25 Best Kali Linux Tools

25 Best Kali Linux Tools
Introduction:
25 Best Kali Linux Tools- Kali Linux is a security-focused Linux distribution designed specifically for digital forensics and penetration testing. Kali Linux, which is derived from the Debian Testing branch, strikes a harmonious equilibrium between ensuring system stability and providing the most recent software releases.
This summary features the top 25 Kali Linux Tools, selected from a pool of more than 600 applications included in the distribution.
1. Nmap
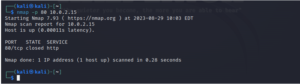
Utilized from the command line, Nmap is a network reconnaissance application that maps and discovers hosts, networks, and services. It assists users in conducting vulnerability assessments of networks and enhancing network security.
By transmitting data packets to a specified port and IP address, Nmap operates. It analyzes the response it receives before generating a report.
Features
- Host identification on a network via port or protocol.
- Perform a ping scan to verify the host.
- Rapid scan to expedite port scanning.
- TCP/IP stack fingerprinting locates the operating system and hardware components of a network device.
Pricing
Nmap is an open-source and cost-free application.
2. Netcat
Netcat is a command-line tool that enables users to transfer data over network connections by both reading and writing. The program conducts port scanning and listens for incoming connections, facilitating file transfers over the TCP and UDP protocols.
The tool serves to streamline the process of debugging and research, allowing developers to integrate it into the backend of their programs and scripts. The syntax of Netcat encompasses a range of parameters that facilitate communication and analysis of external websites and their corresponding ports.
Features
- Connections to TCP/UDP over any port.
- Randomized port scanning is implemented.
- Complete DNS reverse and forward testing.
- The utilization of a source port or network address that is locally configured.
- Deactivate source-routing.
- Mode of TCP/UDP tunneling.
Pricing
Netcat is an open-source and cost-free application.
3. Fluxion
Fluxion is a software application designed for the purpose of conducting security audits and studying user reactions to social engineering assaults. This software is capable of executing Wi-Fi access point attacks by offering a user-friendly interface for establishing counterfeit wireless networks.
In addition to the social engineering aspect, security professionals employ Fluxion to assess the security of wireless networks’ access points by simulating Man in the Middle (MITM) attacks.

Features
- Utilize Handshake Snopper and Captive Portal to simulate a Man-in-the-Middle (MITM) attack.
- Instances of malicious impersonation, known as Evil Twin assaults, occur.
- Phishing for personal credentials.
- De-authentication attacks.
Pricing
Fluxion is a tool that is both free and open-source.
4. Lynis
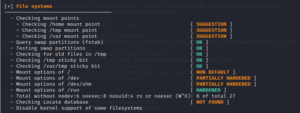
Lynis is a tool used for system hardening and compliance testing. It does thorough inspections to assess the overall health of a system. In addition to IT security professionals, developers employ Lynis to enhance web application security, while sysadmins employ it to uncover novel vulnerabilities.
Lynis has an opportunistic and modular methodology for scanning, enabling it to detect and utilize existing system tools and subsequently execute a customized system assessment. Lynis is able to operate without any dependencies due to this method.
Features
- More than 300 pre-installed tests.
- Support for plugins and customized tests.
- Real-time identification of the operating system.
- Comprehensive logging.
- Index of strengthening.
Pricing
Lynis is a cost-free and open-source software. In addition, there are two Software-as-a-Service (SaaS) options available for Lynis:
- The Premium package encompasses all the modules and entails a monthly membership.
- The Self-Hosted option enables consumers to tailor the offering according to their own requirements.
5. Nessus
Nessus is an extensive tool used for vulnerability assessment, which involves the identification of vulnerabilities, misconfigurations, and possible threats in systems and applications. It provides a comprehensive repository of frequently updated vulnerability checks for current security evaluation.

