Latest LockBit 5.0 is Targeting Linux, ESXi, and Windows

The most recent activity from the infamous LockBit ransomware, with its 5.0 version, which has sophisticated obfuscation, anti-analysis tactics, and seamless cross-platform capabilities for Windows, Linux, and ESXi systems, was examined by Trend™ Research using source binaries.
The original article was also written by Trend Micro, detailing all the factors that the latest LockBit 5.0 is using to target Linux, Windows, and ESXi operating systems.

Key takeaways:
- By loading its payload via DLL reflection and employing anti-analysis techniques, the LockBit 5.0 Windows edition employs severe obfuscation and packing. With command-line parameters for focusing on particular directories and file types, the Linux version offers comparable capabilities. The VMware virtualization infrastructure, which is intended to encrypt virtual machines, is the specific target of the ESXi variation.
- The latest versions have event log clearing after encryption, avoid Russian language systems, and employ randomized 16-character file extensions.
- Additionally, a specific ESXi in LockBit 5.0 targets VMware’s ESXi virtualization architecture.
- LockBit’s continuous cross-platform strategy is confirmed by the availability of Windows, Linux, and ESXi variants, which allow for simultaneous attacks across whole company networks, including virtualized environments. LockBit 5.0 is far more hazardous than its predecessors due to heavy obfuscation and technical advancements across all variations.
- Trend Vision OneTM gives users access to hunting queries, threat insights, and intelligence reports about LockBit 5.0 in addition to detecting and blocking the specific IoCs listed in this blog.
Following the February 2024 law enforcement action (action Cronos) that crippled their infrastructure, Trend™ Research has discovered and examined the source binaries of a new LockBit version in the wild. Reportedly, the LockBit ransomware organization announced the release of “LockBit 5.0” in early September, marking their sixth anniversary. After finding a binary that was accessible in the wild, Trend Research started an investigation that first identified a Windows variant of LockBit 5.0 and verified the presence of Linux and ESXi variants.
This most recent development carries on the company’s long-standing cross-platform approach, which dates back to LockBit 2.0 in 2021.
The Windows program employs strong obfuscation and packing, according to Trend Research’s study. It loads its payload via DLL reflection and employs anti-analysis strategies like ETW patching and stopping security services. The recently found Linux version, meanwhile, keeps the same functionality and offers command-line options to target particular directories and file types. The ESXi variation, which is intended to encrypt entire virtual machine infrastructures in a single attack, targets VMware virtualization setups in particular.
Our research also shows that these more recent versions have similar features, such as randomly generated 16-character file extensions, geolocation-based Russian language system avoidance, and post-encryption event log wiping. Additionally, the 5.0 version’s code is similar to that of LockBit 4.0, including the same hashing algorithms and API resolution techniques, demonstrating that this is an evolution of the original codebase rather than a copy.
LockBit 5.0 Windows analysis
Help information is displayed using the -h option in the Windows version of Lockbit 5.0. The updated version has a cleaner, better user interface than its predecessors. It explains a number of settings and options for running the ransomware, such as the fundamental ones like naming folders to encrypt or bypass, operation modes like verbose and invisible mode, note settings, encryption settings, filtering options, and usage samples. The attacker’s versatility and customisation are demonstrated by the specific instructions and parameters.
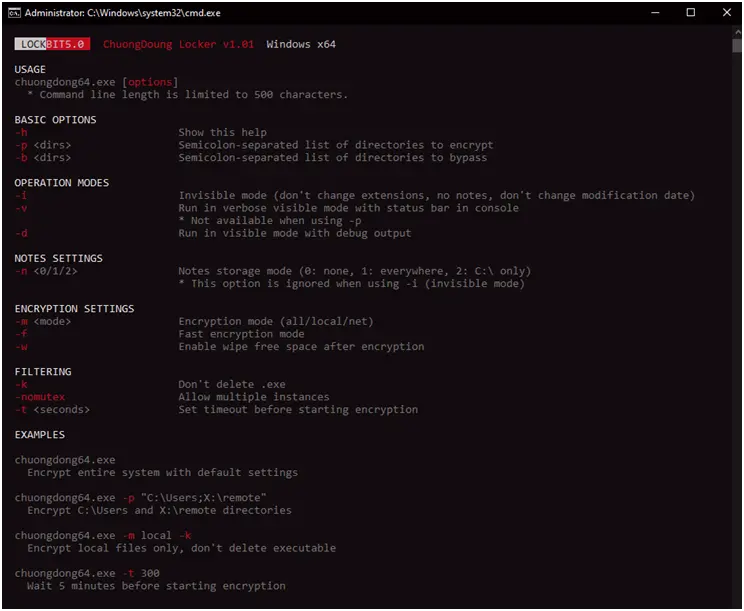
Figure 1. The help command shows the parameters and their respective uses
The command line parameters seen in Trend Research’s threat hunting study are shown in Table 1, along with a description of each.
| Option | Description |
| Basic Options | |
| -h | Show help |
| -d <dirs> | Semicolon-separated list of directories to encrypt |
| -b <dirs> | Semicolon-separated list of directories to bypass |
| Operation Modes | |
| -i | Invisible mode (don’t change extensions, no notes, don’t change modification date) |
| -p | Run in verbose visible mode with status bar in console (not available when using -i) |
| -v | Run in visible mode with debug output |
| Notes Settings | |
| -n <0/1/2> | Notes storage mode: |
| 0: None | |
| 1: Everywhere | |
| 2: C:\ only | |
| Ignored when using -i (invisible mode) | |
| Encryption Settings | |
| -m <mode> -w | Encryption mode: |
| all: Encrupt all files | |
| local: Encrypt local files | |
| net: Encrypt network files | |
| Enable wipe free space after encryption | |
| Filtering | |
| -k | Don’r delete .exe files |
| -nomutex | Allow multiple instances |
| Timeout | |
| -t <seconds> | Set a timeout before starting encryption |
Table 1. A summary of the command line arguments in our analysis of the LockBit 5.0 Windows version.
