Chinese Hackers RedNovember Use Cobalt Strike and Pantegana to Target Governments Across the World
Chinese Hackers RedNovember Use Cobalt Strike and Pantegana to Target Governments Across the World
A Chinese state-sponsored threat actor has been identified as the source of a suspected cyber espionage activity cluster that was previously discovered to target international government and commercial sector organizations in Africa, Asia, North America, South America, and Oceania.

After monitoring the activities under the name TAG-100, Recorded Future has now promoted it to the hacker collective RedNovember. Microsoft also tracks it under the name Storm-2077.
The Mastercard-owned company said in a report shared with News4Hackers that “between June 2024 and July 2025, RedNovember (which overlaps with Storm-2077) targeted perimeter appliances of high-profile organizations globally and used the Go-based backdoor Pantegana and Cobalt Strike as part of its intrusions.”
“The organization has broadened its targeting remit across government and private sector organizations, encompassing defense and aerospace entities, space groups, and law firms.”
A Southeast Asian government, a European government directorate, a state security body in Africa, and a ministry of foreign affairs in Central Asia are some of the most likely new victims of the threat actor. A European engine maker, a trade-focused intergovernmental cooperation body in Southeast Asia, and at least two U.S. defense contractors are also thought to have been compromised by the group.
Over a year ago, Recorded Future published the first documentation of RedNovember, which described how it used the Pantegana post-exploitation framework and Spark RAT after weaponizing known security
flaws in a number of internet-facing perimeter appliances from Cisco, Citrix, F5, Fortinet, Ivanti, Palo Alto Networks (CVE-2024-3400), Check Point (CVE-2024-24919), and SonicWall for initial access.

Targeting security solutions like load balancers, firewalls, VPNs, virtualization infrastructure, and email servers is a trend that other Chinese state-sponsored hacking groups have been using more and more to gain access to networks of interest and stay persistent for long stretches of time
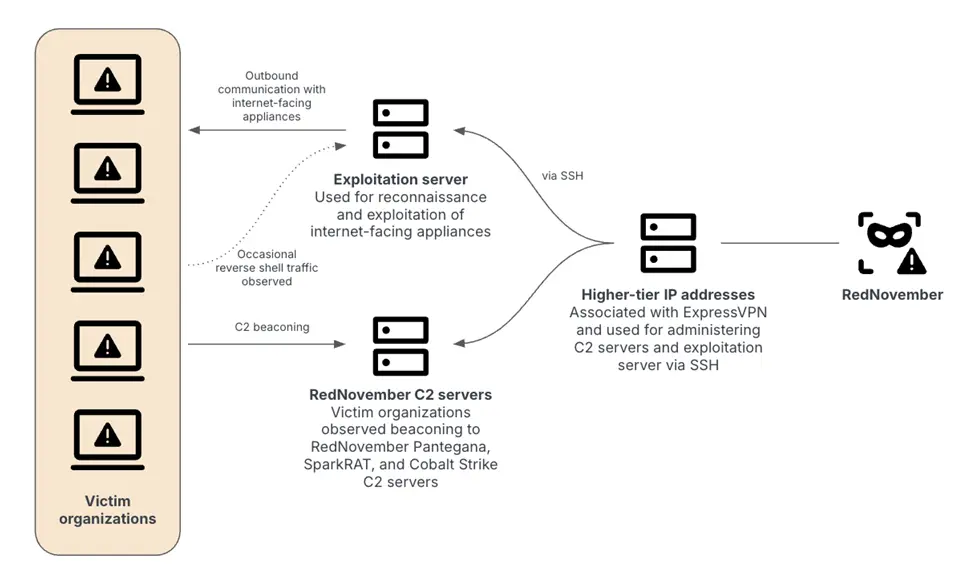
The usage of open-source tools Spark RAT and Pantegana is a notable component of the threat actor’s tradecraft. The adoption is probably a move by espionage actors to repurpose current programs to their benefit and muddle attribution efforts.
Additionally, the assaults use a version of the open-source Go-based loader LESLIELOADER to install Cobalt Strike Beacons or Spark RAT on compromised devices.
In order to manage and connect to two sets of servers used for the exploitation of internet-facing devices and to communicate with Pantegana, Spark RAT, and Cobalt Strike—another legitimate program that has been extensively misused by malicious actors—RedNovember is alleged to use VPN services such as ExpressVPN and Warp VPN.

The hacker gang has concentrated most of its targeted efforts on South Korea, Taiwan, the United States, and Panama between June 2024 and May 2025. It has been discovered to target Ivanti Connect Secure appliances connected to a U.S.-based newspaper and an engineering and military contractor as recently as April 2025.
Prior to a South American nation’s state visit to China, Recorded Future said it also identified the adversary that was probably targeting the nation’s Microsoft Outlook Web Access (OWA) portals.
“RedNovember has historically targeted a diverse range of countries and sectors, suggesting broad and changing intelligence requirements,” the business stated. “RedNovember’s activity to date has primarily focused on several key geographies, including the U.S., Southeast Asia, the Pacific region, and South America.”
About The Author:
Yogesh Naager is a content marketer who specializes in the cybersecurity and B2B space. Besides writing for the News4Hackers blogs, he also writes for brands including Craw Security, Bytecode Security, and NASSCOM.
Read More:
MalTerminal Malware Changes GPT-4 Into a Ransomware Manufacturing Unit