Features
- Asset discovery that is rapid.
- Performing configuration audits.
- The disclosure of confidential information.
- Anti-malware software.
Pricing
Nessus is a commercially available product that provides three different versions:
- Nessus Essentials is a complimentary edition that allows users to examine their surroundings using a maximum of 16 IP addresses per scanner.
- Nessus Professional is a premium yearly membership plan that includes all the necessary modules.
- The Nessus Expert annual membership encompasses the functionalities of Nessus Professional, along with further capabilities including external attack surface scanning, prebuilt scanning rules, and cloud infrastructure scanning.
6. Tiger
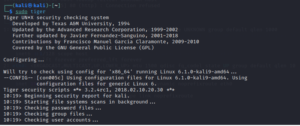
Tiger is a shell-based command-line utility that conducts security audits and detects intrusions on the host system. Additionally, it can serve as a structure for integrating various tools such as intrusion detection systems, integrity checkers, and log checkers.
Users have the ability to choose which specific feature of a UNIX system they wish to examine due to the modular design of the application. For instance, Tiger has the capability to verify filesystem permissions, identify inactive users, and examine the configuration of system files. Additionally, it has the capability to check for patches that are available but have not been put on the system.
Features
- Expandable modular construction.
- Inexhaustible selection of tests.
- Vulnerabilities in password policies, system logs, and network configurations are brought to light.
Pricing
Tiger is a free and open-source tool.
7. John the Ripper
John the Ripper, commonly referred to as John is a password-cracking utility that features a straightforward command-line interface. Cybersecurity experts employ it to conduct password security audits and recover lost passwords.

Features
John the Ripper is compatible with a wide range of hash and encryption types, including:
- Authentication credentials for Linux, BSD, macOS, and Windows users.
- Authentication credentials for online applications and database servers.
- Packet captures of network traffic.
- Private keys that have been encoded using encryption algorithms.
- Filesystems, documents, and archives.
Pricing
Although the application is available for free, there are also premium versions of John the Ripper Pro that are specifically designed for certain operating systems. The license and pricing are contingent upon the operating system and the specific package type.
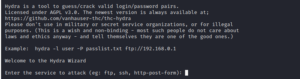
8. Hydra
Hydra is a software tool used for cracking passwords. It is capable of simultaneously connecting to and attacking several protocols. It employs a combination of different brute-force attack methods to attempt to guess the username/password combination.
Penetration testing professionals frequently employ Hydra in conjunction with wordlist generators like Cupp and Crunch.
Features
- Multiple protocols are supported, including FTP, SSH, POP3, and IMAP.
- Assistance with website forms.
- Modular construction.
- Brute-force and dictionary-based attacks.
- Parallel assaults.
- Assistance with custom scripts.
Pricing
Hydra is an open-source, no-cost application.
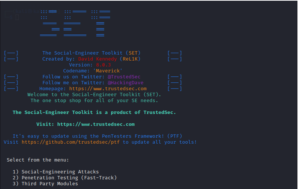
9. Social-Engineer Toolkit (SET)
The Social-Engineer Toolkit (SET) is a Python-based penetration testing toolkit designed for doing social engineering research. Security professionals can utilize this tool to construct a convincing social engineering attack by employing personalized attack vectors.
SET assists security experts in assessing the vulnerability of organizations and individuals to phishing, credential harvesting, and manipulation.
Features
- Provision for a multitude of attack vectors, including spear phishing and credential harvesting.
- Transmission of infectious media.
- Building phishing websites.
- Assaults based on email.
- Creation of malicious USB devices.
Pricing
Social-Engineer Toolkit is a cost-free and open-source project.
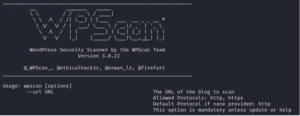
10. WPScan
WPScan is a utility designed to identify vulnerabilities, misconfigurations, and security concerns in WordPress websites. It verifies the status of a website by cross-referencing against a manually updated database of WordPress vulnerabilities.
WPScan can be incorporated into a WordPress installation or utilized as a command-line interface (CLI) tool. The CLI tool provides a straightforward interface that includes the wpscan command.
Features
- Examining code, themes, and modules that have become obsolete.
- Weak passwords, exposed sensitive data, and prospective entry points are inspected for security purposes.
- Verification of the WordPress installation and plugin versions.
- Brute-force attacks are utilized to verify login credentials.
Pricing
The command-line interface (CLI) version of WPScan is available at no cost, however, it has a restriction of 25 API queries per day. The Enterprise edition is a premium offering that requires payment and provides tailored solutions specifically designed for large organizations.
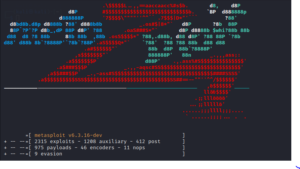
11. Metasploit Framework
The Metasploit Framework is a comprehensive framework used for conducting penetration testing, as well as a versatile platform for developing security tools and exploits. It provides the user with the ability to execute all the essential procedures for creating and deploying an exploit within a unified environment.
Metasploit simplifies the process of creating, evaluating, and running exploit code. It facilitates tasks such as configuring the exploit module, pairing it with the payload, and initiating the exploit on the target system.
Features
- A comprehensive repository of auxiliary modules, payloads, and exploits.
- Permits privilege escalation and remote code execution (RCE), among other exploits.
- An array of security assessment alternatives.
- Generate custom exploits and payloads with ease.
- Post-exploitation modules that enable the exploited system to perform reconnaissance, data extraction, and lateral movement.
Pricing
Although open source and free to acquire, Metasploit Framework only includes the bare minimum of functionality. In addition, the organization provides a paid alternative known as Metasploit Pro, which encompasses further sophisticated functionalities.
12. Burp Suite
Burp Suite is a comprehensive platform designed for the purpose of identifying vulnerabilities and doing security testing on online applications. The suite streamlines repetitious work in all tests and enables users to conduct more thorough examinations using manual and semi-automated testing methods.
Burp Suite endeavors to offer a comprehensive solution for assessing the security of web applications. It offers fundamental functionality by serving as a proxy server, scanner, and intruder. Additionally, it can perform as a repeater, decoder, sequencer, and comparer. The premium versions provide other functionalities, like an extender and a spider.
Features
- Ingenious automation.
- Assistance with HTTP/2 testing.
- OAST is an approach to application security that aims to reduce the occurrence of false positives.
- APIs and single-page applications (SPAs) are being scanned.
- Prerecording of sequences of intricate authentication.
Pricing
Although Burp Suite Community Edition is provided at no cost, it is incredibly limited in functionality. Following a trial period, the Professional and Enterprise editions become available for purchase.
13. Aircrack-ng
Aircrack-ng is a Wi-Fi security tool used for assessing the security of wireless networks. It assists users in identifying, capturing, and analyzing Wi-Fi network data. The device comprises a detector, a packet sniffer, a password cracker, and a wireless LAN analysis tool.
Features
- Keys for WEP, WPA/WPA2, and WPA2 cracking.
- A tool for injecting and replaying frames that facilitates de-authentication attacks.
- The packet analyzer is a device.
- Wireless server for cards.
- Creator of virtual tunnel interfaces.
- Automated WPA handshake logging and WEP decryption.
Pricing
Aircrack-ng is an open-source, no-cost application.
14. Nikto
Nikto is a tool used to evaluate the security of web servers and apps by scanning for vulnerabilities. It conducts scans of online environments to identify potential vulnerabilities, misconfigurations, and security issues.
Nikto, being a command-line program, utilizes the nikto command to accept IP addresses and domain names as inputs. Upon doing an analysis of the server associated with the given address, the program generates a comprehensive report that includes fundamental details about the target and a catalog of possible vulnerabilities.

