Top 38 Best Cyber Security Tools. You Should Know in 2023!

In this article, we will be talking about some of the most popular cybersecurity tools that professionals use to enhance their security measures to protect their resources against online threats.
These popular cyber security tools are suggested by experienced cyber security experts for the security of data, networks, and systems of the practitioners working/ using the services. Within this article, you will learn about how cybersecurity tools work and the benefits of the mentioned tools. Let’s continue!
1 Astra Pentest
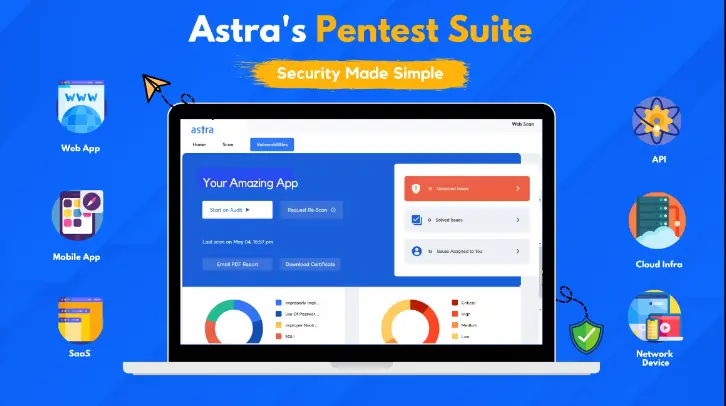
It is a platform that provides you with a combo of the Astra Vulnerability Scanner & Manual Pentesting features. You can use it as a Plug-and-Play SaaS tool by submitting the target URLs and some details.
This software made it easy for the user to perform the following tasks such as surfing on Google.
- Visualizing,
- Navigating, and
- Remediating Vulnerabilities.
2 NMAP

NMap, aka Network Mapper. Moreover, it is an open-source tool for cyber security offering scanning services for IT Systems & Networks to identify security flaws. Also, it allows practitioners to find out potential threats on networks, observe user log-in and out time, and run certain security tasks.
3 Metasploit

It offers various tools beneficial for pentesting. Practitioners utilize it for various goals, such as
- discovering vulnerabilities in systems and networks,
- designing strategies to improve the company’s Cyber Security defenses, and
- Many More.
It helps professionals to assess the system security of online & web apps, servers, networks, etc. Moreover, it can expose upcoming security risks & offer the best security solution in real time.
4 WireShark

Ethereal, a.k.a. Wireshark. It is built around a console. Additionally, it is a packet sniffer application that enables experts to examine network protocols and sniff live networks in search of exploitable flaws. Additionally, it gathers important data about the volume of network traffic.
Professionals in cyber security use this technology to store data packets and determine the traits and behaviors that each packet demonstrates. This information aids in locating network security weaknesses.
5 Nikto

It is an open-source software program designed to identify web security holes and take appropriate action. Experts use this tool to scan for,
- Identify, and
- Manage Web Vulnerabilities.
There are 6,400 different sorts of security risks in its database. The database provides threat information that can be compared to the findings of an online vulnerability scan. Web servers and networks are both included in this scan.
6 SQLmap

Finding dangers and assaults related to SQL injections is automated using SQLmap. Among all web application pentesting tools, SQLmap has a robust testing engine and supports a variety of servers, including
- MySQL,
- Microsoft Access,
- IBM DB2,
- SQLite, and
- Many More attacks.
7 Aircrack-ng

To collect data packets connected across a network for ongoing monitoring, experts use Aircrack-ng. Additionally, it enables experts to employ its features to export these data packets into comprehensible text files that can pass several security evaluations.
Additionally, Aircrack-ng supports capture and injection, which are essential for evaluating the performance of network cards. Additionally, cracking WEP and WPA-PSK keys determines how trustworthy they are and aids a company in comprehending the network’s strength.
8 Kali Linux

This OS has several helpful tools for
- Security Auditing and
- Network & System Vulnerability Scanning, etc.
One of the key benefits of this platform is that it can be used by Cyber Security experts of all levels of expertise, making it a great option even for entry-level professionals.
Additionally, many of the Kali Linux tools are simple to use and enable users to check the network security systems of an organization quickly.
9 Rapid7

Based on a thorough understanding of the techniques used by hackers to attack your systems, Rapid7 provides pentesting services.
To develop quicker, more effective security solutions, they work with the international security community. Additionally, they offer
- Vulnerability Management,
- Security Scanning, & Detection, and
- Response Services.
10 Cobalt

