Red Hat Confirms Data Breach: Hackers Steal 570 GB of Private GitHub Repositories

Red Hat Confirms Data Breach: Hackers Steal 570 GB of Private GitHub Repositories
“Hackers claimed that they have stolen around 570 GB of Data from Private GitHub Repositories, and Red Hat confirmed it.”
The top enterprise open-source software provider in the world, Red Hat, has formally acknowledged a serious security breach involving illegal access to the internal GitLab instance that the Red Hat Consulting team uses.
This confirmation follows one of the biggest source code breaches in recent cybersecurity history, in which the threat actor collective Crimson Collective claimed to have exfiltrated around 570GB of compressed data from 28,000 private repositories.

Compromised Private GitLab Repository
A GitLab environment used for Red Hat Consulting cooperation on a few client engagements was the explicit target of the intrusion.
Red Hat Official Statement
| Prior to security teams detecting the attack, the unauthorized third party was able to successfully access and copy sensitive data from this instance. |
The business promptly started a thorough investigation, blocked the attacker’s access, isolated the affected system, and got in touch with the relevant law enforcement agencies.
Sensitive technical assets such as CI/CD secrets, pipeline configuration files, VPN connection profiles, infrastructure blueprints, Ansible playbooks, OpenShift deployment guides, container registry configurations, and Vault integration secrets are purportedly included in the stolen data.
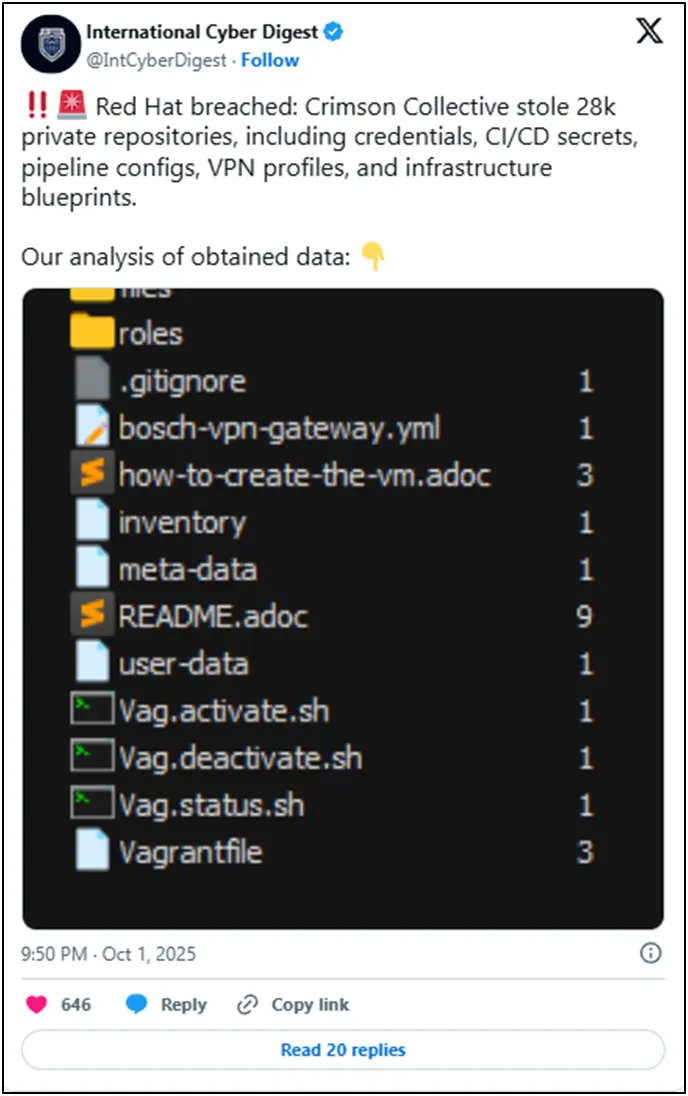
References to thousands of organizations in a variety of crucial industries have been found by security researchers examining the purported breach data. These include large financial institutions like Citi, JPMC, and HSBC; telecom behemoths like Verizon and Telefonica; industrial firms like Siemens and Bosch; and even governmental organizations like the U.S. Senate.
The hack is an example of a sophisticated supply chain attack vector that might have an effect on Red Hat’s wide range of clients.
According to reports, the compromised repositories include credential management configurations, DevOps automation scripts, and Infrastructure-as-Code (IaC) templates that adversaries may use to try secondary infiltration against Red Hat’s consulting clients.
Threat actors looking to get ongoing access to downstream systems have several attack avenues because of the compromised data’s inclusion of SSH keys, API tokens, and database connection strings.
Security experts caution that the compromised Kubernetes deployment manifests and container registry configurations may give hackers comprehensive instructions on how to target cloud-native infrastructures throughout Red Hat’s clientele.

Because GitLab CI/CD runner configurations and automated deployment pipelines frequently contain elevated rights required for enterprise software deployment and maintenance, cybersecurity experts are especially concerned about their exposure.
Red Hat said that initial analysis shows no impact on their official software distribution channels or core software supply chain, and that they have taken additional hardening measures to prevent further unwanted access.
To ascertain the complete extent of the customer impact, the business is still performing forensic analysis, and any impacted Red Hat Consulting clients will get direct notifications.
The recently revealed CVE-2025-10725 vulnerability impacting Red Hat OpenShift AI services has nothing to do with the incident.
About The Author
Suraj Koli is a content specialist in technical writing about cybersecurity & information security. He has written many amazing articles related to cybersecurity concepts, with the latest trends in cyber awareness and ethical hacking. Find out more about “Him.”
Read More:
APT35 Hackers Targeting Government, Military Organizations to Breach Login Credentials









