Discord Accounts Hit by VVS Stealer Malware via Obfuscated Python Code

“Recently, a new type of malware, “VVS Stealer Malware,” is targeting Discord accounts through obfuscated Python code.”
VVS Stealer, also known as VVS $tealer, is a new Python-based information stealer that can grab Discord tokens and passwords, according to information released by cybersecurity researchers.
Palo Alto Networks Unit 42, Report
| According to reports, the stealer was available for purchase on Telegram as early as April 2025. |
Pranay Kumar Chhaparwal & Lee Wei Yeong, Researchers
| “Pyarmor obfuscates the code of the VVS stealer.”
“Python scripts can be obfuscated using this tool to prevent signature-based detection and static analysis. Both lawful uses and the creation of covert malware are possible using Pyarmor.” |
Promoted on Telegram as the “ultimate stealer,” a weekly subscription costs €10 ($11.69). It is also among the least expensive stealers available, costing €20 ($23) for a month, €40 ($47) for three months, €90 ($105) for a year, and €199 ($232) for a lifetime license.
Deep Code, Report, Late April 2025
| The stealer is thought to be the work of a French-speaking threat actor who also participates in Telegram groups connected to stealers, like Myth Stealer and Eyes Stealer GC. |
The PyInstaller package is used to distribute the VVS Stealer malware, which is protected by Pyarmor. The stealer ensures that it is launched automatically after a system reboot by adding itself to the Windows Startup folder once it has been launched.
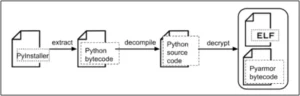
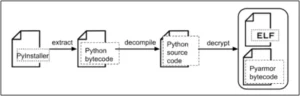
Additionally, it shows phony “Fatal Error” pop-up alerts that tell users to restart their computers to fix a problem and capture a variety of data:
- Discord data (account details and tokens).
- Chromium and Firefox web browser data (cookies, history, passwords, and autofill data).
In order to take over active sessions on the compromised device, VVS Stealer is also made to carry out Discord injection attacks. If the Discord app is already open, it first ends it to accomplish this.
Next, it uses the Chrome DevTools Protocol (CDP) to download an obfuscated JavaScript payload from a remote server that is in charge of keeping an eye on network activity.
Discord
| “To avoid detection by cybersecurity tools, malware authors are increasingly using sophisticated obfuscation techniques, which makes it more difficult to analyze and reverse-engineer their dangerous software.”
“Because this threat uses sophisticated obfuscation and Python is simple for malware authors to utilize, the end product is a highly powerful and covert malware family.” “A sizable portion of the sites hosting these campaigns are legal companies whose administrator credentials were taken by the very infostealers they are now disseminating, rather than malicious infrastructure created by attackers.” |
The revelation coincides with Hudson Rock’s description of how threat actors use information stealers to steal administrative credentials from reputable companies. They then use their infrastructure to spread the malware using ClickFix-style operations, creating a self-sustaining circle.
About The Author
Suraj Koli is a content specialist in technical writing about cybersecurity & information security. He has written many amazing articles related to cybersecurity concepts, with the latest trends in cyber awareness and ethical hacking. Find out more about “Him.”
Read More:
Phoenix University Major Data Breach Involving Details of 35 lakh+ People