Agent Racoon Backdoor Hits Firms in the Middle East, Africa, and the United States

Agent Racoon Backdoor Hits Firms in the Middle East, Africa, and the United States
An unidentified threat actor has targeted organizations in the Middle East, Africa, and the United States in an effort to disseminate the Agent Racoon backdoor.

“According to Palo Alto Networks Unit 42 researcher Chema Garcia’s analysis, this malware family is coded using the .NET framework and exploits the domain name service (DNS) protocol to establish a hidden communication channel and offer various backdoor capabilities.”
The targets of the assaults encompass a wide range of sectors including education, real estate, retail, non-profit organizations, telecommunications, and governmental entities. The activity has not been ascribed to a recognized threat actor, but it is evaluated to be associated with a nation-state due to the victimology pattern and the utilization of sophisticated ways to avoid detection and defense mechanisms.

The cybersecurity company is monitoring the group of related data or systems known as CL-STA-0002. The methods by which these organizations were compromised and the timing of the attacks remain uncertain at present.
The adversary leverages other tools such as a modified version of Mimikatz called Mimilite, and a newly developed application called Ntospy. Ntospy employs a bespoke DLL module that acts as a network provider to illicitly obtain credentials for a remote server.

“Although Ntospy was frequently employed by the attackers across the targeted organizations, the Mimilite tool and the Agent Racoon malware were exclusively detected in environments belonging to nonprofit and government-related organizations,” Garcia clarified.
It is important to note that a previously discovered group of threatening activities, referred to as CL-STA-0043, has been associated with the utilization of Ntospy. The enemy has also focused their efforts on two firms that were previously targeted by CL-STA-0002.
Agent Raccoon is a covert program that can do order execution, file uploading, and file downloading. It camouflages itself as Google Update and Microsoft OneDrive Updater binaries and is terminated through scheduled tasks.
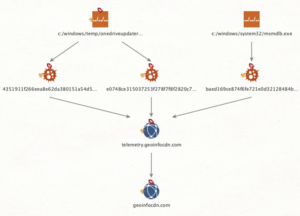
The command-and-control (C2) infrastructure utilized in conjunction with the implant may be traced back to at least August 2020. Analysis of VirusTotal submissions of the Agent Racoon artifacts reveals that the earliest sample was uploaded in July 2022.
Unit 42 has discovered evidence of effective data exfiltration from Microsoft Exchange Server installations, leading to the theft of emails that meet certain search parameters. The malicious actor has also been discovered to collect the Roaming Profile of their victims.

“According to Garcia, this tool set has not yet been linked to a particular threat actor and is not exclusively restricted to a single cluster or campaign.”
About The Author:
Yogesh Naager is a content marketer who specializes in the cybersecurity and B2B space. Besides writing for the News4Hackers blog, he’s also written for brands including CollegeDunia, Utsav Fashion, and NASSCOM. Naager entered the field of content in an unusual way. He began his career as an insurance sales executive, where he developed an interest in simplifying difficult concepts. He also combines this interest with a love of narrative, which makes him a good writer in the cybersecurity field. In the bottom line, he frequently writes for Craw Security.
READ MORE ARTICLE HERE
4 Individuals Are Arrested In A ₹1 Lakh Electricity Bill Scam By Gurgaon Police.
Former Ex-LG of Ladakh RK Mathur Duped By A Phishing Scam of ₹2 Lakh.
The Top 5 Most Dangerous Cyber Attacks of All Time






