM.
Read More:
Cheap Android Photo Frames Executing Silent Remote Attacks







