Espionage Malware Deployed by China-Aligned Threat Group Using Windows Group Policy
Espionage Malware Deployed by China-Aligned Threat Group Using Windows Group Policy
A number of cyberattacks against governmental organizations in Southeast Asia and Japan have been linked to LongNosedGoblin, an undiscovered China-aligned threat cluster.
According to a report released today by Slovak cybersecurity firm ESET, the ultimate objective of these operations is cyber espionage. It has been determined that the threat activity cluster has been active since at least September 2023.
According to security researchers Anton Cherepanov and Peter Strěček, “LongNosedGoblin utilizes Group Policy to spread malware across the hacked network and cloud services (e.g., Microsoft OneDrive and Google Drive) as command and control (C&C) servers.”
On Windows computers, Group Policy is a tool for controlling permissions and settings. Microsoft claims that Group Policy can be used to administer server systems and specify configurations for user groups and client computers.
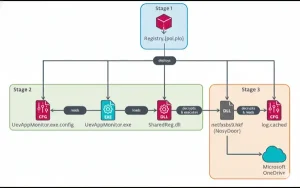
The employment of a diverse bespoke toolkit, primarily C#/.NET apps, is what distinguishes the attacks.
- NosyHistorian, which gathers browser history from Mozilla Firefox, Microsoft Edge, and Google Chrome
- NosyDoor is a backdoor that exfiltrates files, deletes files, and runs shell commands using Microsoft OneDrive as C&C.
- Google Chrome and Microsoft Edge browser data can be exfiltrated by NosyStealer and stored in an encrypted TAR archive on Google Drive.
- To download and execute a payload in memory, like NosyLogger, use NosyDownloader.
- A modified DuckSharp program called NosyLogger is used to record keystrokes.
According to ESET, the hacking group’s activities were initially discovered in February 2024 on a Southeast Asian governmental entity’s system. Eventually, it was discovered that Group Policy was utilized to spread the virus to several computers belonging to the same company. It is yet uncertain what specific initial access techniques were employed in the assaults.
While many victims were impacted by NosyHistorian between January and March 2024, only a portion of these people were infected with NosyDoor, suggesting a more focused strategy, according to an additional study. It has occasionally been discovered that the dropper used to install the backdoor via AppDomainManager injection has “execution guardrails” intended to restrict operation to the computers of particular victims.
Other tools used by LongNosedGoblin include a Cobalt Strike loader, a reverse SOCKS5 proxy, and software that runs a video recorder to record audio and video.
The cybersecurity firm highlighted the lack of conclusive proof connecting the threat actor’s tradecraft to clusters identified as ToddyCat and Erudite Mogwai, albeit pointing out that there are some weak connections. However, given the similarities between NosyDoor and LuckyStrike Agent, as well as the fact that LuckyStrike Agent’s PDB path contains the words “Paid Version,” there is a chance that the malware will be licensed or sold to other threat actors.
“We later discovered an additional instance of a NosyDoor version attacking an organization in an E.U. country, once again deploying similar TTPs, and employing the Yandex Disk cloud service as a C&C server,” the investigators stated. “The widespread distribution of this NosyDoor variant indicates that the malware may be distributed among multiple China-aligned threat groups.”
About The Author:
Yogesh Naager is a content marketer who specializes in the cybersecurity and B2B space. Besides writing for the News4Hackers blogs, he also writes for brands including Craw Security, Bytecode Security, and NASSCOM.
Read More:
Cisco: Zero-Day Exploit Hits Key Security Products, Need System Rebuilding