Malware Attacks on Chinese People involving HiddenGh0st, and kkRAT Exploit SEO

“Chinese people are being attacked by various malware attacks currently.”
A search engine optimization (SEO) poisoning effort targets Chinese-speaking people by disseminating malware through phony software websites.
Pei Han Liao, Labs Researcher, Fortinet FortiGuard
| “The attackers registered lookalike domains that closely resembled genuine software websites and used SEO plugins to influence search rankings.”
They deceived victims into accessing spoof websites and downloading malware by employing persuasive language and minor character changes. |
The cybersecurity firm noticed the activity in August 2025. It results in the distribution of malware families such as HiddenGh0st and Winos (also known as ValleyRAT), which are both variations of the remote access trojan Gh0st RAT.
Notably, the use of Winos has been linked to a cybercrime group called Silver Fox, which is also known as SwimSnake, Void Arachne, The Great Thief of Valley (or Valley Thief), and UTG-Q-1000. At least from 2022, it is thought to have been operational.
Users who seek programs like DeepL Translate, Google Chrome, Signal, Telegram, WhatsApp, and WPS Office on Google are led to fake websites in the most recent assault chain that Fortinet has discovered. This causes trojanized installers to deploy the malware.
Fortinet
| “Nice is the name of the script. The virus delivery mechanism on these websites is managed by JavaScript,” Fortinet clarified.
“A download link is called first, and the script returns JSON data, including a secondary link, in a multi-step chain. After that, the secondary link leads to another JSON answer with a link that reroutes to the malicious installer’s final URL.
According to Fortinet, “customers found it challenging to detect the infection because the installers included both the malicious payload and the genuine application.”
“In this manner, even highly ranked search results were weaponized, highlighting the significance of closely examining domain names before downloading software.” |
A malicious DLL (“EnumW.dll”) is included in the installer. It performs a number of anti-analysis checks to evade detection, such as extracting another DLL (“vstdlib.dll”) to overload analysis tools by increasing memory utilization and degrading their functionality.
The second DLL is designed to detect whether 360 Total Security antivirus software is installed on the infected host before unpacking and launching the main payload. If it is present, the virus establishes persistence and eventually launches a Windows executable (“insalivation.exe”) using a method known as TypeLib COM hijacking.
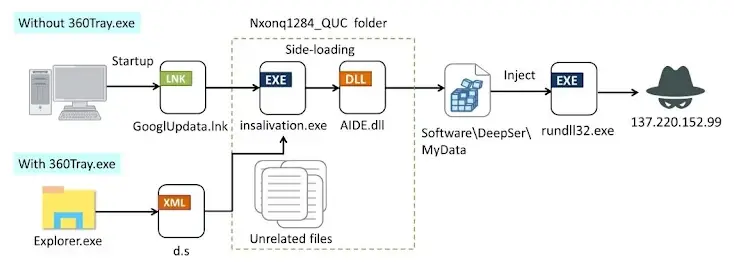
By making a Windows shortcut that points to the same executable, persistence is accomplished even if the antivirus program is not present on the host. The infection’s ultimate objective is to sideload a DLL (“AIDE.dll”) that starts three essential processes:
- To communicate with a distant server and exchange encrypted data, use command-and-control (C2).
- Heartbeat, to gather victim and system information and count active processes in comparison to a hard-coded list of security products.
- In order to verify persistence, monitor the victim’s surroundings, keep tabs on user behavior, and send a beacon to the C2 server.
Commands to download other plugins, record keystrokes and clipboard information, and even take over Ethereum and Tether cryptocurrency wallets are also supported by the C2 module. Previously classified as components of the Winos framework, several of the detected plugins have the ability to monitor the victim’s screen.
Malware Trifecta Targets Chinese Speakers, Including New kkRAT#
The development coincides with Zscaler ThreatLabz identifying a different campaign that targets Chinese-speaking individuals and uses Winos, FatalRAT, and kkRAT, a previously undocumented virus, from early May 2025.
Muhammed Irfan V A, Researcher, Zscaler
| China-based hackers usually use kkRAT, which “has code similarities with both Gh0st RAT and Big Bad Wolf (大灰狼).” According to Zscaler researcher Muhammad Irfan V. A.
Similar to Ghost RAT, kkRAT uses a network connection protocol, but after data compression, it adds an encryption layer. Among the features of the RAT are the implementation of remote monitoring tools (such as Sunlogin and GotoHTTP) and the manipulation of the clipboard to substitute cryptocurrency addresses. |
Similar to the previously stated activities, the attack campaign distributes the three trojans by imitating well-known software, such as DingTalk, through phony installer pages. Because the phishing sites are hosted on GitHub pages, the criminals may take advantage of the credibility that comes with a trustworthy platform to spread malware. The pages were deployed using a GitHub account that is no longer accessible.