When the ransomware is executed, it creates its trademark ransom message and points victims to a specific leak website. With a simplified “Chat with Support” component for ransom talks, the infrastructure upholds LockBit’s well-established victim interaction approach.
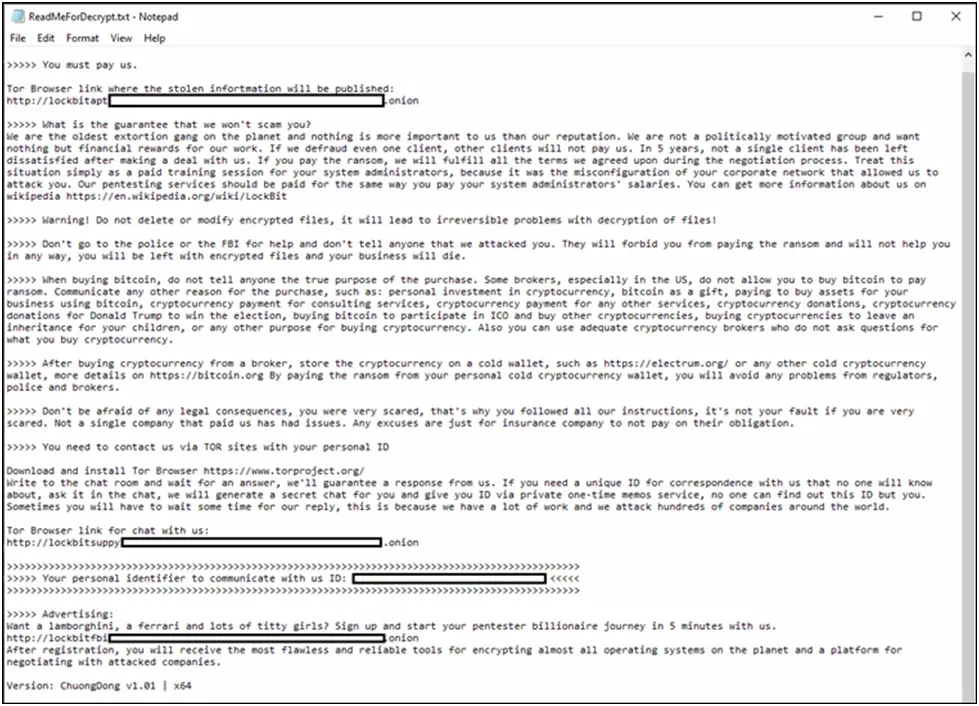
Figure 2. The ransom note generated by LockBit 5.0
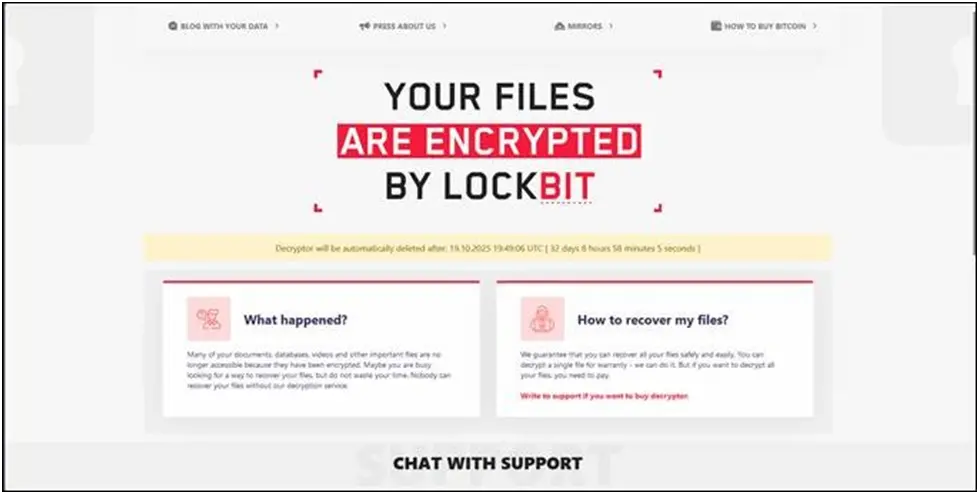
Figure 3. The leak site, where the link in the ransom note directs when visited by victims
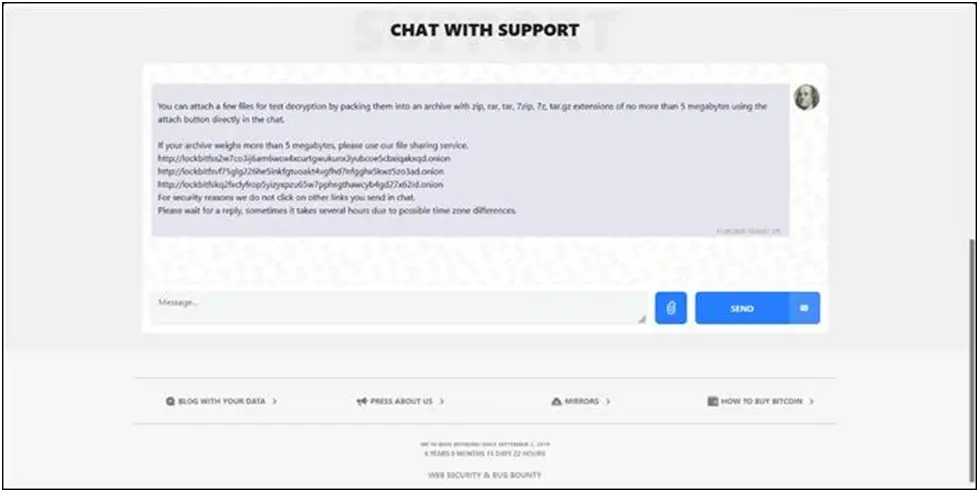
Figure 4. The data leak site provides a direct communication channel with the victims in the “Chat with Support” section.
