GlassWorm Malware Campaign Targets iMacs with Trojanized Crypto Wallets
GlassWorm Malware Campaign Targets iMacs with Trojanized Crypto Wallets
A VS Code-compatible editor’s capabilities can be increased by adding features and productivity boosts in the form of development tools, language support, or themes through extensions found in the OpenVSX registry and the Microsoft Visual Studio Marketplace.
The official Visual Studio Code extension shop is the Microsoft marketplace, while OpenVSX is an open, vendor-neutral substitute that is mostly utilized by editors who do not support or prefer not to rely on Microsoft’s proprietary marketplace.
Using “invisible” Unicode characters to conceal itself inside malicious extensions, the GlassWorm virus initially surfaced on the marketplaces in October.
Once installed, the virus tried to steal cryptocurrency wallet information from many extensions as well as login credentials for GitHub, npm, and OpenVSX accounts. It also allowed VNC remote access and could use a SOCKS proxy to transport traffic through the victim’s computer.
GlassWorm reappeared in early November on OpenVSX and again in early December on VSCode, despite strengthened protections and public disclosure.
GlassWorm back on OpenVSX
In contrast to earlier GlassWorm campaigns that solely targeted Windows systems, Koi Security researchers found a new one that targets macOS computers entirely.
The most recent GlassWorm attacks employ an AES-256-CBC-encrypted payload contained in compiled JavaScript in the OpenVSX extensions, as opposed to the invisible Unicode seen in the first two waves or the built Rust binaries used in the third:
- studio-velte-distributor.pro-svelte-extension
- cudra-production.vsce-prettier-pro
- Puccin-development.full-access-catppuccin-pro-extension
After a 15-minute delay, the malicious logic starts running, probably in an effort to avoid detection in sandboxed situations.
It now uses AppleScript in place of PowerShell and LaunchAgents for persistence in place of Registry manipulation. However, experts claim that there is also infrastructure overlap and that the Solana blockchain-based command-and-control (C2) mechanism is still in place.
GlassWorm now aims to steal Keychain passwords in addition to over 50 browser encryption extensions, developer credentials (GitHub, NPM), and browser data.
It also has a new function that allows it to detect hardware bitcoin wallet apps on the host, such as Ledger Live and Trezor Suite, and replace them with a trojanized version.
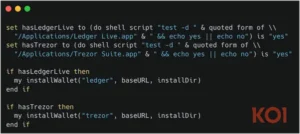
Code to replace legitimate hardware wallets
Source: Koi Security
However, because the trojanized wallets are delivering empty files, Koi Security observes that this approach is presently failing.
“This could mean the attacker is still preparing the macOS wallet trojans, or the infrastructure is in transition,” says Koi Security.
“The capability is ready and constructed; payloads need to be uploaded. All other harmful features, including persistence, data exfiltration, keychain access, and credential theft, are still fully functional.
News4Hackers displayed a warning for two of the malicious extensions, stating that their publisher was unreliable, when it tested to see if they were still accessible on OpenVSX.
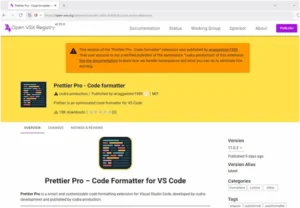
GlassWorm extension on OpenVSX
Source: Google
More than 33,000 installs are displayed in the download counters; however, threat actors often modify these numbers to make the files seem more reliable.
It is advised that developers who have installed any of the three extensions delete them right away, reset the passwords for their GitHub accounts, cancel their NPM tokens, look for any indications of infection on their system, or reinstall them.
About The Author:
Yogesh Naager is a content marketer who specializes in the cybersecurity and B2B space. Besides writing for the News4Hackers blogs, he also writes for brands including Craw Security, Bytecode Security, and NASSCOM.
Read More:
RondoDox Botnet Attacked on Critical React2Shell Flaw To Access IoT Devices & Web Servers