Recently, Malicious Chrome Extensions Victimized 900K Users Over ChatGPT & DeepSeek
“Nowadays, 2 Malicious Chrome Extensions have compromised 900k+ users by stealing their conversions.”
Over 900,000 users have been affected by two malicious Chrome extensions that covertly transfer complete browser histories and conversations from ChatGPT and DeepSeek to attacker servers.
OX Security Researchers, OX Research Team
| The spyware mimics the genuine AITOPIA AI sidebar tool; one of the fakes even received Google’s “Featured” label.
Extensions that replicate AITOPIA’s chat interface for LLMs like GPT and Claude are revealed during normal analysis. |
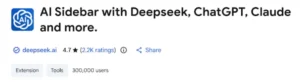
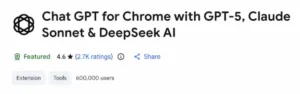
They ask for “anonymous analytics” permission to conceal data theft under the names “Chat GPT for Chrome with GPT-5, Claude Sonnet & DeepSeek AI” (600K+ users, ID: fnmihdojmnkclgjpcoonokmkhjpjechg, version 1.9.6) and “AI Sidebar with Deepseek, ChatGPT, Claude and more” (300K+ users, ID: inhcgfpbfdjbjogdfjbclgolkmhnooop).
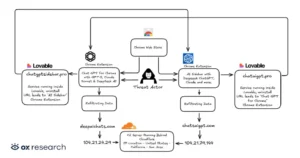
Uninstalled extensions reroute to the other, and threat actors host privacy policies on Lovable.dev to hide origins.
How Does the Malware Work?
By using the chrome.tabs.onUpdated API to monitor tabs, installed extensions create a distinct “gptChatId” for each victim. They scrape DOM elements for prompts, responses, and session IDs after identifying chatgpt.com or deepseek.com URLs.
They save data locally prior to Base64-encoding and send batches to C2 servers like deepaichats.com or chatsaigpt.com every 30 minutes.
This records PII, proprietary code, business plans, search queries, and internal URLs that AITOPIA’s stated server storage missed.
Stolen conversations put personal information, company secrets, and intellectual property at risk of being sold on dark web forums or used for espionage. Phishing and identity theft are made possible throughout impacted companies by browsing records that disclose patterns, tokens, and organizational hierarchies.
Both extensions are still available for download as of January 7, 2026; the first was updated as recently as October 2025 but lost its “Featured” status after disclosure.
Users can use the ChatGPT extension, AI Sidebar, or remove it by ID by going to chrome://extensions. Regardless of badges, stay away from unconfirmed extensions and only use reliable sources.
IoCs
| Type | Value | Notes |
| Extension Name | Chat GPT for Chrome with GPT-5, Claude Sonnet & DeepSeek AI | Malicious AI sidebar-style extension |
| Extension ID | fnmihdojmnkclgjpcoonokmkhjpjechg | Chrome Web Store ID |
| Version | 1.9.6 | Reported a malicious build |
| SHA-256 Hash | 98d1f151872c27d0abae3887f7d6cb6e4ce29e99ad827cb077e1232bc4a69c00 | Package hash |
| Extension Name | AI Sidebar with Deepseek, ChatGPT, Claude, and more | Second malicious extension |
| Extension ID | inhcgfpbfdjbjogdfjbclgolkmhnooop | Chrome Web Store ID |
| Version | 1.6.1 | Reported a malicious build |
| SHA-256 hash | 20ba72e91d7685926c8c1c5b4646616fa9d769e32c1bc4e9f15dddaf3429cea7 | Package hash |
Network and C2 IoCs
| Category | Domain/ Endpoint | Notes |
| C2 endpoint | deepaichats[.]com | Receives stolen chat data and URLs |
| C2 endpoint | chatsaigpt[.]com | Additional C2 for exfiltrated data |
| Lovable-Hosted Server | chataigpt[.]pro | Used for privacy policy/ infra hosting |
| Lovable-Hosted Server | chatgptsidebar[.]pro | Used for uninstall redirect and infra |
About The Author
Suraj Koli is a content specialist in technical writing about cybersecurity & information security. He has written many amazing articles related to cybersecurity concepts, with the latest trends in cyber awareness and ethical hacking. Find out more about “Him.”
Read More:
Discord Accounts Hit by VVS Stealer Malware via Obfuscated Python Code