Recovery attempts are made more difficult by the encryption process, which adds random 16-character extensions to files. LockBit 5.0 does not use conventional infection identifiers at file endings, in contrast to several ransomware variants that do. Consistent patterns, such as the original file size embedded in the encrypted file footer, were found by our research.
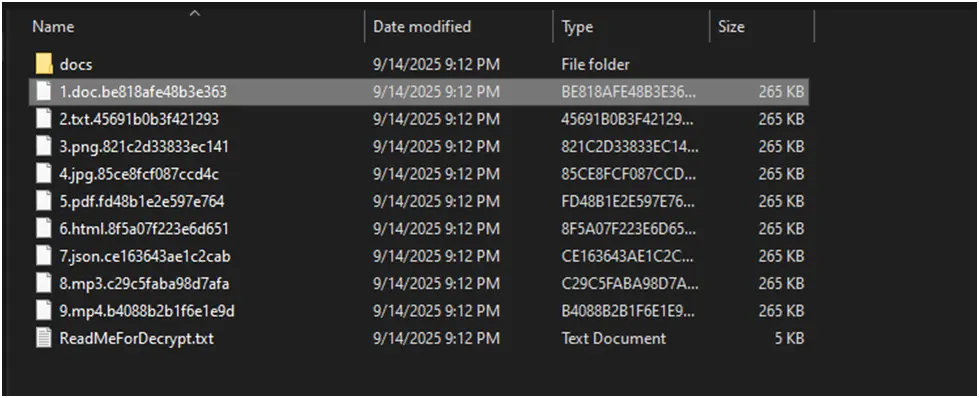
Figure 5. LockBit 5.0 encrypted files are appended with unique and seemingly randomly generated extensions with 16 characters, which complicates the decryption process.
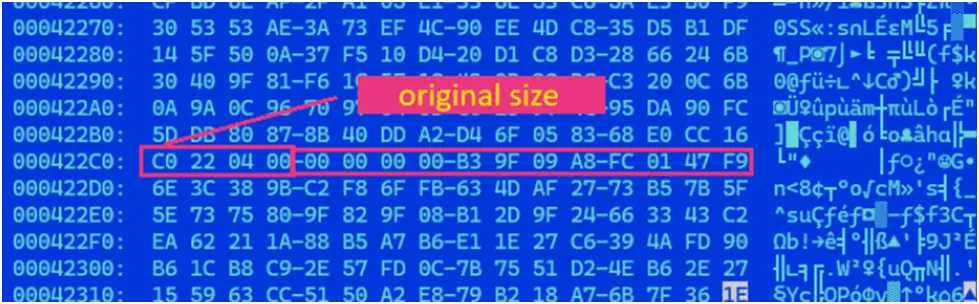
Figure 6. End part of encrypted file A
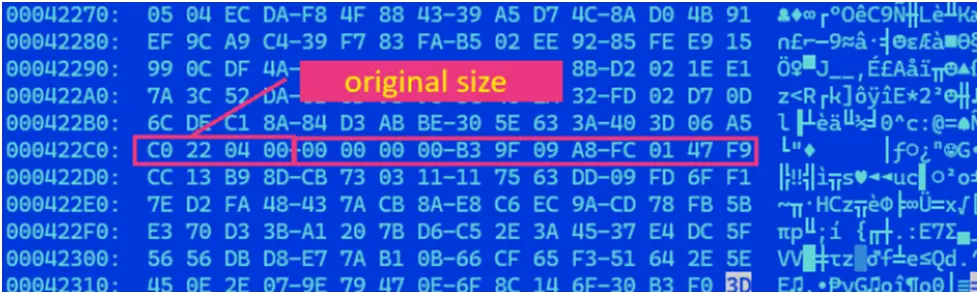
Figure 7. End part of encrypted file B
Heavy obfuscation through packing is used in the Trend Research sample that was examined. We found that it serves as a binary loader during debugging, decrypting a PE binary in memory, and loading it using DLL reflection techniques. Static analysis is made much more difficult by this complex loading procedure.
