Top 10 Ethical Hacking Gadgets: Your Ultimate Toolkit for Cybersecurity

Top 10 Ethical Hacking Gadgets: Your Ultimate Toolkit for Cybersecurity
Occasionally, in the context of security audits, it is possible to come across a scenario wherein all aspects are being effectively controlled. Various approaches, such as implementing security patches, adherence to policies, network segmentation, utilization of antivirus software, and promotion of user awareness, among others, are being effectively employed. At this juncture, in order to further examine the subject matter through the lens of a security researcher or consultant, the significance of social engineering and various other tools, which will be explored in this discourse, becomes more pronounced. These Ethical hacking Gadgets may be the sole means by which an attacker can successfully infiltrate the targeted system.
These Ethical Hacking Gadgets mostly consist of hardware components specifically engineered for the purpose of conducting security research or engaging in related tasks. Presented below is a comprehensive compilation of the ten essential tools that are required for white hat hackers.
Here, we will try to know more about the Top 10 Ethical Hacking Gadgets that can be very beneficial for ethical hacking professionals for long-term usage to track down every single flaw in the security posture of any IT interface.
#1 Raspberry Pi 3

Currently, we find ourselves in the third generation of these cost-effective computing devices, which possess versatile functionality. An exemplary illustration in security audits is the utilization of a Raspberry Pi device, accompanied by a suitable battery pack, a distribution platform such as Kali Linux, and programs like FruityWifi. This combination together functions as a versatile tool for penetration testing, akin to the multifunctional Swiss army knife.
#2 WiFi Pineapple

The assortment of tools designed for conducting wireless penetration tests becomes highly advantageous in executing a range of attacks, including the man-in-the-middle attack. The platform offers a user-friendly online interface that facilitates connectivity across many devices, including smartphones and tablets. The software is notable for its user-friendly interface, efficient organization of tasks, comprehensive data presentation, and the capability to simulate many sophisticated assaults with no effort.
The WiFi Pineapple platform facilitates the utilization of numerous modules, which are consistently being developed by the user community. This ongoing development process contributes to the incorporation of novel features that expand the platform’s range of capabilities. An additional advantage is that these modules can be easily installed at no cost using the web interface within a few seconds.
#3 Alfa Network Board
A conventional Wi-Fi board designed for the purpose of packet injection. The Alfa is notable for its utilization of high-quality materials and incorporation of chipsets that can be configured into monitoring mode, a necessary feature for conducting wireless audits.
#4 Rubber Ducky

The mentioned “special” pen drive is a programmable keyboard gadget designed in the form of a USB drive. Upon connecting the device to a computer, it initiates an automatic writing process to execute programs and tools. These programs and tools can either be pre-existing on the targeted computer or stored within the device’s onboard Micro SD card. The purpose of this operation is to extract information from the computer.
In the popular television series Mr. Robot, viewers may recall that in the second season, the character Rubber Ducky becomes a pivotal role as an ally to Angela, aiding her in obtaining the passwords of an executive at E Corp.
#5 LAN Turtle

This particular system administration and penetration testing tool offers inconspicuous remote access by maintaining a concealed connection to a USB port. In addition, it enables users to gather data from the network and possesses the capability to carry out a man-in-the-middle assault.
#6 HackRF One

This tool facilitates the installation of a robust Software-Defined Radio (SDR) system. In essence, the device can be described as a radio communication apparatus that deploys software as a substitute for conventionally installed hardware components. In this manner, the device exhibits the ability to effectively process a wide spectrum of radio signals, spanning from 10 MHz to 6 GHz, utilizing a singular peripheral that can be conveniently linked to the computer through a USB port.
#7 Ubertooth One
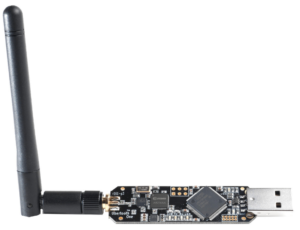
The Ubertooth One is a device that is widely used in the field of wireless security research and analysis.
The device in question is a code development platform operating at a frequency of 2.4 GHz, which is open-source in nature. Its primary purpose is to facilitate experimentation with Bluetooth technology, thereby allowing users to gain a comprehensive understanding of the many components and functionalities associated with emerging wireless technologies.
#8 Proxmark3 Kit

The Proxmark3 Kit is a hardware and software tool used for conducting research and analysis on various RFID and NFC systems. It is designed to provide users with the ability.
The Proxmark3 is a device designed by Jonathan Westhues, which possesses the capability to effectively scan and replicate a wide range of RFID (radio frequency identification) labels, in addition to intercepting their signals. Additionally, the device has the capability to function independently, without the need for a personal computer, by utilizing batteries.
#9 Lockpicks

It is crucial to acknowledge that in certain nations, the possession of lockpicks is considered a criminal offense. It is not advisable to engage in any conduct that may be in violation of legal statutes. It is advisable to ensure compliance with the legislation in your respective nation before obtaining any of the aforementioned instruments. This recommendation also extends to the other devices mentioned within the context of this article.
The aforementioned instruments serve as the primary apparatus utilized in the practice of lockpicking, which refers to the skill of accessing a lock or physical security mechanism by means of logical analysis or manipulation of its constituent parts in the absence of the original key. There exists a wide range of sizes and formats for kits, which, in numerous instances, have the potential to compromise physical security.
#10 Keylogger
A traditional method for recording keystrokes. This gadget offers connectivity options through USB or PS/2 interfaces, facilitating a discreet linkage between the keyboard and personal computer, thereby recording every keystroke made. Undoubtedly, it often eludes detection by the majority of security systems.
Although Christmas is still a while away, you may be inclined to consider gifting yourself with these items. They are certain to provide you with ample opportunities for testing and experimentation. Furthermore, it is important to consider that in subsequent penetration tests, these vulnerabilities may serve as potential entry points to infiltrate a seemingly impervious target.
Wrapping Up
In a nutshell, we have tried our level best to deliver you the Top 10 Ethical Hacking Gadgets or tools that every Ethical Hacker deserves to have in their toolkit. However, if there are any devices that have been overlooked, kindly provide your input in the comments section, along with a rationale for why you believe they should be included in this list.
For the same sake, you can contact the author.
About The Author:
Yogesh Naager is a content marketer who specializes in the cybersecurity and B2B space. Besides writing for the News4Hackers blog, he’s also written for brands including CollegeDunia, Utsav Fashion, and NASSCOM. Naager entered the field of content in an unusual way. He began his career as an insurance sales executive, where he developed an interest in simplifying difficult concepts. He also combines this interest with a love of narrative, which makes him a good writer in the cybersecurity field. In the bottom line, he frequently writes for Craw Security.
Read More Article Here