Bug Bounty’s Maximum Limit is Doubled by Apple to $2M for zero-click RCEs

“Apple doubled rewards for zero-click RCEs by increasing bug bounties to $2 million. It has given $ 35 million to 800 researchers since 2020.”
Apple has raised its bug bounty payouts, with up to $2 million now available for bugs involving zero-click remote code execution. The tech behemoth has paid 800 researchers $35 million since 2020.
Apple wants to compensate exploit chains on par with commercial spyware providers and mercenary groups. The business disclosed that bonuses (beta bugs, bypassing Lockdown Mode) can increase compensation to above $5 million.
Apple increased the scope of its bug reward to include more attack surfaces, including up to $1 million for wireless proximity vulnerabilities and $300K for one-click WebKit sandbox escapes. Additionally, it provided Target Flags, which allow researchers to demonstrate exploitability for popular categories such as RCE and TCC bypasses and, once validated, obtain speedier rewards.

In an effort to promote more study into this crucial security measure, Apple is offering a $100,000 reward for a comprehensive, user-free Gatekeeper bypass on macOS.
Apple
| “Our top prize is being doubled to $2 million for exploit chains that can accomplish objectives comparable to those of highly skilled mercenary spyware attacks.”
“Our bonus system, which offers extra rewards for Lockdown Mode bypasses and vulnerabilities found in beta software, can more than double this reward, with a maximum payout of more than $5 million. This is the largest payout offered by any bounty program that we are aware of and an industry first.”
“We will compare all new reports to both the old and new frameworks until the revised awards are posted online, at which point we will give the larger sum. And even though we’re particularly encouraged to receive creative research and intricate exploit chains, we’ll keep reviewing and rewarding any reports that have a major influence on user security, even if they don’t fall under one of our published categories.”
“We’re excited to keep collaborating with you to protect our users!” |
To strengthen defenses, Apple’s Security Engineering and Architecture (SEAR) team investigates intricate exploit chains akin to those of mercenary spyware. The Security Bounty now gives greater payouts for five important attack vectors to encourage more in-depth, offensive research and increases rewards to encourage researchers to discover multi-step, cross-border attacks:
| Current Maximum | New Maximum | |
| Zero-click chain: Remote attack with no user interaction | $1M | $2M |
| One-click chain: Remote attack with one-click user interaction | $250K | $1M |
| Wireless proximity attack: Attack requiring physical proximity to the device | $250K | $1M |
| Physical device access: An Attack requiring physical access to a locked device | $250K | $500K |
| App sandbox escape: Attack from the app sandbox to SPTM bypass | $150K | $500K |
High payments for exploit chains that mimic real-world, complex assaults on modern hardware and software and make use of target flags are given priority by the company.
Researchers can demonstrate exploit capabilities like code execution or memory control with Apple’s new Target Flags. Target Flags are integrated into Apple operating systems to improve efficiency and trust by allowing the business to automatically validate results and provide quicker, clearer bounty rewards even before updates are made available.
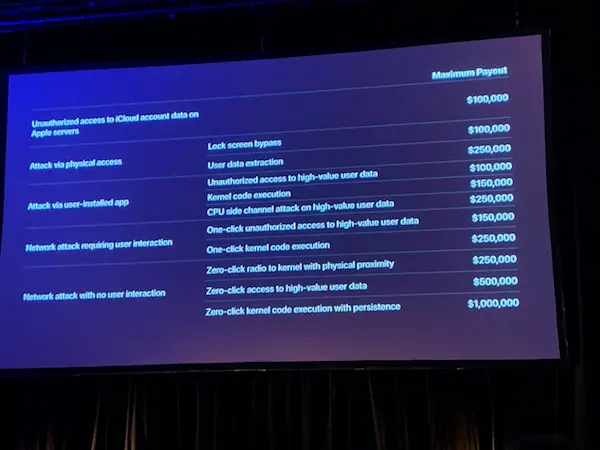
In order to increase remote-entry payouts and decrease benefits for less realistic vectors, rewards are based on demonstrated impact (outcome). The business points out that unrelated or isolated components are nonetheless acceptable, albeit in smaller quantities.
With its latest smartphones featuring C1/C1X and N1 processors, Apple expanded coverage to all radio interfaces, doubling its wireless proximity incentive to $1 million.
Issues affecting the newest devices and operating systems, such as the iPhone 17 with Memory Integrity Enforcement, are given priority in reward standards. Bonuses are awarded for outstanding research in beta releases or avoiding Lockdown Mode.

$1,000 rewards are now given for low-impact reports. In order to defend civil society from mercenary malware, Apple plans to donate 1,000 iPhone 17 devices to them by 2026. Additionally, Apple plans to expand its Security Research Device Program to include iPhone 17 devices, offering priority bounty consideration to discoveries made on these devices.
About The Author
Suraj Koli is a content specialist in technical writing about cybersecurity & information security. He has written many amazing articles related to cybersecurity concepts, with the latest trends in cyber awareness and ethical hacking. Find out more about “Him.”
Read More:
Chinese Hackers Exploit ‘Nezha’ Tool to Pry on Asian Companies