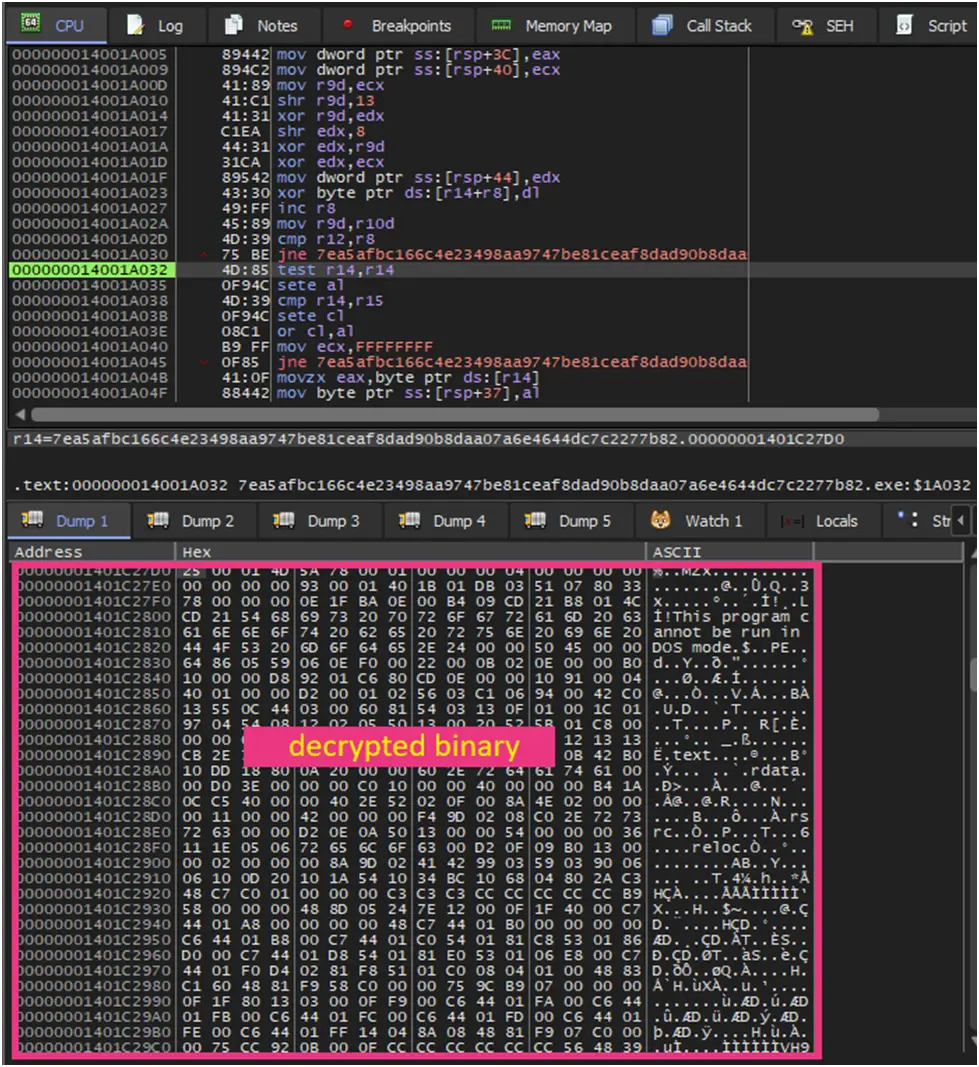
Figure 8. Decrypted PE binary in the memory of loader
In addition, the malware employs a number of anti-forensics strategies. In order to disable Windows Event Tracing, it patches the EtwEventWrite API by replacing it with a 0xC3 (return) command. After encryption is finished, it also uses the EvtClearLog API to delete all event logs and ends security-related services by comparing hashed service names to a hardcoded set of 63 values.
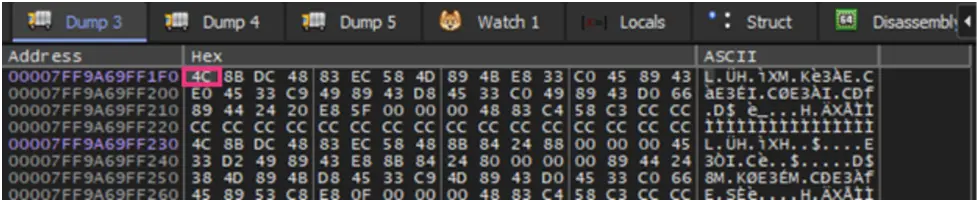
Figure 9. Before patching of EtwEventWrite
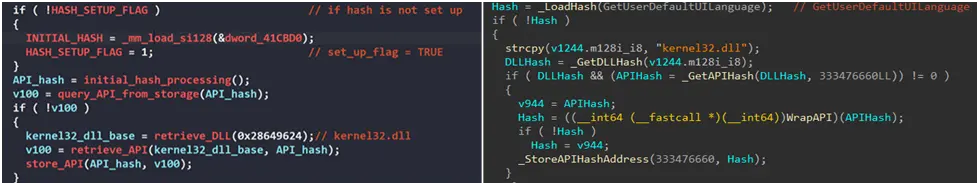
Figure 10. After patching EtwEventWrite, the malware shows a C3 byte, forcing it to immediately return.
If they are running the system, it compares each service by hashing the service name and comparing it with the list that is hardcoded. After that, service names that match are shut down.
| FEF56F15, BEC3470B, 9757464D, 88CE6B8E, 826AC445, 83143F70, 8685D050, 493AEE1F, 35BE2F4E, 23FA53E4, FEF56F16, 10D06066, 1370CEA3, E11A285C, DBECA3C2, BEC3470C, C347B317, CA6C4394, 732AA0BF, 60B29D13, 493AEE20, 5E5F1954, 5EF504FC, A49FA5E2, 9757464E, 9A768D62, A1816235, 41278146, 35BE2F4F, 369D7114, 3B6794E3, E7AA4056, E11A285D, E5C9CC93, E66A2C63, 7B39B584, 732AA0C0, 739BF272, 7ABD1404, 88CE6B8F, 9439954E, 9655130F, 23FA53E5, 26336765, 2C1F8E5F, DBECA3C3, DCF04E8C, DEED0E56, 60B29D14, 62C32884, 6337AD82, A49FA5E3, A8F16BAB, BD071334, 41278147, 4292EDD8, 47F1286A, E7AA4057, E7BF305D, F82A288D, 7B39B585, 7F480CF7, 7DD43601 |
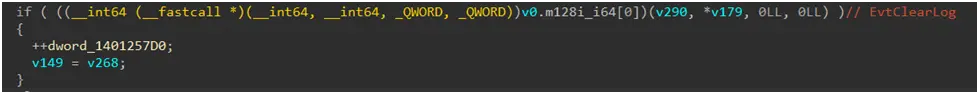
Figure 11. Event log clearing using the EvtClearLog API
Like its predecessors, LockBit 5.0 has geopolitical protections that stop the program’s execution when it detects Russian language settings or Russian geolocation. Ransomware organizations from Eastern Europe frequently engage in this behavior.
