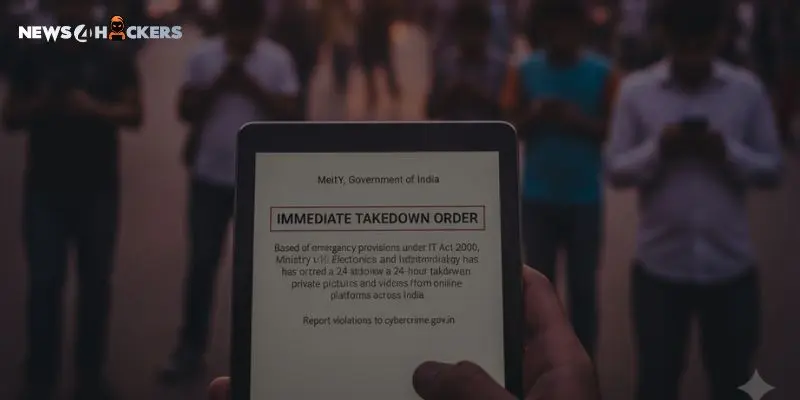
MeitY Executed 24-Hour Takedown for Private Moments’ Pics & Videos in India
“Recently, MeitY has taken a great step ahead in stopping messy pics and videos from circulating online.”
The Ministry of Electronics and Information Technology (MeitY) has released a thorough Standard Operating Procedure (SOP) requiring the prompt removal of non-consensual intimate imagery (NCII) from internet platforms within 24 hours in a historic move to protect digital dignity.
The SOP, which was unveiled on November 11, 2025, is India’s first standardized, victim-focused framework to fight deepfakes, revenge porn, and altered content in response to an increase in cybercrimes that have ruined countless lives.
In the matter of X v. Union of India (Writ Petition No. 25017/2025), the Madras High Court issued an order in July 2025 for MeitY to create a “prototype” for victims who are subjected to the distribution of private, non-consensual photos.
The court emphasized infringement of Article 21’s right to privacy and dignity by highlighting the terrifying experience of a female campaigner whose private videos went viral online. In accordance with the Information Technology (Intermediary Guidelines and Digital Media Ethics Code) Rules, 2021, MeitY’s SOP, which was submitted in October and is becoming codified, turns this judicial nudge into practical policy.
Fundamentally, the SOP provides victims with a variety of easily available reporting channels, such as direct complaints to social media sites like Instagram or WhatsApp, the National Cybercrime Reporting Portal (NCRP) helpline at 1930, One-Stop Centers (OSCs) for women, or nearby police stations.
Intermediaries have a rigorous 24-hour window to remove or disable access to NCII, which includes actual intimate images, videos, hidden camera recordings, and AI-generated deepfakes. IT Rules provide consequences for noncompliance.
The process uses hash-matching technologies to stop revival. The Ministry of Home Affairs’ Indian Cybercrime Coordination Centre (I4C) would keep a safe “hash bank” of digital fingerprints of content that has been identified, allowing platforms to automatically identify and prevent re-uploads across new URLs.
While Content Delivery Networks (CDNs) are required to immediately de-index, the Department of Telecommunications (DoT) will collaborate with Internet Service Providers (ISPs) to limit access to offending URLs. Even if the source is removed, search engines are still required to remove NCII from results.
MeitY manages the ecosystem, guaranteeing smooth stakeholder collaboration. IPC Sections 354C (voyeurism) and 66E (privacy infringement) of the IT Act include law enforcement agencies (LEAs) in criminal investigations.
Confirmation of the steps taken is given to victims, which promotes faith in a procedure that is sometimes tainted by insensitivity and delays.

Nine key forms of abuse are specifically targeted by the SOP, and each is demonstrated with scenarios that demonstrate the document’s victim-first design, demonstrating its practical applicability:
- Private Photos Shared by an Ex
After a painful split, a young woman in Mumbai finds out that her ex-partner posted pictures of her private bedroom on X (previously Twitter). She reports straight to the platform’s grievance officer since she is traumatized.
According to the SOP, the intermediary must remove the photos within 24 hours and confirm the complaint’s legitimacy, usually with the use of victim ID documentation and a declaration of non-consent. In order to stop mirror posts on Telegram channels, I4C logs the hash.
