AI is Used by New Android Malware to Click on Disguised Web Advertisements
AI is Used by New Android Malware to Click on Disguised Web Advertisements
TensorFlow machine learning models are used by a new family of Android click-fraud trojans to automatically identify and engage with particular ad elements.

Unlike traditional click-fraud trojans, which use script-based DOM-level interaction, the method focuses on visual analysis based on machine learning rather than predefined JavaScript click routines.
The threat actor is utilizing TensorFlow.js, an open-source JavaScript machine learning model training and deployment library created by Google. It makes it possible to execute AI models on Node.js servers or in browsers.
The new family of Android trojans is disseminated via GetApps, the official app store for Xiaomi devices, according to researchers from mobile security firm Dr.Web.
They found that the virus can function in a mode known as “phantom,” which loads a JavaScript file and a target page for click-fraud using a hidden WebView-based embedded browser. Automating actions on the advertisements displayed on the loaded website is the goal of the script.
The concealed browser is positioned on a virtual screen after the trained model has been loaded from a distant server, and screenshots are collected so that TensorFlow.js can examine and identify pertinent information.
The malware replicates a user’s typical actions by tapping on the appropriate UI element. Since most of these advertisements are dynamic, constantly changing their structure, and frequently include iframes or video, this approach is more successful and resistant to the variety of modern commercials.
In a second mode known as “signalling,” the attackers can conduct real-time activities like tapping, scrolling, and text entry by using WebRTC to send a live video feed of the virtual browser screen to them.
The threat actor uses games from Xiaomi’s GetApps software portfolio to spread the infection. The harmful components are added to the apps in later versions after they are first submitted without any malicious functionality.
Among the games that Doctor Web found to be compromised are:
| Theft Auto Mafia | 61,000 downloads |
| Cute Pet House | 34,000 downloads |
| Creation Magic World | 32,000 downloads |
| Amazing Unicorn Party | 13,000 downloads |
| Open World Gangsters | 11,000 downloads |
| Sakura Dream Academy | 4,000 downloads |
One of the malicious apps on Xiaomi’s app store
Source: Doctor Web
The trojans are disseminated through third-party APK websites (such as Apkmody and Moddroid, modified versions, the so-called mods, of the original Spotify, YouTube, Deezer, and Netflix apps) in addition to the Xiaomi-hosted apps.
The majority of the apps on Moddroid’s “Editor’s Choice” page, according to the researchers, are compromised.
Spotify Pro, Spotify Plus – Official, Moddroid.com, and Apkmody Chat are a few instances of apps that spread infected APK files over Telegram channels.
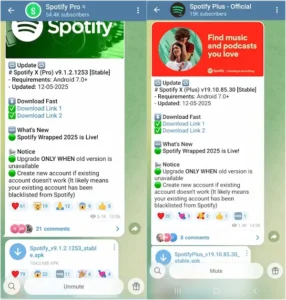
Click-fraud trojans on Telegram
Source: Doctor Web
Additionally, Dr.Web discovered a Discord channel with 24,000 members promoting the compromised Spotify X app.
At least some of these apps “actually work,” according to the study, which lessens consumers’ mistrust. The victims won’t be able to detect the malicious activity because click fraud is carried out secretly in a concealed WebView that displays content on a virtual screen.
Clickjacking and ad fraud are profitable cybercrimes even if they don’t immediately endanger consumer privacy and data. Battery depletion and early deterioration, as well as higher mobile data fees, directly affect the user.
It is recommended that Android users refrain from installing apps from sources other than Google Play, particularly versions of well-known apps that offer free access to premium subscriptions or additional features.
About The Author:
Yogesh Naager is a content marketer who specializes in the cybersecurity and B2B space. Besides writing for the News4Hackers blogs, he also writes for brands including Craw Security, Bytecode Security, and NASSCOM.