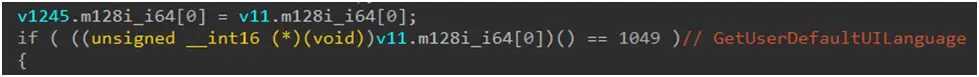
Figure 12. This code terminates if the language is Russian
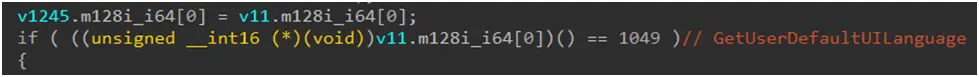
Figure 13. This code terminates if the geolocation is Russia
LockBit 5.0 Linux analysis
The 5.0 Linux version exhibits LockBit’s dedication to cross-platform compatibility by sharing features with its Windows equivalent. Attackers have the same operational flexibility on both systems because of the command-line interface’s replication of the Windows version’s layout and features.
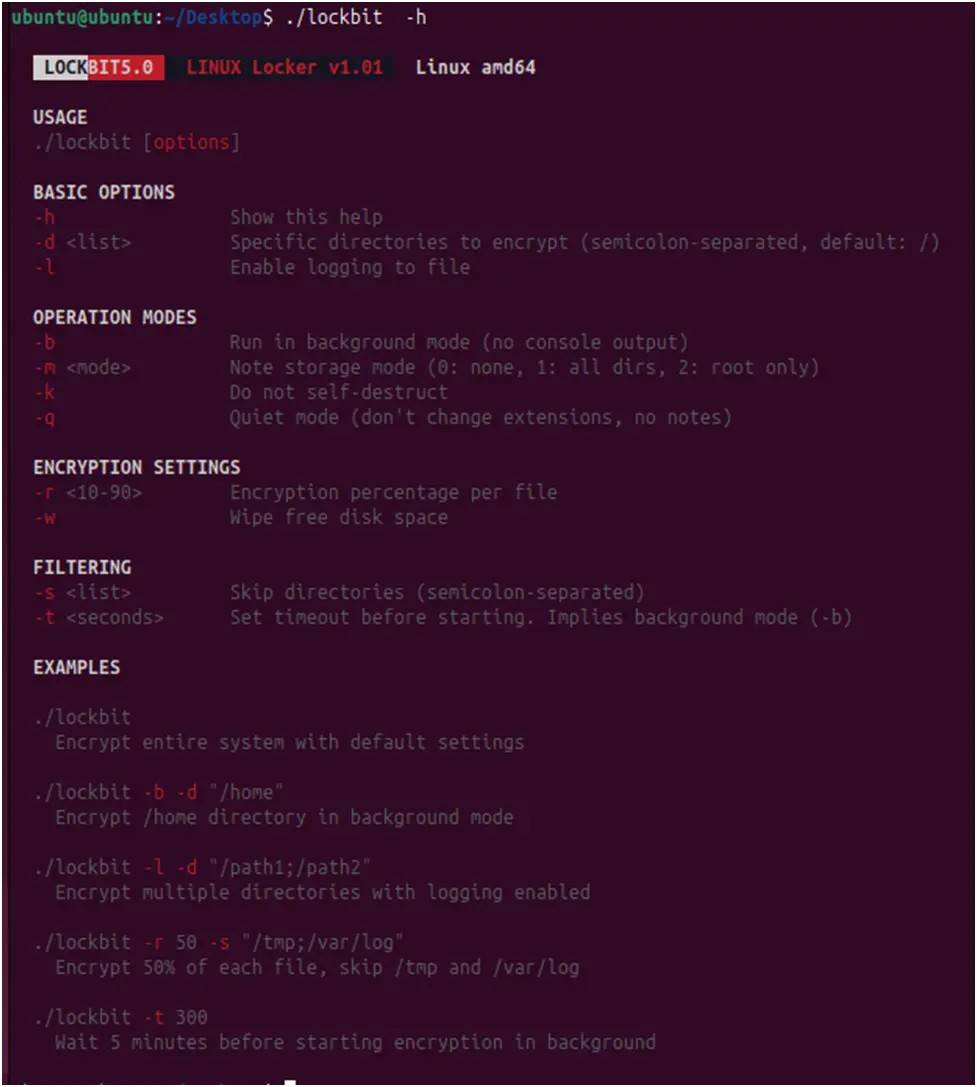
Figure 14. The LockBit 5.0 Linux version shows a similar formatting of help options
The Linux version offers thorough activity logging while it is running, highlighting files that are encrypted and folders that are excluded. The variation may be utilized in testing environments or by affiliates that need thorough execution feedback, based on the transparency of the operation logs.