The installer hosted on the websites performs several checks after the user launches it in order to detect virtual machines (VMs) and sandbox environments, and to get around security measures.
Additionally, it asks for administrator capabilities, which, if granted, allow it to list and momentarily deactivate every network device that is currently in use. This basically prevents antivirus software from operating normally.
The malware’s use of the Bring Your Own Vulnerable Driver (BYOVD) approach, which involves reusing code from the RealBlindingEDR open-source project, to disarm host-installed antivirus protection, is another noteworthy feature. The following five programs are explicitly searched for by the malware:
- 360 Internet Security Suite
- 360 Total Security
- HeroBravo System Diagnostics suite
- Kingsoft Internet Security
- QQ电脑管家
Following the termination of the pertinent antivirus-related processes, the malware proceeds to establish a scheduled task that executes a batch script with SYSTEM privileges, guaranteeing that the processes are automatically stopped each time a user signs in to the computer.
Additionally, it alters 360 Total Security Windows Registry entries, most likely with the intention of turning off network checks. The malware then re-enables network adapters to restore the system’s network connectivity after completing all of these steps.
Launching shellcode is the installer’s main duty. This causes another obfuscated shellcode file called “2025.bin” to be launched from a hard-coded URL. This recently recovered shellcode acts as a downloader for an artifact (“output.log”), which then contacts two distinct URLs to retrieve two ZIP files:
- zip, containing a legitimate executable file and a malicious DLL that’s launched using DLL side-loading
- zip, containing a file named longlq.cl, which holds the encrypted final payload
Zscaler
| “After extracting the legitimate executable from trx38.zip, the malware will make a shortcut for it, add it to the startup folder for persistence, then run the legitimate executable to sideload the malicious DLL.”
“The final payload from the file longlq.cl is decrypted and executed by the malicious DLL. The second ZIP package that is downloaded determines the campaign’s final payload.
“Features like installing RMM utilities like Sunlogin and GotoHTTP, relaying network traffic that can be exploited to get over firewalls and VPNs, and clipboard hijacking to replace cryptocurrency wallet addresses are made possible via kkRAT’s commands and plugins.” |
A malware campaign’s attack chain that distributes many RATs.
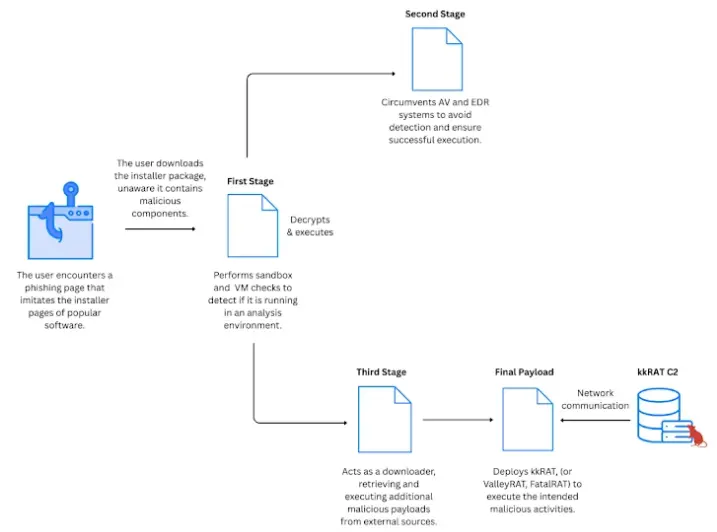
kkRAT is one of the three payloads. Once the virus has established a socket connection with the C2 server, it profiles the victim’s computer and acquires a number of plugins to carry out a variety of data collection operations.
- Recording and mimicking user inputs, including mouse and keyboard movements.
- Retrieving and altering data from the clipboard.
- Turning on remote desktop functions, like starting web browsers and stopping running programs.
- Enabling shell interface-based remote command execution.
- Turning on screen management for Windows.
- Demonstrating characteristics of process management, like the ability to list running processes and stop them when necessary.
- Creating a list of all the network connections that are active.
- Supplying tools for managing applications, like the ability to list installed programs and remove certain ones.
- Listing all of the values that are kept in the autorun Registry key and retrieving them.
- Serving as a proxy to use the SOCKS5 protocol to transit data between a client and server.
In addition to these plugins, kkRAT supports a lengthy list of commands to launch the plugins, remove data from 360 Speed Browser, Google Chrome, Internet Explorer, Mozilla Firefox, QQ Browser, Sogou Explorer, Skye, and Telegram, and act as a clipper by swapping out cryptocurrency wallet addresses copied to the clipboard.
About The Author
Suraj Koli is a content specialist in technical writing about cybersecurity & information security. He has written many amazing articles related to cybersecurity concepts, with the latest trends in cyber awareness and ethical hacking. Find out more about “Him.”
Read More:
North Korean Hackers Use ChatGPT to make Deepfake IDs for Phishing the South Korean Military








