Screen-Sharing Trojan Leaked Private Chats on WhatsApp, Telegram, and Signal
“Let’s see how a screen-spying trojan really exposed private chats on social media apps!”
ThreatFabric researchers anticipated discovering another addition to the extensive list of banking trojans that steal passwords and trick users into fraudulent logins when they started monitoring a new outbreak of Android malware this autumn. Rather, they discovered something more ambitious.
According to researchers, the malware known as Sturnus is still in “development or limited testing.” However, even in this initial version, it gives remote operators incredibly broad access, ranging from device-level management to the capacity to gather private financial data.
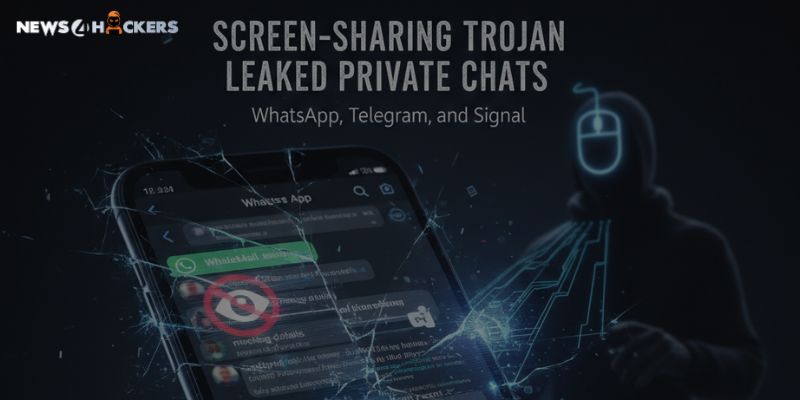
Researchers claim that what makes Sturnus unique is a feature that subtly compromises one of the most robust security measures in consumer technology: the encryption seen in apps like Signal, WhatsApp, and Telegram.
These systems have not been breached by the attackers, and no encryption has been compromised. Instead, Sturnus waits. It monitors. Additionally, the spyware copies communications in real time as soon as users decrypt them to view them on the screen.
Security Analyst, ThreatFabric
| “That is the issue with any gadget that has been compromised.”
“Even if your cryptography is flawless, the message is merely text once it appears on the screen.” |
The Screen as a Vulnerability in Secure Communication
For years, developers of encrypted messengers assured customers that forwarding could be turned off, screenshots could be limited, and messages could be made to vanish. However, the idea was only viable if the gadget itself continued to be trusted. With Sturnus, that assumption collapses.
According to ThreatFabric’s assessment, encryption would prevent the malware from intercepting network communications. Rather, it makes use of Android’s Accessibility Services, which is the same mechanism that makes it possible for people with disabilities to read everything that occurs on the screen.
Real-time logging of contacts, message histories, and conversation content circumvents the safeguards of end-to-end encrypted applications without actually crossing any cryptographic boundaries.
Aditya Sood, Vice President, Aryaka, Network Security Firm
| “It’s the traditional side-door attack.”
“The user’s secrets are visible if you can view their screen.”
The communication architecture of Sturnus makes detection more difficult. In order to blend in with the background noise of regular traffic, the virus communicates with its command-and-control server via a combination of plaintext, RSA, and AES-encrypted channels.
“It is far more difficult to examine Sturnus’ network traffic or retrieve the stuff it steals due to its complexity.” |
Beyond Customers: An Increasing Risk for Businesses
Sturnus may have ramifications for organizations, but the majority of malware strains that target mobile messaging apps mostly pose a threat to people.
Encrypted messengers are now used as unofficial backchannels for sharing sensitive or private information in a variety of industries, including defense and banking. Executives in the private sector are using them more and more to talk about transactions, corporate strategy, or compliance issues. They are essential for safe communication for journalists, activists, and lawyers.
Sood feels that Sturnus’s ability to record messages from these platforms “could spell serious problems for organizations,” particularly those that depend on encrypted apps as safeguards for internal operations. Even a single compromised device, he warned, can expose entire lines of critical communication.
Security researchers note that phony update prompts, such as phony “Google Chrome updates,” which encourage users to download malicious versions of trustworthy software, appear to play a role in the spread of Sturnus. The strategy is similar to the more general trend in mobile spyware, which is extremely dishonest but essentially straightforward social engineering.
Researcher
| “This has less to do with technical skill.”
“and more about taking advantage of the regular faith we have in our own screens.” |
CISA Warns of Spyware Targeting Messaging Applications
This week, the U.S. Cybersecurity and Infrastructure Security Agency (CISA), which now bills itself as “America’s Cyber Defense Agency,” released its own advice alerting users to the growing use of commercial spyware programs by cyber actors to infiltrate users of major messaging applications.
The agency’s warning echoes the dangers brought up by the most recent Trojan, even though it did not specifically mention Sturnus. The strategies mentioned are well-known but still successful:
- Malicious QR codes and phishing attempts are intended to link victim accounts to devices under the control of the attacker.
- Zero-click exploits don’t need the user to do anything.
- Techniques that impersonate reliable platforms like WhatsApp, Signal, and others.
CISA’s message is blunt: The best-practice safeguards are universal, but state-linked or high-end commercial spyware operators will never target most regular users. Check for unexpected alerts.
Steer clear of scanning unreliable QR codes. Don’t link too many devices. Any prompt that unexpectedly asks for authentication should be questioned. The alert presents a straightforward reality that is reflected in the Sturnus findings: encryption provides no protection if a device is compromised.
Researchers, ThreatFabric
| “As soon as the gadget is hacked.”
“The operator can see every sensitive interaction, and there is no longer any cryptographic security.” |
About The Author
Suraj Koli is a content specialist in technical writing about cybersecurity & information security. He has written many amazing articles related to cybersecurity concepts, with the latest trends in cyber awareness and ethical hacking. Find out more about “Him.”
Read More:
I4C Issues a Transnational Cybercrime Alert Regarding the WhatsApp Web Accounts Renting






