Advanced Linux VoidLink Malware Attacks Cloud and Container Environments

“Recently, a new advanced Linux VoidLink Malware is attacking cloud and container environments.”
A feature-rich malware architecture known as VoidLink, which was created especially for long-term, covert access to Linux-based cloud systems, has been revealed by cybersecurity researchers.
Check Point Research, New Report
| With the use of a variety of custom loaders, implants, rootkits, and modular plugins, the cloud-native Linux malware framework’s operators can modify its capabilities over time and alter course as goals change. In December 2025, it was initially found.
“The framework is designed to function dependably in cloud and container environments for extended periods of time, and it has several cloud-focused features and modules.” “Based on a unique Plugin API that seems to have been influenced by Cobalt Strike’s Beacon Object Files (BOF) methodology, VoidLink’s architecture is incredibly adaptable and highly modular. By default, over 30 plug-in modules use this API.” |
The results show that threat actors are shifting their attention from Windows to Linux systems, which have become the foundation of cloud services and vital operations. It is believed that China-affiliated threat actors are responsible for the active maintenance and evolution of VoidLink.
The toolkit, a cloud-first implant written in the Zig programming language, can identify major cloud environments, such as Amazon Web Services (AWS), Google Cloud, Microsoft Azure, Alibaba, and Tencent, and modify its behavior if it detects that it is operating inside a Docker container or a Kubernetes pod.
Additionally, it can collect credentials related to cloud environments and well-known source code version control systems like Git.
The fact that these services are being targeted suggests that VoidLink is probably designed to target software developers, either with the intention of stealing confidential information or using the access to launch supply chain attacks.
The following is a list of some of its other capabilities:
- LD_PRELOAD, loadable kernel module (LKM), and eBPF are rootkit-like characteristics that conceal their processes according to the Linux kernel version.
- A system of in-memory plugins to increase functionality.
- Several command-and-control (C2) channels, including HTTP/HTTPS, WebSocket, ICMP, and DNS tunneling, are supported.
- Create a mesh-style or peer-to-peer (P2P) network across infected hosts.
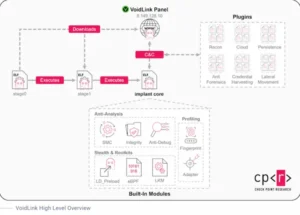
A Chinese web-based dashboard that enables the attackers to perform various stages of the attack cycle, from reconnaissance and persistence to lateral movement and defense evasion by erasing traces of malicious activity, as well as remotely control the implant, create custom versions on the fly, and manage files, tasks, and plugins.
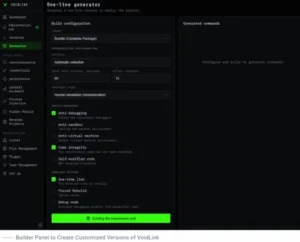
VoidLink is a complete post-exploitation framework thanks to its 37 plugins, which include anti-forensics, reconnaissance, containers, privilege escalation, lateral movement, and more.
- Anti-forensics, timestomping files to obstruct analysis, and wiping or editing shell history and logs depending on keywords.
- Cloud, to enable container escapes, privilege-escalation, Kubernetes and Docker discovery, and misconfiguration probes.
- Credential harvesting is the process of gathering credentials and secrets, such as SSH keys, git credentials, local password content, browser credentials and cookies, tokens, and API keys.
- Lateral movement: to use an SSH-based worm to spread laterally.
- Persistence can be established by system services, cron jobs, and misuse of dynamic linkers.
- Recon, to collect comprehensive knowledge about the surroundings and system.
Check Point described VoidLink as “impressive” and “far more advanced than typical Linux malware,” noting that it has a core orchestrator component that manages task execution and C2 connections.
In order to avoid detection, it also has a variety of anti-analysis measures. In addition to alerting different debuggers and monitoring tools, it has the ability to erase itself if any indications of manipulation are found.
Additionally, it has a self-modifying code option that circumvents runtime memory scanners by decrypting protected code portions during runtime and encrypting them when not in use.
Additionally, the malware framework counts the installed security products and hardening measures on the compromised host to determine an overall evasion strategy and calculate a risk score. For instance, this may entail having more control in high-risk situations and slowing down port checks.

Check Point Research
| “With a strong command of several programming languages, including Go, Zig, C, and contemporary frameworks like React, the developers exhibit a high degree of technical proficiency.”
“Furthermore, the attacker’s deep understanding of intricate operating system internals allows for the creation of clever and intricate solutions.” “VoidLink profiles an area and determines the best course of action to take to automate evasion as much as feasible. VoidLink’s operators can navigate cloud environments and container ecosystems with adaptive stealth thanks to its extensive plugin ecosystem and kernel-mode tradecraft.” |
About The Author
Suraj Koli is a content specialist in technical writing about cybersecurity & information security. He has written many amazing articles related to cybersecurity concepts, with the latest trends in cyber awareness and ethical hacking. Find out more about “Him.”
Read More:
n8n Supply Chain Attack Steals OAuth Tokens by Abusing Community Nodes