SVG and PureRAT Phishing Threats Attacking Ukraine and Vietnam Exposed by Experts

“Two phishing threats are attacking Ukraine and Vietnam, which have been exposed by experts.”
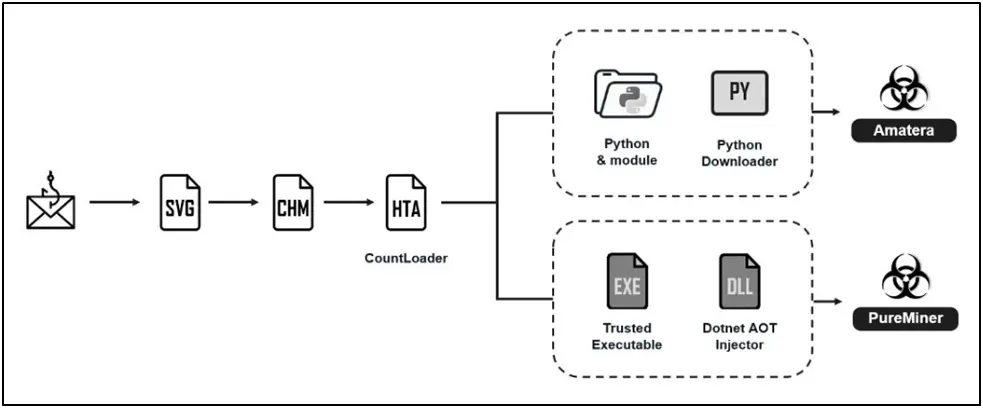
In order to deploy CountLoader, which is subsequently used to drop Amatera Stealer and PureMiner, a new campaign has been seen that poses as Ukrainian government agencies in phishing assaults.
Yurren Wan, Researcher, Fortinet FortiGuard Labs
| According to Yurren Wan, a researcher at Fortinet FortiGuard Labs, “the phishing emails contain malicious Scalable Vector Graphics (SVG) files designed to trick recipients into opening harmful attachments,” the hacker news outlet reported. |
SVG files are used to start the download of a password-protected ZIP package that contains a Compiled HTML Help (CHM) file in the attack chains that the cybersecurity firm has identified.

Launching the CHM file starts a series of actions that lead to CountLoader’s deployment. The emails purport to be a notification from Ukraine’s National Police. CountLoader has been identified to dump a variety of payloads, including Cobalt Strike, AdaptixC2, and PureHVNC RAT, according to a recent investigation conducted by Silent Push.
However, it acts as a distribution channel for PureMiner, a covert .NET bitcoin miner, and Amatera Stealer, a variation of ACRStealer, in this assault chain. It’s important to note that PureMiner and PureHVNC RAT are both components of a larger malware suite created by the threat actor PureCoder. The following are some further works by the same author:
- PureCrypter is a Native and .NET cryptosystem.
- PureRAT, sometimes known as ResolverRAT, is a PureHVNC RAT replacement.
- PureLogs is a logger and information thief.
- BlueLoader is a piece of malware that can download and run payloads remotely, functioning as a botnet.
- PureClipper is a clipper virus that uses wallet addresses controlled by the attacker to replace cryptocurrency addresses put into the clipboard in order to reroute transactions and steal money.
Both PureMiner and Amatera Stealer are distributed as fileless attacks, according to Fortinet, and are “executed via .NET Ahead-of-Time (AOT) compilation with process hollowing or loaded directly into memory using PythonMemoryModule.”
When Amatera Stealer is run, it collects system information, files that match a predetermined list of extensions, and information from browsers that are based on Chromium and Gecko, as well as programs like Steam, Telegram, FileZilla, and other cryptocurrency wallets.
Fortinet
| “This phishing campaign demonstrates how a malicious SVG file can act as an HTML substitute to initiate an infection chain.”
“In this instance, attackers used emails with SVG files to target Ukrainian government organizations. The HTML code with SVG integrated sent victims to a download website.” |

This comes after Huntress discovered a threat group that is most likely Vietnamese-speaking and uses phishing emails with copyright infringement notice themes to fool recipients into opening ZIP files that launch PXA Stealer, which then develops into a multi-layered infection sequence that drops PureRAT.
James Northey, Security Researcher
| “This attack has a clear and intentional evolution, beginning with a basic phishing appeal and progressing via levels of defense evasion, credential theft, and in-memory loaders.”
“The conclusion of this endeavor is the final payload, PureRAT, which is a professionally created, modular backdoor that grants the attacker total control over a compromised host.”
“They exhibit not only perseverance but also the characteristics of a mature and serious operator as they advance from amateurishly obfuscating their Python payloads to utilizing commercial malware like PureRAT.” |
About The Author
Suraj Koli is a content specialist in technical writing about cybersecurity & information security. He has written many amazing articles related to cybersecurity concepts, with the latest trends in cyber awareness and ethical hacking. Find out more about “Him.”
Read More:
Top 10 Cybersecurity News Websites to Follow in 2025








