100+ Cisco Secure Email Devices are Vulnerable to Zero-Day Exploitation

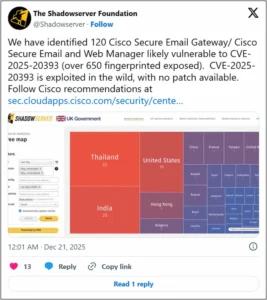
“Around 120 Cisco Secure Email Gateways and Cisco Secure Email were exposed to Zero-Day exploitation.”
At least 120 Cisco Secure Email Gateway and Cisco Secure Email and Web Manager devices have been found by security experts to be susceptible to a serious zero-day vulnerability that hackers are actively using in the wild.
There is currently no patch available for the issue, which is listed as CVE-2025-20393, leaving companies vulnerable to possible compromise.
Shadowserver Foundation, Threat Intelligence
| The susceptible devices are a portion of approximately 650 Cisco email security appliances that are fingerprinted and available online. |
For businesses that depend on these systems to screen malicious emails and shield their networks from phishing scams and malware spread, the discovery raises serious issues.
Cisco’s email security infrastructure, which businesses utilize to check incoming and outgoing email traffic for threats, is the target of CVE-2025-20393.
The confirmation of active exploitation shows that threat actors are already using this vulnerability to infiltrate affected systems, even though detailed technical information regarding the exploitation mechanism is still restricted to avoid broad abuse.
Cisco has acknowledged the vulnerability and issued security advice advising companies to take quick precautions.
Until a long-term solution is found, the networking behemoth advises impacted clients to examine their security settings and implement temporary mitigations. Cisco’s Security Advisory platform provides organizations with comprehensive assistance.
The incident serves as a reminder of the continuous difficulties businesses encounter with zero-day vulnerabilities, especially in crucial infrastructure elements like email gateways.
These devices handle sensitive messages and act as the main line of protection against email-borne attacks, placing them at a critical intersection in enterprise networks. Attackers may be able to install ransomware, eavesdrop on private messages, or create long-term network access if the compromise is successful.
Reviewing the alert and putting the suggested remedies into practice right away should be the top priority for security teams overseeing Cisco Secure Email Gateway and Web Manager implementations.
Additionally, companies should keep an eye out for unusual activity on their systems and think about temporarily limiting external access to these devices until patches are made available.
Interim precautions are crucial for reducing exposure to this actively exploited vulnerability because the vendor has not given a schedule for the deployment of a security fix.
About The Author
Suraj Koli is a content specialist in technical writing about cybersecurity & information security. He has written many amazing articles related to cybersecurity concepts, with the latest trends in cyber awareness and ethical hacking. Find out more about “Him.”
Read More:
Christmas 2025: A Warning About Phishing Messages, AI-Driven Scams, and Fake Offers