It is a manual tool for penetration testing that enables you to connect with pen testers in accordance with your requirements for security testing. They have tools that make it possible to complete a pentest rapidly.
This automated tool is typically used for web applications. Additionally, Cobalt’s SaaS platform enables you to receive real-time information so your teams can immediately start remediation.
11 Burp Suite

Businesses can improve their network security by using the powerful Burp Suite tool, which is utilized in cyber security. Burp Suite is used by security professionals to conduct in-the-moment system scans to locate critical flaws that could have a significant impact on a company’s security.
Additionally, it simulates assaults to discover how these threats might erode and jeopardize the network’s security. The three versions of Burp Suite are
- Community,
- Professional, and
- Enterprise.
12 Acunetix

Your websites, Online Apps, and APIs may all be secured by Acunetix. This Application security testing solution can
- Scan all Pages, Web Apps, & Sophisticated Web Apps and
- Detect over 7K Vulnerabilities.
It has capabilities for managing vulnerabilities built right in. Acunetix offers on-premises and on-demand deployment options.
13 Nessus

This tool aids businesses in enhancing network integrity and fixing several problems, such as
- Incorrectly Configuring Security Settings,
- Applying the Wrong Security Updates, and
- Numerous other Errors.
Additionally, it enables experts to identify network weaknesses like
- Software Defects,
- Improper Security Configurations in the OS, IT Devices, Software Apps, missing & incomplete updates, etc., and
- Manage them as Necessary.
14 Cain and Abel
It aids in locating Windows security holes and password recovery. Moreover, it enables cyber security professionals to identify weaknesses in the password security of various Windows-based systems.
It plays an important role by being able to record VoIP conversations and examine routing protocols to see if routed data packets are vulnerable.
15 John the Ripper

Security professionals evaluate the security of passwords using John the Ripper. Its layout makes weak passwords that endanger a specific system’s security easier to find. It was initially solely intended to run on the UNIX platform.
But recent updates have made it possible for it to run on other platforms, including
- DOS,
- Windows, and
- OpenVMS systems, etc.
To uncover any weak passwords, John the Ripper looks for challenging ciphers, encrypted login information, and hash-like passwords.
16 Tcpdump

It is a packet-sniffing networking tool. It helps with monitoring and tracking TCP/ IP traffic that is sent over a network. The network traffic passing via the network and the system traffic are both analyzed by this command-based software tool.
To assess network security, this application also separates streams of live TCP/ IP data traffic.
17 KisMAC

KisMAC was specially created to offer wireless network security in MAC operating systems. Due to its high-end features, intended to be used by industry experts, it might not be the best tool for new hires and entry-level security personnel.
Wi-Fi networks that Wi-Fi cards may access, such as those in airports, are examined by KisMAC. It breaks the security of WEP and WPA keys via
- Brute Force Assaults,
- Shoddy Scheduling,
- Exploiting Holes, and
- Numerous other Similar Methods.
18 NetStumbler

It is a well-known piece of cyber security software designed for Windows-based computers. Additionally, it makes it possible for IT and cyber security professionals to identify open network ports, which is incredibly helpful for wardriving.
It has no space for source codes because it was made particularly to run on Windows. It employs WAP-seeking techniques, in contrast to other cyber security programs, to find open-source network ports, making it popular with businesses for network defense.
19 Splunk

Because of its versatility and speed, it is a dependable system security tool. One of the greatest tools for keeping track of network security is this one. Real-time network analysis and history searches are done with Splunk to check for threat information.
A single-user interface, multiple features, and strategies that aid in the search for necessary information are all included in this user-friendly tool.
It is a comprehensive tool for system security that is used to collect, store, and index data in repositories to produce
- Real-Time Alerts,
- Reports,
- Visualizations,
- Graphs, and
- Dashboards.
20 Forcepoint

It is a tool for cloud security that enables professionals to modify SD-Wan to prevent users from accessing particular resource data. Additionally, it permits
- Blocking Invasions and
- Potential Exploitation of Vulnerabilities.
Using this App, network administrators may quickly identify harmful activity within a network and take the appropriate preventative measures. It alerts users or bans cloud servers that put the systems’ security at risk. Moreover, it also provides great security in other apps with important data.
21 Paros Proxy

It is a Java-based security tool that consists of several practical tools that experts can use to carry out security tests that reveal various web vulnerabilities. Some important tools offered in Paros Proxy are web spiders, vulnerability scanners, and the traffic collected to keep real-time network operations. It also makes it possible for professionals to spot network intrusions.
22 Intruder

