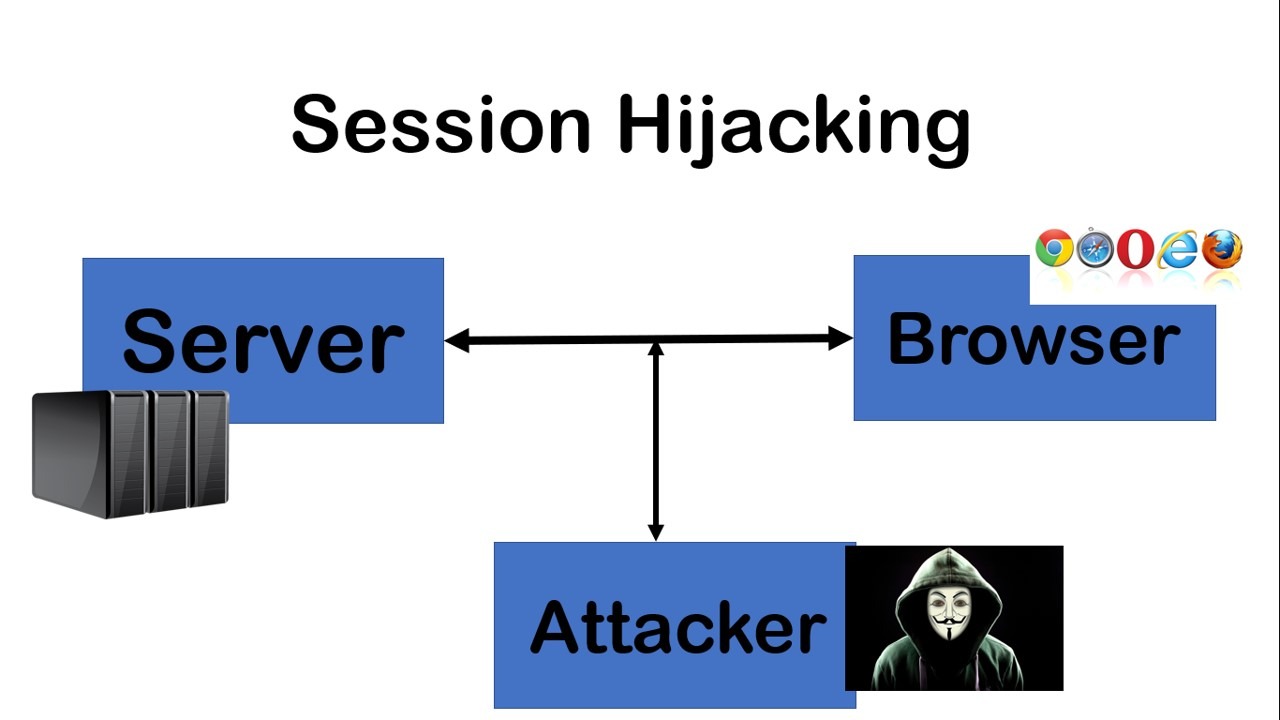
What is session hijacking?

What is session hijacking?
Session hijacking is a type of network attack that has existed for some time. Hackers use the underlying Internet technology to perform this kind of attack, so this kind of attack is unlikely to disappear anytime soon. Although it is often too late to discover session hijacking, users can still take some measures to protect their connection and data security.
Sessions and Cookies
As long as you go online, the website you visit and your browser will start a session. They exchange information to identify each other, and the website sends session cookies (and other content) to verify identities throughout the session.
Cookies are small files that contain information about users. For example, after leaving the page, the session cookie will allow the online store to continue to obtain the information in your shopping cart. Due to the existence of cookies, the online form will provide suggestions based on what you previously entered. This also tailors the way of advertising for you: Look at a pair of sneakers on Amazon, and their images will appear when you browse the Internet for several days.

