Chrome Extensions that Steal Credentials Target Corporate HR Systems

It was found that malicious Chrome extensions on the Chrome Web Store were collecting authentication credentials or blocking management sites required to address security problems while posing as productivity and security applications for enterprise HR and ERP platforms.
Cybersecurity company Socket made the effort and claims to have found five Chrome extensions that were installed more than 2,300 times and targeted Workday, NetSuite, and SAP SuccessFactors.
According to Socket, “the campaign uses three different attack types: bidirectional cookie injection for direct session hijacking, DOM manipulation to prevent security management sites, and cookie exfiltration to distant servers.”
“The extensions target the same enterprise platforms and share identical security tool detection lists, API endpoint patterns, and code structures, indicating a coordinated operation despite appearing as separate publishers.”
Although the extensions were released under different names, the researchers claim that their architecture, coding patterns, and targeting are the same. While the fifth extension utilized a different branding under the moniker Software Access, the other four were released under the developer name databycloud1104.
Although about 2,300 people were impacted by the extensions, widespread ransomware and data theft assaults could be fueled by the theft of organizational credentials.
Demonstrated as Tools for Corporate Users
According to Socket, the extensions were marketed to customers of large HR and ERP systems, portraying themselves as instruments intended to boost security, increase productivity, or simplify procedures.
A number of the extensions purported to provide easier access to “premium tools” for various platforms, including Workday and NetSuite.
Data By Cloud 2, one of the more well-liked extensions, was installed 1,000 times and marketed as a dashboard that provided bulk management features and quicker access for customers overseeing numerous business accounts.
Tool Access 11, another extension, marketed itself as a security-focused add-on that would limit access to critical administrative functions. According to its listing, the extension might restrict user activities using “special tools” in order to guard against account compromise.

Similar language about granting “access” to tools and services was used by other extensions in the group, demanding rights that seemed to be in line with enterprise integrations.
Nevertheless, according to Socket, none of the extensions revealed the blocking of security management sites, cookie extraction, or credential exfiltration. Additionally, the extensions’ privacy policies made no mention of the collection of user data.
The extensions employed a variety of malicious techniques, such as session hijacking by cookie injection, administrator page blocking, and authentication cookie exfiltration, according to Socket’s examination of the extensions.
The “__session” authentication cookies for a targeted domain, which hold active login tokens for Workday, NetSuite, and SuccessFactors, were continuously collected by several extensions.
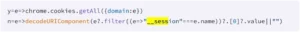
Stealing “__session” cookies
Source: Socket
Attackers were able to keep access even when users checked out and back in because these tokens were exfiltrated to distant command-and-control servers every 60 seconds.
Workday’s security and issue response pages were inaccessible due to two extensions, Tool Access 11 and Data By Cloud 2. The extensions either diverted administrators from management pages or removed information from the pages using page title detection.
“According to Socket, Tool Access 11 targets 44 administration pages, such as session restrictions, IP range management, security proxy settings, and authentication policies.”
“By including password management, account deactivation, 2FA device restrictions, and security audit logs, Data By Cloud 2 increases this to 56 pages.”
If a security incident is discovered, blocking access to certain pages can make it impossible for authorized administrators to address it.
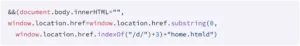
Tool Access 11 is blocking access to security management pages
Source: Socket
Lastly, Socket claims that by adding a capability that permits bidirectional cookie modification, the Software Access extension implemented the most harmful behavior. The extension might obtain stolen cookies from the attacker’s server and inject them straight into a browser in addition to obtaining session tokens.
The researchers claim that the attackers may take over authenticated sessions without inputting usernames, passwords, or multi-factor authentication codes by using the C2 to set authentication cookies. According to Socket, this made it possible to take over accounts instantly on the targeted enterprise platforms.
According to Socket, they reported the extensions to Google, and as of the time this post was published, they seem to have been removed.
Anyone utilizing these extensions should update their passwords on the targeted platforms and report them to their security administrators for additional incident response.
About The Author:
Yogesh Naager is a content marketer who specializes in the cybersecurity and B2B space. Besides writing for the News4Hackers blogs, he also writes for brands including Craw Security, Bytecode Security, and NASSCOM.
Read More:
Black Basta Ransomware Group Accused of Targeting Ukraine & Germany