Intruder is a cloud-based network vulnerability scanner that enables you to identify cybersecurity flaws in your most vulnerable systems and prevent costly data breaches.
23 ManageEngine Vulnerability Manager Plus

It is a built-in patch management program for businesses that prioritizes threats and vulnerabilities.
Additionally, from a centralized console, it is a strategic solution for providing
- Thorough Visibility,
- Evaluation,
- Remediation & Reporting of Vulnerabilities,
- Misconfigurations, and
- Other security gaps across the company network.
24 Norton Security

It offers a comprehensive solution through Norton 360 with LifeLock. The business provides cybersecurity software options such as
- Antivirus,
- Virus Removal,
- Malware Protection,
- Cloud Backup,
- Password Manager, and
- Secure VPN.
25 McAfee

It provides customers with complete security protection by combining some of the top privacy, identification, and antivirus solutions. Once installed, the app will secure you against
- Ransomware,
- Viruses,
- Phishing Scams,
- Adware,
- Malware, etc.
The nicest thing about McAfee is that one subscription covers up to ten different devices for protection.
26 Perimeter 81

The software immediately won us over after looking at its cutting-edge network security capabilities. The program provides its users various cybersecurity solutions to fortify your company’s defenses against potential threats.
The program makes it simple to manage and secure the integrity of your network with features like
- Device Posture Check,
- Online Blocking,
- Zero Trust Network Access, and
- Multi-Factor Authentication.
27 Vipre

It provides cybersecurity products for both business and personal use. It guards against
- Data Breaches,
- Ransomware, and
- Computer Infections.
It can offer the following features for company protection against online threats
- Complete Email,
- End-Point, & Privacy Security, and
- Real-Time Threat Information.
Your company & your partners are protected in multiple ways thanks to this. Platforms for Windows and Mac are supported.
28 Mimecast

It is a cloud-based platform that provides email security & cyber resilience. Moreover, it provides multiple products & services like
- Email Security with Threat Protection,
- Information Protection,
- Web Security, and
- Cloud Archiving, etc.
29 GnuPG

It is a tool for data and communication encryption and signature. Moreover, it supports
- Windows,
- Mac, and
- Linux Platforms.
30 BluVector

It offers enhanced threat detection in real-time. The foundation of this network intrusion detection system is dependent upon.
- Artificial Intelligence,
- Machine Learning, and
- Speculative Code Execution.
31 Invicti (Formerly Netsparker)

It is an enterprise-level solution for application security testing. Additionally, it provides the tools & capabilities for automated security testing throughout the SDLC. Invicti has capabilities of
- Automation,
- Visibility,
- Accuracy,
- Scalability, and
- Security.
32 Intego

It provides a full range of services that are intended to protect Windows and Mac systems from any threats. Antivirus software is available that offers real-time threat protection. The Net Barrier, which enables sophisticated firewall security, is another option. An additional option for internet privacy is a VPN.
33 Hashcat

Passwords can be cracked with this program. The hashing algorithms supported by this utility number are close to 250. This tool facilitates
- Windows,
- Linux, and
- macOS Platforms.
The key characteristics of this tool are that it is open-source, extremely quick, adaptable, and useful for performing brute-force attacks using a variety of hash values.
It can perform various cyber attacks like
- Brute-Force Attacks,
- Combinator Attacks,
- Dictionary Attacks,
- Fingerprint Attacks,
- Mask Attacks,
- Hybrid Attacks,
- Permutation Attacks,
- Toggle-Case Attacks, and
- Rule-Based Attacks, etc.
34 TrueCrypt

The application can create virtual encrypted disks in a file or encrypt an entire storage device or storage medium. Additionally, TrueCrypt, a disk encryption technology, enables security experts to encrypt multilayer content using two separate access control types.
This is one of the reasons TrueCrypt is still a widely used encryption program even after its developers stopped giving it the necessary updates.
35 KeyPass

Cybersecurity professionals primarily use it for identity management. It is extremely applicable to various business contexts. It enables system users to log into their accounts for business purposes using a single password.
Once the master password has been entered, KeyPass will automatically fill in the password to access the account. KeePass prevents this threat because poor password management is the main cause of system or network intrusions.
36 Tor

It is a very effective technique for protecting consumers’ privacy when they are online. This is accomplished by diverting user requests to many proxy servers, making it difficult to identify the users’ online activity.
Using Tor wisely ensures that a user is invisible even though there are malicious exit nodes that can be exploited to sniff internet data.
37 Bitdefender

