“ClickFix” Trap: Qilin Ransomware Infection Caused by False Human Verification
“ClickFix” Trap: Qilin Ransomware Infection Caused by False Human Verification
Researchers have discovered a direct connection between the infamous Qilin ransomware organization and “ClickFix,” a dishonest social engineering technique that has developed into a gateway for significant ransomware attacks. The Counter Threat Unit (CTU) research team recently released a paper that describes how a straightforward surfing error turned into a widespread network penetration involving several malware families and stolen VPN credentials.
The “ClickFix” strategy takes advantage of a user’s conditioning to bypass security checks. The method “essentially relies on a victim following a series of instructions that masquerade as a human verification request,” according to the report.
A Qilin ransom note
The investigation started when a user went to aquafestonline[.]com, a legitimate yet hacked website. A malicious script that retrieved a deeply obfuscated JavaScript file from an external source was concealed within the website.
The purpose of this script was to be selective. In order to “limit attacks on the system to one per 24-hour period,” it even generates a unique tracking string and “fingerprints the user’s operating system and browser type.”
The script produced a phony “ClickFix” verification page when it was activated. By downloading a batch file that installed NetSupport Manager, a legal remote administration tool that is frequently abused by attackers, victims who followed the instructions to “verify” themselves were not demonstrating their humanity.
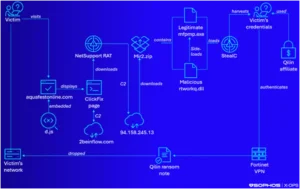
Infection chain resulting in Qilin ransomware deployment | Image: Sophos
The attackers changed course after establishing the NetSupport Remote Access Trojan (RAT). After establishing a connection with a command-and-control server, the RAT downloaded a ZIP file that included an authentic Microsoft executable (mfpmp.exe). A malicious DLL was sideloaded using this program, which led to an infection with StealC V2, a powerful information stealer that was launched in March 2025.
Regarding StealC V2, the researchers observed that “the updated version offered significant upgrades in terms of stealth and versatility.”
About a month later, the last blow was delivered. Threat actors used a Fortinet VPN account to access the victim’s network using credentials that were probably stolen by StealC. The Qilin ransomware notes (README-RECOVER-ID) quickly spread throughout the network.
“Analysis showed that the threat actor used a privileged account on a Fortinet VPN device to access the network using credentials they had stolen.”
The GOLD FEATHER threat group’s Qilin engagement emphasizes how serious the effort is. According to reports, Qilin was the “most prevalent ransomware-as-a-service (RaaS) operation between January 2024 and December 17, 2025,” with 1,168 victims during that time.

The organization uses a “double-extortion model,” encrypting the victim’s computers while obtaining confidential information to use as leverage.
The CTU team advises businesses to concentrate on “patching vulnerable internet-facing devices” and making sure that services like RDP aren’t made public unless absolutely necessary.
Most crucially, identity security can prevent a ransomware distribution by blocking the path from a stolen credential. To stop initial access brokers from selling a way in, the paper suggests “robustly implementing phishing-resistant multi-factor authentication (MFA) across the network.”
About The Author:
Yogesh Naager is a content marketer who specializes in the cybersecurity and B2B space. Besides writing for the News4Hackers blogs, he also writes for brands including Craw Security, Bytecode Security, and NASSCOM.
Read More:
npm Data Leak: Fake WhatsApp API Package Steals SMS, Contacts, & Login Tokens