It’s True! Hackers can Clone Toyota Hyundai and Kia Keys That Are in Millions Now
It’s True! Hackers can Clone Toyota Hyundai and Kia Keys That Are in Millions Now
Major automakers’ vehicles are disclosed due to encryption vulnerabilities in a prevalent anti-theft function.

In recent years, car owners who have keyless start systems have developed an awareness regarding relay assaults. These attacks involve hackers taking advantage of radio-enabled keys to steal vehicles undetected. Numerous millions of additional automobiles that utilize chip-enabled mechanical keys are now susceptible to high-tech larceny as well. A few cryptographic vulnerabilities combined with a well-placed screwdriver or even hot-wiring enable hackers to duplicate those keys in an instant.

Earlier this week, a group of researchers from the Universities of Birmingham and KU Leuven in Belgium and Leuven disclosed novel vulnerabilities they discovered in the encryption systems employed by immobilizers. Immobilizers are radio-enabled devices installed in vehicles that establish a close proximity connection with a key fob in order to unlock the ignition and commence the vehicle.
Specifically, they discovered flaws in the implementation of the DST80 encryption system by Texas Instruments by Kia, Hyundai, and Toyota. Staked near the key fob of any vehicle equipped with DST80, a Proxmark RFID reader/transmitter device that is comparatively inexpensive, can provide an intruder with sufficient data to deduce the secret cryptographic value of the vehicle.
This would then enable the assailant to impersonate the key inside the vehicle using the same Proxmark device, thereby disabling the immobilizer and gaining access to the engine.

According to the researchers, the Toyota Camry, Corolla, and RAV4; the Kia Optima, Soul, and Rio; and the Hyundai I10, I20, and I40 are among the affected automobile models. The following is an exhaustive list of vehicles whose immobilizers were discovered to contain cryptographic vulnerabilities by the researchers:
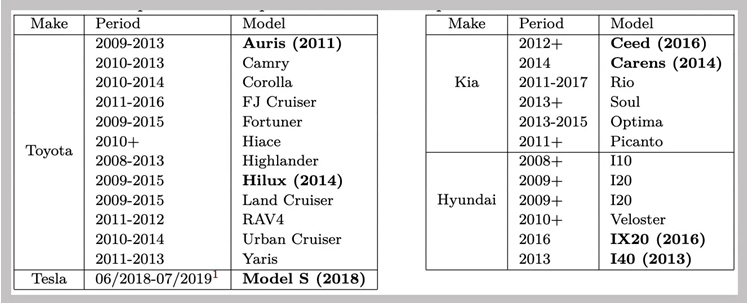
A catalog of the vehicles that, according to the researchers, are susceptible to their immobilizer-disabling assault. Despite the Tesla S being included in the list, an update was released by Tesla to mitigate the vulnerability last year. COURTESY: University of Birmingham and Ku Leuven
While the list also encompasses the Tesla S, the DST80 vulnerability was brought to Tesla’s attention by researchers last year. In response, the company issued a firmware update which effectively thwarted the attack.

Toyota has verified the existence of the cryptographic flaws discovered by the researchers. However, their method is probably more difficult to execute than the “relay” assaults that thieves have utilized repeatedly to take luxury vehicles and SUVs. A pair of radio devices is typically sufficient to extend the reach of a key fob in order to start and unlock a vehicle belonging to the victim. They can be extracted from a considerable distance, even by penetrating the walls of a structure.

In contrast, a replication attack devised by researchers from the Universities of Birmingham and KU Leuven necessitates that an assailant scan a target key fob using an RFID reader from a distance of no more than two inches. Furthermore, since the key-cloning method specifically focuses on the immobilizer as opposed to keyless entry systems, the assailant is still required to manipulate the ignition barrel, which is the cylinder into which the mechanical key is inserted.

Although this introduces an additional level of intricacy, the researchers highlight that a criminal could still manipulate the ignition switch via hot-wiring or turn the barrel with a screwdriver, just as they did prior to the advent of immobilizers, which rendered those methods obsolete. “You are regressing the security to that of the 1980s,” says Flavio Garcia, a computer science professor at the University of Birmingham. In addition, unlike relay attacks, which are only effective when the burglar is in close proximity to the original key, they can repeatedly start and operate the targeted vehicle after deriving the cryptographic value of the fob.

By purchasing a collection of electronic control units for immobilizers from eBay and reverse-engineering the firmware to determine how they communicated with key fobs, the researchers devised their method. The secret value utilized for authentication by Texas Instruments DST80 encryption was frequently compromised for far too simple a task.
Instead of DST80 per se, the issue is with the manner in which automakers implemented it. For instance, the Toyota key fobs’ cryptographic key was derived from their serial number, which was also transmitted openly via an RFID reader scan. In addition, Kia and Hyundai key fobs utilized 24 bits of randomness as opposed to the DST80’s 80 bits, which rendered their secret values easily guessed. “That is an error,” Garcia exclaims. “Twenty-four bits is a couple of milliseconds on a laptop.”

Although WIRED attempted to contact the impacted automakers and Texas Instruments for comment, neither Kia nor Texas Instruments provided a response. Hyundai, however, stated in a statement that none of the impacted models are sold in the United States. The publication stated that the organization “continues to track the area for new exploits and [makes] significant attempts to stay abreast of potential attackers.” Additionally, it advised clients to exercise caution regarding the individuals who use their vehicle’s key transmitter.

In response, Toyota issued the following statement: “The vulnerability that has been described is applicable to older models, as the configuration of current models differs.” The organization stated that “this vulnerability poses a low risk for customers, as the technique needs both the possession of the physical key anda highly sophisticated device that is not readily accessible on the market.” The researchers, in contrast, maintained that their investigation did not necessitate any apparatus that was not readily accessible.

The researchers claim that they omitted portions of their method for deciphering the key fob encryption of carmakers from their published paper in order to deter car thieves from replicating their work. However, this does not preclude less ethical hackers from potentially reverse-engineering the identical hardware that the researchers utilized in order to discover the same vulnerabilities. The researchers claim that, apart from Tesla, none of the vehicles whose immobilizers they examined could have had the program fixed with a software upgrade downloaded directly to the vehicle.
Owners could have the immobilizers reprogrammed by bringing the vehicles to dealerships; however, key fob replacement may be necessary in certain instances. (When contacted by WIRED, none of the affected automakers indicated any intention of making such an offer.)

However, the researchers assert that they chose to publish their results in order to expose the true state of immobilizer security and give vehicle proprietors the freedom to determine whether or not it is sufficient. For instance, vigilant vehicle proprietors who possess compromised immobilizers may opt to employ a steering wheel lock. “It’s preferable to be in an area where we are aware of what sort of protection we’re receiving from our security gadgets,” Garcia asserts. “Otherwise, only the criminals know.”
About The Author:
Yogesh Naager is a content marketer who specializes in the cybersecurity and B2B space. Besides writing for the News4Hackers blog, he’s also written for brands including CollegeDunia, Utsav Fashion, and NASSCOM. Naager entered the field of content in an unusual way. He began his career as an insurance sales executive, where he developed an interest in simplifying difficult concepts. He also combines this interest with a love of narrative, which makes him a good writer in the cybersecurity field. In the bottom line, he frequently writes for Craw Security.





