Cyberattacking Indian Energy and Defense Sectors with Malware Disguised as an Air Force Invitation

Cyberattacking Indian Energy and Defense Sectors with Malware Disguised as an Air Force Invitation
Unidentified threat actors have been targeting energy businesses as well as government organizations in India with the intention of distributing a modified version of HackBrowserData, an open-source info stealer malware, and, in some instances, exfiltrating sensitive data via Slack as a command-and-control (C2) platform.

“The info stealer was transmitted by a phishing email appearing as an invitation letter from the Indian Air Force,” EclecticIQ researcher ArdaBüyükkaya stated in a report released on 27th March 2024.
“The intruder employed Slack channels as exfiltration points for uploading sensitive internal files, classified email messages, and cached web browser records after the malware’s execution.”

The initiative, which commenced on March 7, 2024, was designated Operation FlightNight by the Dutch cybersecurity company in relation to the Slack channels managed by the adversary.
The nefarious activity targets numerous government entities in India, including those that are involved in IT governance, national defense, electronic communications, and IT communications.
It is purported that the threat actor effectively infiltrated private energy firms, acquiring financial documents, employee personal information, and data pertaining to oil and gas exploration operations. A cumulative amount of 8.81 GB of data has been compromised throughout the duration of the campaign.
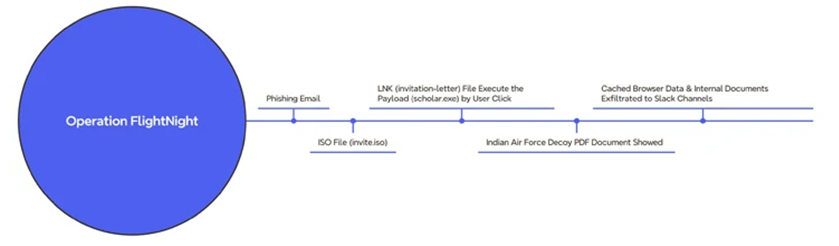
The assault series commences with a phishing message that attaches an ISO file (“invite.iso”) to the mounted optical disk image. This ISO file, in turn, comprises a Windows shortcut (LNK) that initiates the execution of a concealed binary (“scholar.exe”).
At the same time, the victim is presented with an enticing PDF file that appears as an invitation letter from the Indian Air Force. All the while, the malware stealthily acquires documents and cached web browser data, which it then transfers to FlightNight, an actor-controlled Slack channel.

The malicious software is a modified iteration of HackBrowserData, which surpasses its primary function of stealing browser data by also enabling unauthorized access to documents (including Microsoft Office, PDFs, and SQL database files), communication via Slack, and enhanced evasion of detection through the use of obfuscation techniques.

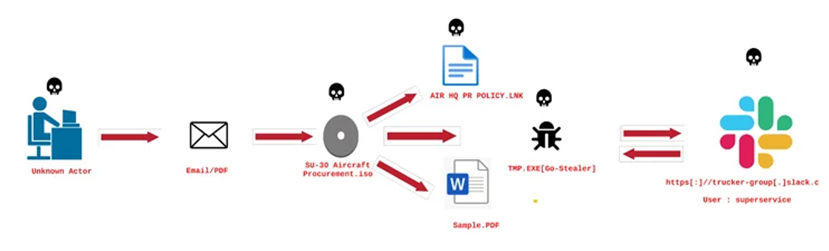
There is suspicion that the threat actor obtained the dummy PDF during a prior intrusion, as behavioral resemblances can be traced back to a phishing campaign that targeted the Indian Air Force using GoStealer, a Go-based stealer.
In the middle of January 2024, an Indian security researcher operating under the alias xelemental (@ElementalX2) divulged information regarding the activity.

The GoStealer infection sequence closely resembles that of FlightNight; it utilizes lures with a procurement theme (“SU-30 Aircraft Procurement.iso”) to trick the system into displaying a bogus file. The stealer payload is then executed to illicitly transfer sensitive data through Slack.
By modifying openly accessible offensive tools and repurposing authorized infrastructure, such as Slack, which is widely used in enterprise settings, threat actors can effectively evade detection, save time and money on development, and reduce their operational footprint.
Additionally, the increased efficiency facilitates the execution of targeted attacks, enabling inexperienced and aspiring cybercriminals to promptly exploit the situation and cause substantial harm to organizations.
“Operation FlightNight and the GoStealer operation demonstrate an easy yet successful strategy by threat actors to employ open-source tools for cyber spying,” Büyükkaya reported.

“This underlines the constantly changing environment of cyber threats, wherein attackers exploit widely used open-source offensive tools and platforms to accomplish their goals with a low risk of detection and investment.”
About The Author:
Yogesh Naager is a content marketer who specializes in the cybersecurity and B2B space. Besides writing for the News4Hackers blog, he’s also written for brands including CollegeDunia, Utsav Fashion, and NASSCOM. Naager entered the field of content in an unusual way. He began his career as an insurance sales executive, where he developed an interest in simplifying difficult concepts. He also combines this interest with a love of narrative, which makes him a good writer in the cybersecurity field. In the bottom line, he frequently writes for Craw Security.
READ MORE ARTICLE HERE