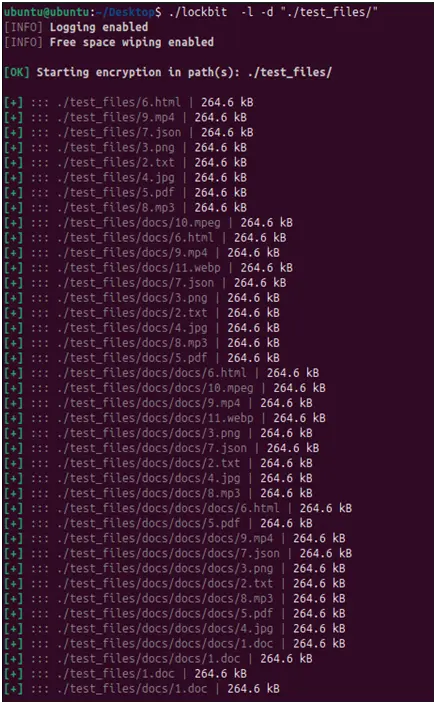
Figure 15. Logging activity shows the files to be encrypted
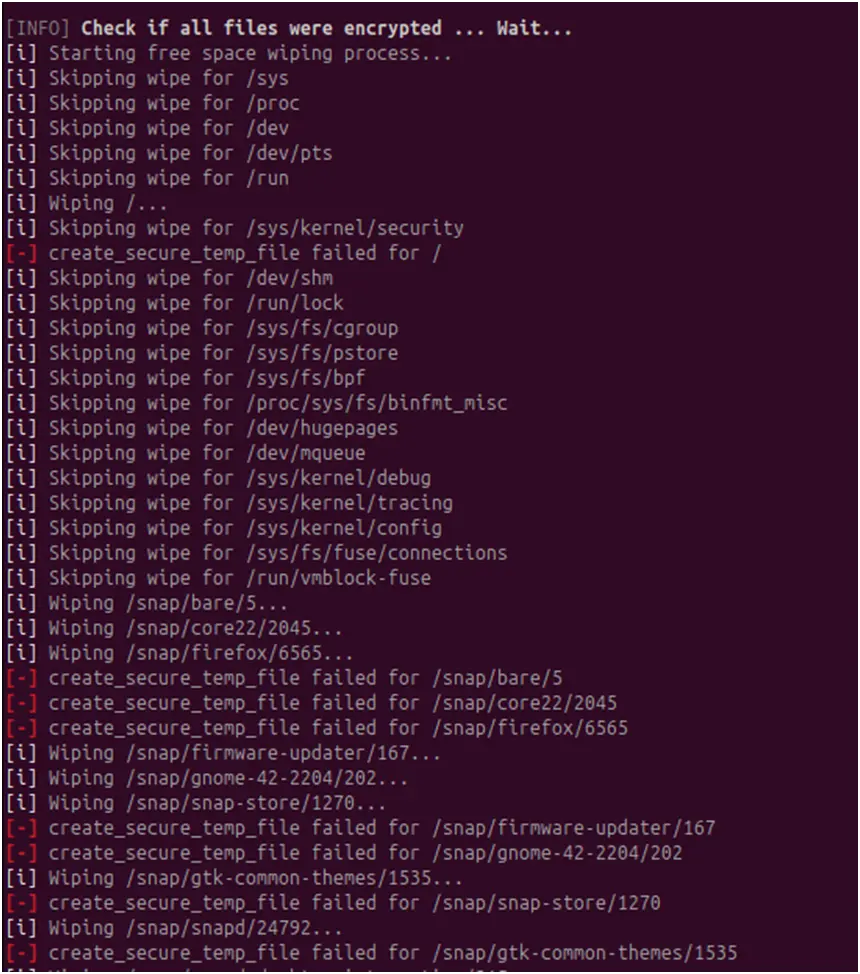
Figure 16. Logs show the list of folders to be skipped when wiping
The ransomware creates a thorough report after it is finished, displaying the total number of encrypted files and their combined size. It handles encrypted files with random extensions, the same as the Windows version, so post-encryption file handling is consistent across platforms.
