Rhysida Ransomware Cracked and A Free Decryption Tool Released by Cybersecurity Researchers
Rhysida Ransomware Cracked and A Free Decryption Tool Released by Cybersecurity Researchers
Researchers in the field of cybersecurity have discovered an “implementation vulnerability” that enables the reconstruction of encryption keys and the decryption of data that has been locked by Rhysida ransomware.
Last week, a team of researchers from Kookmin University and the Korea Internet and Security Agency (KISA) released their findings.

The researchers stated that they were able to identify an implementation flaw in Rhysida Ransomware, which allowed them to recreate the encryption key utilized by the malware.
This achievement signifies the initial and effective deciphering of the ransomware variant, which initially emerged in May 2023. KISA is distributing a recovery tool.
This study is the most recent to successfully decrypt data by exploiting vulnerabilities in the implementation of ransomware, following the examples of Magniber v2, Ragnar Locker, Avaddon, and Hive.

Rhysida, a ransomware group that has similarities with another group named Vice Society, uses a strategy referred to as double extortion to coerce victims into paying by threatening to expose their stolen data.
In November 2023, the U.S. government issued an advisory highlighting the threat posed by opportunistic attackers who are carrying out targeted attacks on education, manufacturing, information technology, and government agencies.
An extensive analysis of the ransomware’s internal mechanisms has uncovered its utilization of LibTomCrypt for encryption, along with the implementation of parallel processing to enhance the speed of the operation. Furthermore, intermittent encryption (also known as partial encryption) has been discovered as a means to avoid detection by security systems.
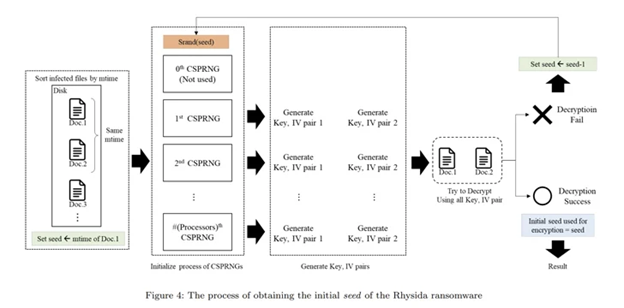
The researchers stated that Rhysida ransomware used a Cryptographically Secure Pseudo-Random Number Generator (CSPRNG) to create the encryption key. This generator employs a cryptographically robust approach to produce random numbers.
The CSPRNG is derived from the ChaCha20 algorithm implemented in the LibTomCrypt library. Additionally, the produced random numbers are influenced by the current time when the Rhysida ransomware is active.

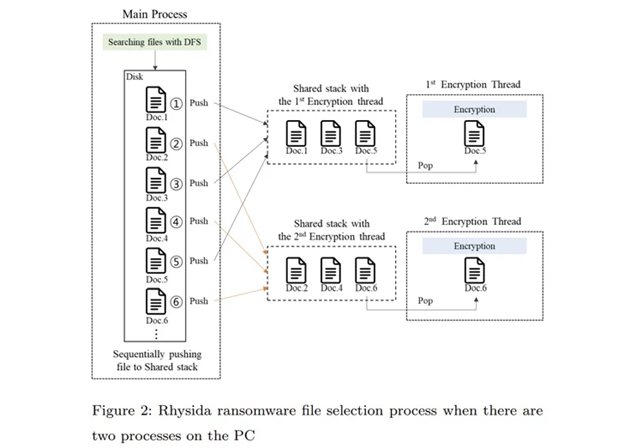
Despite the randomness of the generated numbers, the primary operation of Rhysida ransomware involves creating a list of files to be encrypted. This list is then used by many threads to encrypt the files in a specified sequence.
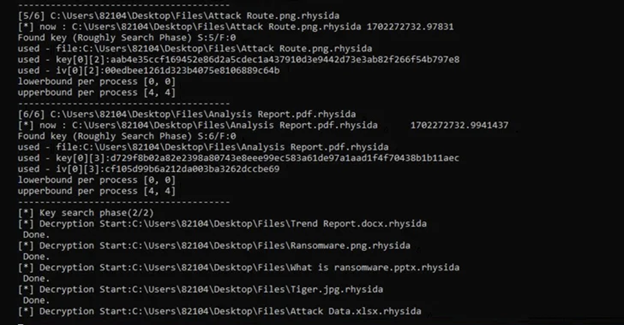
The researchers observed that throughout the encryption procedure of the Rhysida ransomware, the encryption thread produces 80 bytes of random values for each file that is being encrypted. “Out of these, the initial 48 bytes serve as the encryption key and the initialization vector.”

By utilizing these findings as benchmarks, the researchers successfully obtained the original key for decrypting the ransomware, identified the seemingly random sequence in which the files were encrypted, and eventually restored the data without the need to make a ransom payment.
The researchers stated that while these investigations have a restricted focus, it is crucial to recognize that specific ransomware can indeed be decrypted with success.

Update
After the news was published, security researcher Fabian Wosar revealed that the vulnerabilities were discovered by “at least three other entities, who opted to share the information privately instead of making it public and notifying Rhysida about the issue.”

“Avast discovered it in October of the previous year, the French CERT wrote and released a confidential document about it in June, and I identified the vulnerability in May of the previous year,” stated Wosar. “I am not familiar with the Avast and CERT data, but since then, we have successfully decrypted hundreds of systems.”
“Additionally, it is important to note that the paper specifically pertains to the Windows PE version of the Rhysida ransomware.” This does not pertain to the ESXi or the PowerShell payload.
About The Author:
Yogesh Naager is a content marketer who specializes in the cybersecurity and B2B space. Besides writing for the News4Hackers blog, he’s also written for brands including CollegeDunia, Utsav Fashion, and NASSCOM. Naager entered the field of content in an unusual way. He began his career as an insurance sales executive, where he developed an interest in simplifying difficult concepts. He also combines this interest with a love of narrative, which makes him a good writer in the cybersecurity field. In the bottom line, he frequently writes for Craw Security.