Features
- Detects security issues, misconfigured servers, and obsolete software.
- Identifies and scans in excess of 6700 malicious files and CGIs.
- Complete SSL support.
- Full support for HTTP proxies.
- Port scanning is performed using a Nmap file as input.
Pricing
Nikto is an open-source and cost-free application.
15. Autopsy
Autopsy Forensic Browser is a sophisticated software tool used in the field of digital forensics. It is designed to retrieve and analyze information from various digital devices and data sources. Autopsy is a widely utilized tool by forensic professionals and law enforcement authorities. It allows for the examination and retrieval of data from different file systems.
Autopsy is installed using the Command Line Interface (CLI) and can be accessed through a web interface.
Features
- Learning concealed or expunged data.
- Robust keyword search functionalities.
- Analysis of timelines offers valuable insights into the activities of users.
- Integrating cipher databases for the purpose of verifying file integrity.
- Hash filtering to identify known malicious files.
- Facilitation of diverse data types.
Pricing
- Autopsy is a free and open-source application.
16. King Phisher
King Phisher is a software application that is used to simulate and carry out phishing campaigns with the purpose of evaluating and enhancing security awareness. It aids enterprises in assessing their vulnerability to phishing assaults.
King Phisher is a versatile tool that may be utilized for a range of purposes, including basic education on security awareness and elaborate demonstrations of the risks associated with credential harvesting. The user has control over emails and server content due to the adaptable design.