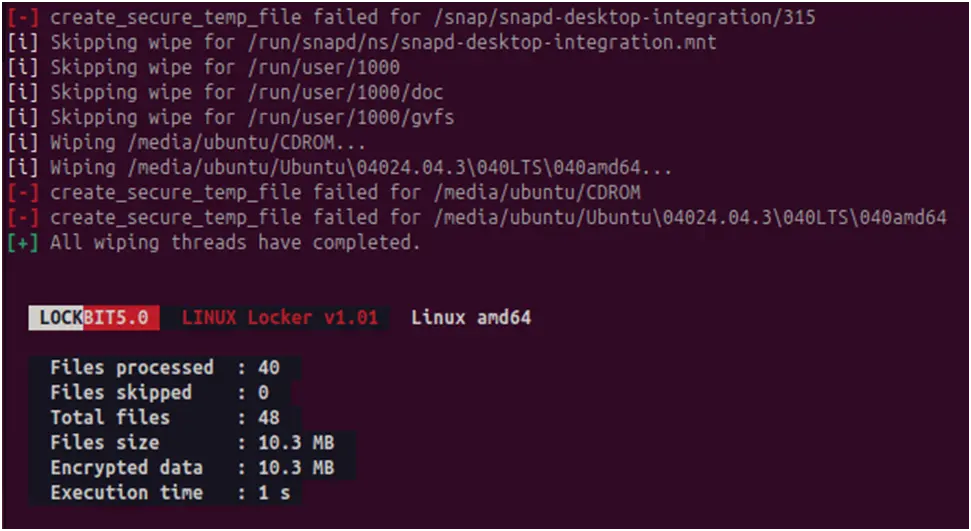
Figure 17. A summary shows the total number of files and the size of the encrypted files
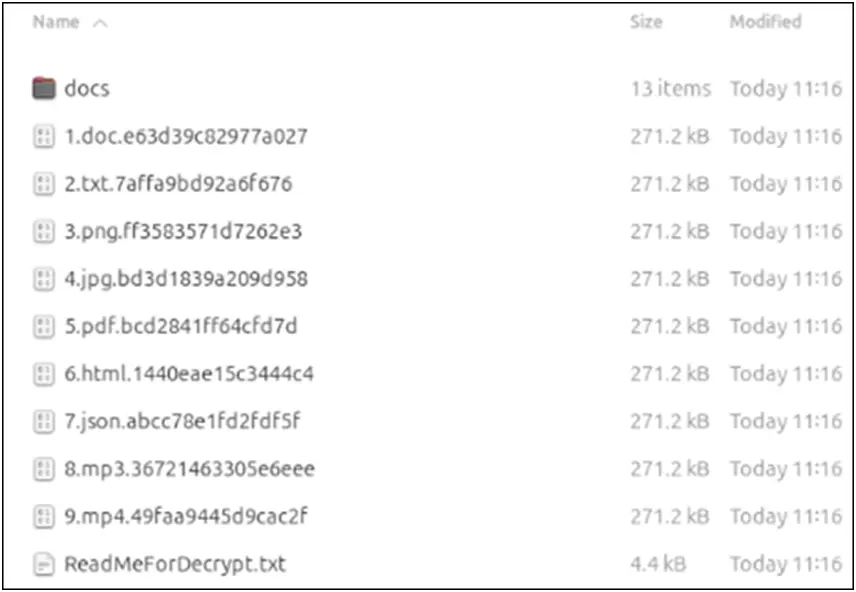
Figure 18. A list of files encrypted that have random extensions
LockBit 5.0 ESXi analysis
After more research, a specific ESXi version of LockBit 5.0 that targets VMware virtualization architecture was discovered. Given that ESXi servers frequently house numerous virtual machines, this variant constitutes a significant advancement in LockBit’s capabilities since it enables attackers to encrypt whole virtualized environments with a single payload execution.
Attackers can operate consistently across all platforms thanks to the ESXi variant’s maintenance of the same command-line interface structure as its Windows and Linux counterparts. Targeting particular directories and VM configuration files is one of the ESXi-specific parameters designed for virtual machine encryption that can be found in the help menu.
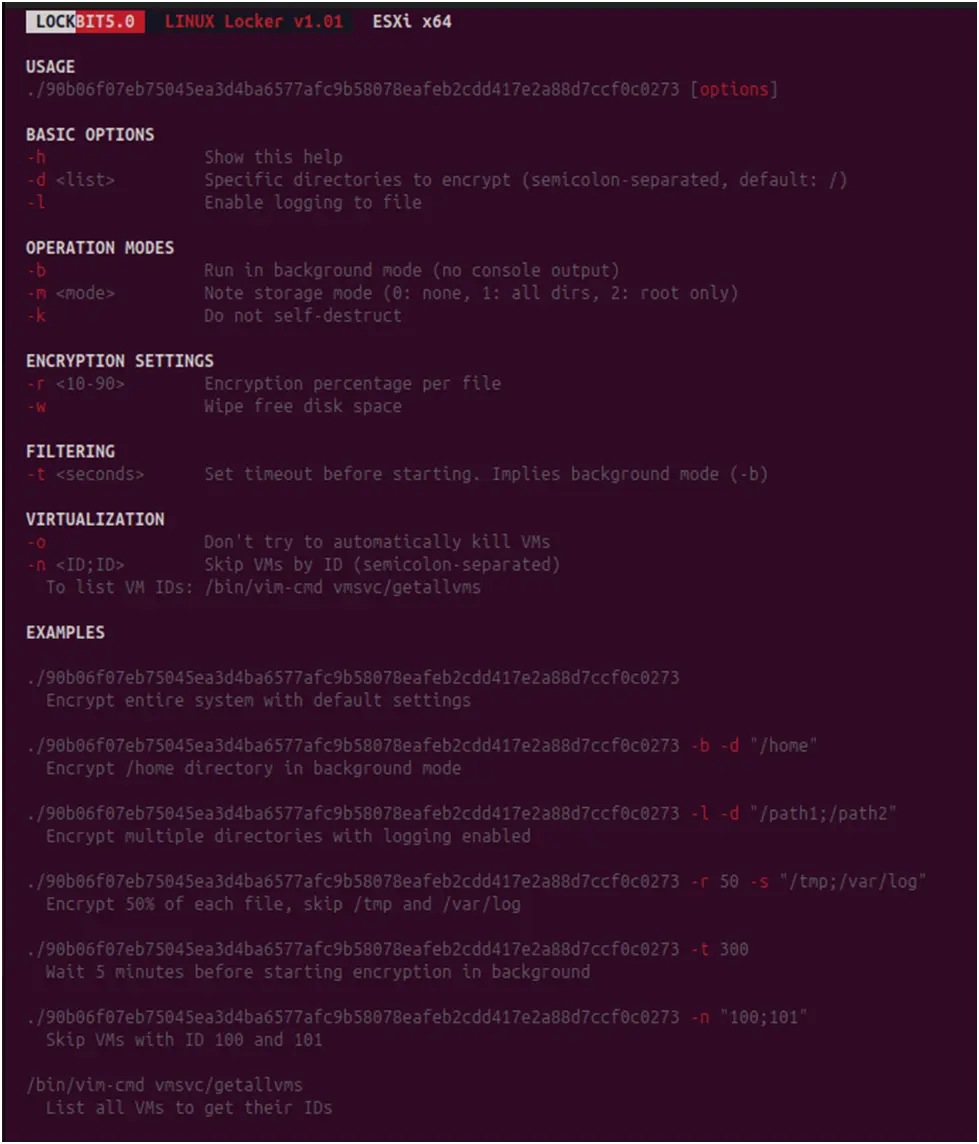
Figure 19. The ESXi variant help command shows virtualization-specific parameters
A single compromised ESXi host can produce dozens or hundreds of encrypted virtual machines, greatly increasing the attack’s potential to interrupt business operations. This ESXi variant exemplifies LockBit’s strategy, which focuses on maximizing impact through virtualization infrastructure.