Cookies can be annoying, but they can also bring a lot of conveniences. You don’t have to log in every time you visit a social network, and you don’t need to put items in your shopping cart every time. Pages you visit frequently will also load faster. Unfortunately, if you are not careful, cookies may cause you trouble.
How does session hijacking work?
In essence, a session hijacking attack is a type of cookie theft. If you log in to your social media account on the library computer, the website will send a session cookie to keep you logged in on the next page. If someone steals this cookie, they may pretend to be you and cause a lot of damage.
The attacker may see all the information in your account, such as your name, email address, phone number, address, credit card details, etc. They can buy some goods and pay with your bank card, or they can use phishing links to send spam to your contacts.
Types of session hijacking
There are several different ways to perform session hijacking:
Session bypass hijacking: This can happen when you are connected to an unsecured network (such as public Wi-Fi). The attacker can intercept or eavesdrop on the connection and then see what other people on the same network are doing online. If the website you visit is not encrypted using TLS, the snooper can see everything you do on the website-including your session cookies. Therefore, even after you disconnect, the attacker can still continue your session.
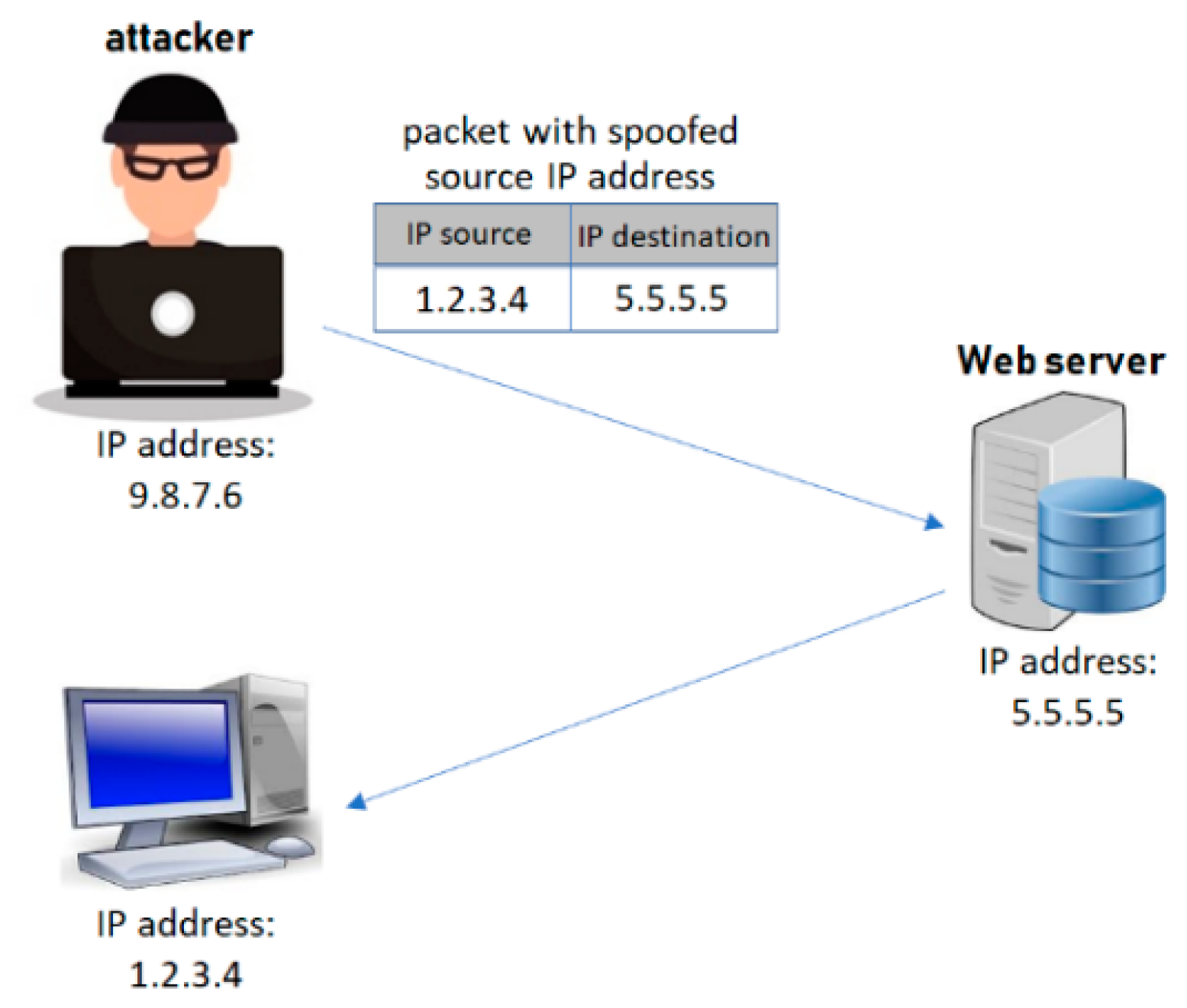
IP spoofing: Man-in-the-middle attacks are checked here, similar to session bypass hijacking. Attackers use this type of technique to pretend to be you from the beginning. When you try to connect to a website, you need to perform a TCP handshake. If you connect via an insecure Wi-Fi connection, the hacker will intervene in this three-way handshake immediately before the third step. They will use (impersonate) your IP address to fool the server, make the server think they are you, and perform the third part of the TCP handshake. After this, they can receive all cookies and communicate with the website on your behalf.

Brute force attack: It works in the same way as all brute force attacks. Cybercriminals will try all possible session tokens and hope to be able to guess the correct token and control your account.
The session is fixed: This can happen when you are connected to an unsecured network (such as public Wi-Fi). The attacker can intercept or eavesdrop on the connection and then see what other people on the same network are doing online. If the website you visit is not encrypted using TLS, the snooper can see everything you do on the website-including your session cookies. Therefore, even after you disconnect, the attacker can still continue your session.
This is how it works
- Never connect to insecure Wi-Fi. Use your own mobile data connection during coffee breaks-this way Zuo is much safer. If you do need to connect to a public hotspot, please do not enter any personal information, such as login credentials or credit card details.
- Before downloading each application or software, please check each part of it. Make sure that the developer is trustworthy and that the application and software itself are not a trap. Some apps are very realistic in design, but once you install them, malware will take over your device.
- Get anti-malware tools to protect your device. It can not only terminate any session hijacking attempts but also ensure the safety of your data and online accounts.
- Be cautious when surfing the Internet. Phishing and threatening software will judge our judgment based on our emotions. If you receive an email telling you that someone is trying to log in to your account, you should act immediately. Please do not click the link lightly. Check the sender — does it look like a legitimate email address? Are there any typos in the text? Does the font look wrong? If any abnormality is found, it may be a fraudulent email. You should open a new tab and log in to the account that claims to have been hacked to see if the hacking has actually occurred.
To know more about DDoS Attack. Click Here