- Morphed Images Circulating on WhatsApp
When a Delhi college girl awakens, she discovers that her face has been cruelly superimposed onto a nude body and shared on more than fifty campus WhatsApp groups. She uses NCRP to dial 1930.
As a middleman, WhatsApp is required to remove the altered file from every thread that is visible and to identify similar variations using perceptual hashing. DoT prevents the transmission of viruses by blocking bulk forwarding IPs when necessary.
- Hidden-Camera Footage Posted Online
A trial-room video taken by a customer in Bengaluru using a covert phone appears on a dark-web mirror website run by a CDN. After the victim contacts her local OSC, the matter is escalated to the police and I4C.
The SOP initiates CDN takedown procedures; LEAs track the uploader in accordance with Section 66C of the IT Act, and Akamai or Cloudflare equivalents are required to remove the material globally within hours.
- Revenge Porn Uploaded on Social Media
The jilted ex of a Hyderabad influencer publicly humiliates her by posting her private movies on Instagram Reels. The 24-hour clock is started by direct reporting through Instagram’s in-app form.
In order to file a formal complaint under IPC 354A (sexual harassment), Meta must temporarily disable the account, notify the victim of its removal, and provide metadata to the cyber police.
- Deepfake Sexual Videos
On YouTube Shorts, an AI-generated video using the visage of a Chennai teacher in a pornographic scene gets popular. The SOP handles deepfakes urgently, classifying them as “artificially morphed images.”
Using tools like Microsoft’s PhotoDNA, YouTube eliminates the video, sends its hash to I4C’s bank, and uses AI crawlers to stop similar GAN-generated fakes.
- Leaked Cloud Storage Images
Reddit and 4chan display a Pune professional’s private iCloud images that were obtained through phishing. The victim reports to the cyber police out of fear of losing their job. Intermediaries work with Apple to disable the source; the SOP requires LEA to preserve evidence for prosecution under Section 67A (explicit content transfer) and notify victims within 36 hours of takedown.
- Search Engine Results Showing Intimate Content
A Kolkata victim’s leaked nude photos continue to appear in Google Image searches through cached thumbnails even after the source has been deleted. She uses NCRP to file.
According to SOP requirements, Google must de-index URLs within 24 hours and use “right to be forgotten”-style filters for NCII hashes to stop algorithmic reappearance.
- Multiple Re-Uploads Across New URLs
Using bit.ly shorteners and new domains, trolls in a coordinated harassment operation re-upload the same NCII every few hours. Hash banks are revolutionary because they use I4C-shared perceptual hashes to automatically prevent 99% of variants on sites like Facebook. DoT’s crawler technology proactively analyzes and throttles domains at the ISP level.
- Victim Is Scared or Unsure How to Report
Paralyzed by shame, a survivor in rural Rajasthan confides in a Sakhi OSC counselor. The flexibility of the SOP is evident; no technical expertise is needed. All services prioritize trauma-informed handling, OSCs file on her behalf, police offer transportation if necessary, and MeitY requires quarterly training for grievance officers.

Priya Rao, Advocate, Digital Rights
| The SOP is praised by experts as a long-overdue “systemic muscle.” “This is a reaffirmation of consent in the digital age, not just a regulation.” |
The Internet Freedom Foundation highlights privacy concerns in centralized banks while applauding hash-sharing. Siddharth Pillai of the Rati Foundation calls for changes, pointing out that the explicit-nudity concentration can leave out suggestive or semi-nude private photos.
This SOP could reduce response times from 15 days to less than 24 hours, as NCRP recorded 4,200+ NCII complaints in October 2025 alone, a 40% YoY jump. MeitY intends to raise awareness through #SafeDigitalBharat, with a goal of reaching 100 million users by March 2026.
The policy, which combines state-of-the-art technology with compassionate enforcement, indicates zero tolerance as AI deepfakes spread (I4C found 1,800 incidents in Q3). For victims, respect is now a 24-hour promise rather than a request.
About The Author
Suraj Koli is a technical writing content specialist focused on cybersecurity & information security. He has written many amazing articles related to cybersecurity concepts, with the latest trends in cyber awareness and ethical hacking. Find out more about “Him.”