LockBit 4.0 versus LockBit 5.0
Instead of a total redesign, a comparison of LockBit 4.0 and 5.0 shows substantial code reuse and evolutionary progress. For string operations—a crucial part of API resolution and service identification—both versions use the same hashing techniques. The dynamic API resolution code structure is very consistent across versions, indicating that the developers built on top of the LockBit 4.0 codebase. Chuong Dong’s blog is the source of the screenshots on the left in figures 20 and 21.
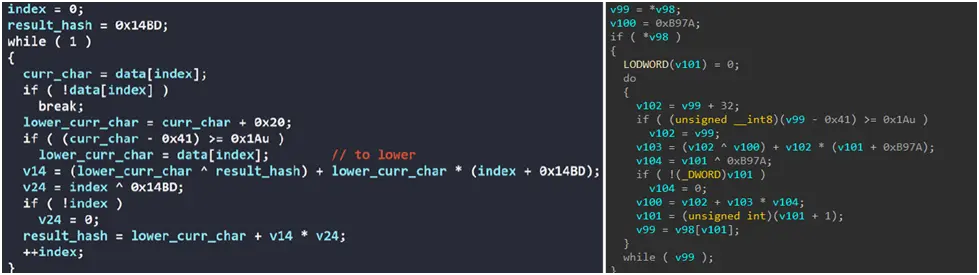
Figure 20. Similarities of the hashing algorithm of the string of LockBit 4.0 (left – screenshot from Chuong Dong’s blog) and LockBit 5.0 (right)
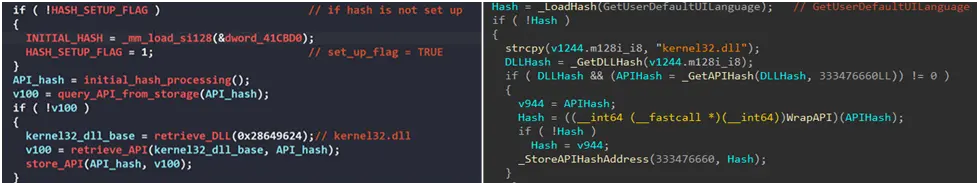
Figure 21. Dynamic API resolution of LockBit 4.0(left – screenshot from blog) and LockBit 5 (right)
According to Trend Research, these parallels show unequivocally that LockBit 5.0 is a continuation of the LockBit ransomware family rather than a copy or rebranding by other threat actors. The group’s strategy of gradually improving its ransomware platform is demonstrated by the addition of new evasion strategies while maintaining essential capabilities.
The Bottom Line
The fact that LockBit has Windows, Linux, and ESXi versions attests to its ongoing cross-platform approach. With the ESXi variation intended to destroy entire virtual infrastructures, this allows for simultaneous attacks across entire company networks, from desktops to crucial servers housing databases and virtualization platforms. LockBit 5.0 is much more hazardous than its predecessors due to technical advancements, including faster encryption, improved evasion, and the removal of infection marks, while heavy obfuscation throughout these new variations greatly delays the creation of detection signatures.
One of the most well-known ransomware-as-a-service (RaaS) organizations, LockBit, has continuously outperformed its rivals by aggressively evolving its strategies and tactics. All three versions of version 5.0 have now been verified, demonstrating the criminals’ tenacity in the face of Operation Cronos. Companies need to make sure they have thorough cross-platform protections in place, paying special attention to safeguarding virtualized infrastructure. The Windows, Linux, and ESXi versions of LockBit 5.0 provide further evidence that no platform or operating system is immune to contemporary ransomware attacks.
Mitigating risk from LockBit 5.0 by Craw Security
By proactively carrying out threat hunting exercises customized to group-specific tools, techniques, and procedures, organizations are strongly urged to assess and improve their security posture. Strengthening network and endpoint security is crucial, as is early identification of defense evasion tactics used to undermine security measures.
Moreover, interested individuals and organizations can also seek proactive measures from the world-class VAPT Solutions in India by Craw Security, which is the sister vertical of News4Hackers, which delivers quality penetration testing solutions under the proactive supervision of superb penetration testers with many years of classic work experience in delivering superior pentesting services throughout several IT Security parameters to all types of organizations.
To know more about the best price range that Craw Security offers, you can visit the Official Website of Craw Security and give them a call at their hotline mobile number, +91-9513805401.
Indicators of Compromise (IOCs)
Indicators of compromise can be found here.
About The Author:
Yogesh Naager is a content marketer who specializes in the cybersecurity and B2B space. Besides writing for the News4Hackers blogs, he also writes for brands including Craw Security, Bytecode Security, and NASSCOM.
Read More:
An AI-Powered App Raises the Risk of Supply Chain Attacks by Exposing User Data







