A Tax Phishing Campaign Targets Indian Users, Blackmoon Malware Delivery
A Tax Phishing Campaign Targets Indian Users, Blackmoon Malware Delivery
As part of a suspected cyber espionage campaign, cybersecurity researchers have found an ongoing campaign that targets Indian consumers with a multi-stage backdoor.
According to the eSentire Threat Response Unit (TRU), the activity entails tricking victims into downloading a malicious archive through phishing emails posing as the Income Tax Department of India. This gives the threat actors permanent access to the victims’ computers for ongoing monitoring and data exfiltration.
The complex attack’s ultimate objective is to use a genuine enterprise solution called SyncFuture TSM (Terminal Security Management), created by the Chinese company Nanjing Zhongke Huasai Technology Co., Ltd., and a variation of the well-known banking trojan Blackmoon (also known as KRBanker). No known threat actor or group has been linked to the initiative.
“While marketed as a legitimate enterprise tool, it is repurposed in this campaign as a powerful, all-in-one espionage framework,” claimed eSentire. “By deploying this system as their final payload, the threat actors establish resilient persistence and gain a rich feature set to monitor victim activity and centrally manage the theft of sensitive information.”
With the exception of an executable (“Inspection Document Review.exe”) that is used to sideload a malicious DLL contained in the archive, all five of the files in the ZIP file transmitted by the phony tax penalty notices are hidden. For its part, the DLL contacts an external server to retrieve the next-stage payload and performs tests to identify delays caused by the debugger.
The downloaded shellcode subsequently obtains administrative access by circumventing the User Account Control (UAC) prompt using a COM-based method. In order to evade detection, it additionally alters its own Process Environment Block (PEB) to look like the authentic Windows “explorer.exe” process.
Additionally, it obtains the subsequent stage “180.exe” from the “eaxwwyr[.]cn” domain. This 32-bit Inno Setup installer modifies its actions according on whether the compromised host is running the Avast Free Antivirus process (“AvastUI.exe”).
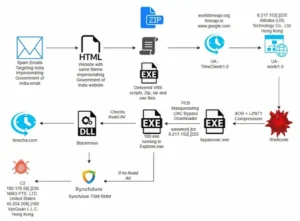
In order to avoid detection, the malware uses automatic mouse simulation to navigate Avast’s interface and add harmful files to its exclusion list without turning off the antivirus engine. This is accomplished by using a DLL that is thought to be a member of the Blackmoon virus family, which is notorious for attacking companies in the United States, Canada, and South Korea. September 2015 was when it first appeared.
A program called “Setup.exe,” a tool from SyncFutureTec Company Limited that is intended to write “mysetup.exe” to disk, has been added to the exclusion list. SyncFuture TSM, a commercial solution with remote monitoring and management (RMM) features, is evaluated as the latter.
The campaign’s threat actors can remotely control compromised endpoints, log user activity, and exfiltrate relevant data by misusing a legitimate offering. Other files are also deployed when the executable is executed:
- Batch scripts that make unique directories and change their Access Control Lists (ACLs) so that every user has access
- Batch programs that change the desktop folder user permissions
- Cleanup and restoration tasks are carried out via a batch script.
- A program named “MANC.exe” that allows for extensive logging and orchestrates several services
“It offers them the tools to not only steal data but to maintain granular control over the compromised environment, track user activity in real-time, and ensure their own persistence,” stated eSentire. “By blending anti‑analysis, privilege escalation, DLL sideloading, commercial‑tool repurposing, and security‑software evasion, the threat actor demonstrates both capability and intent.”
PhishNext — Your Companion for World-Class Phishing Simulation Services in Delhi NCR
You definitely need a partner who can do everything for you if you want to identify all the weak points in your workforce that lack cyber knowledge and could be a whistleblower about the security parameters of the relevant IT infrastructure of your company! In this regard, we offer you PhishNext by Craw Security, a real Phishing Simulation Service that can identify the vulnerabilities in your personnel network that could serve as a point of entry for all malware and Trojan viruses started by a malevolent threat actor seeking to gain access to your IT system.
Craw Security’s PhishNext employs a range of techniques, including numerous proactive Phishing Simulation Services and pre-recorded video sessions for those who fall for the scam, click on the phishing emails, and download the malware-containing files in real time.

In this sense, Craw Security, the top provider of phishing services in Delhi NCR, offers a number of essential components in its top-notch PhishNext, the Best Phishing Simulation Service in India, including the following:
| Realistic Approach Domains | PhishNext uses nearly identical names of popular websites to offer a similar approach to the receivers of the emails, making them smell a little less suspicious than other phishing emails while still appearing more authentic and clickable. |
| Similar Templates | Many of the templates we have are identical in appearance and are sourced from reputable companies like Amazon, Flipkart, SBI, ICICI, Myntra, MakeMyTrip, GoIbibo, and many more. |
| Detailed Analytics | In order to help our clients identify the weak points in their human resource chain, we provide them with thorough reports that contain actionable insight, such as click rates, credential submissions, and risk assessment indicators. |
| Integrated Training | Employees who experience simulated attacks are automatically enrolled in security awareness training. |
PhishNext, the best-in-class Phishing Simulation Service in Delhi NCR from the House of Craw Security, the Top-Notch VAPT Solutions Provider in Delhi, is an option for individuals or enterprises looking to purchase the best phishing simulation solutions in Delhi NCR. Please visit the Official Website of Craw Security for additional information, or call our 24-hour hotline at +91-9513805401 to speak with one of our top phishing experts.
About The Author:
Yogesh Naager is a content marketer who specializes in the cybersecurity and B2B space. Besides writing for the News4Hackers blogs, he also writes for brands including Craw Security, Bytecode Security, and NASSCOM.
Read More:
ShinyHunters Revives Leak Site Leads to Crunchbase Confirming Data Breach