Companies looking for full IT security against cyberattacks can rely on this tool. Several security tools are included in Bitdefender, including
- Social Network Protection,
- A Privacy Firewall,
- Safe Online Banking, and
- Anti-Phishing Tools.
More than 38% of all comprehensive security systems employ it. The malware protection software Bitdefender is compatible with
- Windows,
- Android, and
- Apple Devices.
Benefits of Cyber Security
- Protects Personal Data
Cyber security can help organizations to protect their resources against online threats that can put the reputation of companies at risk of being untrustworthy. Organizations are responsible for protecting the data, networks, and systems that carry the burden of transmitting huge amounts of data related to people, companies, and financial institutions.
With cybersecurity skills, one can protect data against online threats, such as
- Viruses,
- Malware,
- Ransomware, and
- Worms.
Helps Preserve Reputation
Goodwill is hard to preserve. With tech such as Network Security & Cloud Security, one can prevent data breaches that can happen due to unauthorized access. Moreover, it can strengthen access and authentication.
Enhances Productivity
Cyberattacks can interrupt networks, workflows, and functioning, which can definitely affect companies’ operations. Due to network interruption, adversaries can easily breach data. Moreover, it can slow down the work efficiency of the employees.
Cyber security can help protect against online threats by providing a second layer of security over the networks, security, and database.
Assists the Remote Workspace
Cyber security can help employees protect themselves against online threats, even if they are working remotely. They can provide solutions to secure their network infrastructure against online threats flowing through the network.
Mostly, IoT devices are the main target of adversaries running malicious software online to trap victims against online threats. Cybersecurity techniques can help in enhancing security measures for users.
Regulation Compliance
Working under cyber security standards can reduce the chances of cyber-attacks and data breaches, which can happen due t the negligence of compliance with necessary security measures. Following are some regulatory bodies that can strengthen the security of the users.
- HIPAA,
- SOC,
- PCI DSS, and
- GDPR.
Improves Cyber Posture
Employees have the flexibility, freedom, and security to access the internet, thanks to the comprehensive digital protection offered by cybersecurity for enterprises.
A single dashboard with sophisticated cybersecurity technology allows for the real-time tracking of all systems. By automating actions and responses in the case of a cyberattack, businesses may run more efficiently and fortify cybersecurity policies against threats.
Better Data Management
The foundation of marketing and product strategies is data. If hackers or rival businesses compromise it, the foundation may need to be rebuilt, offering rival businesses a competitive advantage.
Therefore, enterprises must continuously check their data to guarantee that data security requirements are implemented flawlessly. Cybersecurity aids in operational efficiency in addition to security.
Helps Educate and Train the Workforce
By educating the workforce about potential hazards like ransomware, data breaches, malware, and more, you can increase the level of safety in your company’s daily operations.
The staff members will be less susceptible to phishing attacks and will know what to do if something goes wrong.
Helps Maintain Trust and Credibility
Cybersecurity aids in building confidence and trust with investors and customers. The breach affects an organization’s reputation, which causes a sharp decline in audience. In contrast, a company’s customer base grows when it has a reputation for protecting both business and customer data.
Streamline Access Control
Businesses feel in control of all tasks because they have internal and external processes under control. Companies can establish accountability for strategic management by concentrating on other worthwhile responsibilities. Systematized access to devices, computers, and resources lessens the potential of cybercrime.
Supports the IT Team
Cyberattacks result in regulatory fines, consumer claims, low sales, and reduced revenue, all of which have a significant impact on continuity. Cybercrimes can also stop normal business activities.
Technology development has led to the development of advanced hacking techniques. The IT team needs to stay current with the continuously changing online.
Even the most sophisticated cybercrime can be handled expertly by an IT staff with the right tools, strategies, support, and understanding.
Conclusion for Cyber Security Tools
In the end, you must know that with the help of cyber security tools, one can secure their resources against online threats executed by adversaries for illicit means against the victims. To learn how to use the mentioned tools, there are several available sources out there.
One of the best sources is cyber security certification providers, which offers the Best 1 Year Diploma Course in Cyber Security Training in Delhi. This certification course is specifically designed to offer knowledge of cybersecurity tools and techniques to IT Professionals.
What are you waiting for? If you also want to get professional guidance in cyber security, you can join this certification course. Join Now!
Read More Article Here:
XDR: The Future of Cybersecurity
Mamata Banerjee made accusations of Hacking EVMs against the BJP during election preparation.