Features
- Permission to conduct concurrent spoofing campaigns.
- Landing page harvesting of credentials.
- Copies of web pages.
- SPF (Integrated Sender Policy Framework) evaluations.
- Images that are embedded in emails.
- Two-factor verification.
Pricing
King Phisher is an open-source and cost-free program.
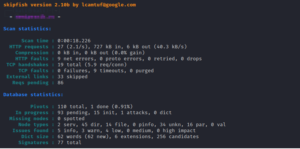
17. Skipfish
Skipfish is a software program designed to evaluate and analyze the security of web applications. It facilitates security reconnaissance by performing a systematic search and analysis of a website’s structure and content, utilizing a recursive crawl and dictionary-based probes, ultimately generating an interactive map of the target website.
The user commences a Skipfish scan by specifying a target website via its command-line interface.
Features
- Modular construction with adaptable features.
- Content compression, keep-alive connections, and range requests.
- Required response size restriction.
- Enumeration monitoring.
- Potential vulnerabilities, including SQL injection and cross-site scripting (XSS), are identified.
Pricing
Skipfish is an open-source application, and it is free to use.
18. BeEF
The Browser Exploitation Framework (BeEF) is a framework designed to evaluate the security and vulnerability of web browsers. It detects vulnerable aspects of web browsers and assists users in developing effective defenses for web applications.
BeEF operates by intercepting a web browser and using it as a beachhead, which serves as a strategic point of attack for carrying out targeted command modules and other associated attacks. This operation grants the security expert the ability to exert restricted control over the end user’s browser tab and carry out a simulated attack for testing purposes.

Features
- Focusing on weaknesses like cross-site scripting (XSS) and HTML injection.
- Exploiting vulnerabilities specific to certain web browsers through tailored attacks executed within the browser.
- The extension API and restful API.
- Utilizing a browser proxy.
- Integration of Metasploit.
- Identification of plugins.
Pricing
BeEF is a free and open-source tool.
19. Wireshark
Wireshark is a software application used for examining and interpreting network packets to identify and resolve issues in computer networks. The program has the capability to record and analyze network traffic in real-time, as well as analyze packets that have been captured in the past. The study provides a valuable understanding of network behavior and enables the detection and identification of potential security risks.
The primary Wireshark program is graphical user interface (GUI) based. Nevertheless, there exists a command-line iteration known as TShark.
Features
- Capturing data in real-time.
- Data retrieval from loopback, Ethernet, IEEE 802.11, and PPP networks.
- Implement filters.
- Plugin compatibility.
- Call detection via VoIP.
- Raw USB data acquisition.
Pricing
Wireshark is an open-source and cost-free program.
20. Yersinia
Yersinia is a tool used for exploiting network protocols by simulating and testing attacks against them. It carries out Layer 2 assaults by impersonating a stable framework for testing and analyzing deployed networks and systems.
Features
Yersinia encourages the following protocols for attack:
- Cisco Discovery Protocol (CDP).
- Dynamic Host Configuration Protocol (DHCP).
- 1q and 802.1x.
- Dynamic Trunking Protocol (DTP).
- Hot Standby Router Protocol (HSRP).
- Inter-Switch Link Protocol (ISL).
- VLAN Trunking Protocol (VTP).
- Spanning Tree Protocol (STP).
Pricing
Yersinia is an open-source and cost-free application.
21. Maltego
Maltego is a sophisticated tool that combines intelligence and data visualization to collect and analyze data from many sources, revealing connections and patterns. The software offers a collection of data discovery transformations and a graph-based representation of the data, suitable for data mining and link analysis purposes.

Features
- Simplified the process of collecting data from disparate sources.
- One million or more entities may be observed on the map.
- Combining and linking map data automatically.
- Recognition of patterns encompassing organic, block, hierarchical, and circular configurations.
Pricing
Maltego Community Edition is available for no cost, but, registration is necessary. The premium variants, Maltego Pro and Maltego Enterprise, offer supplementary functionalities. This encompasses utilizing the tool across various devices, implementing it within virtual machines, and accessing supplementary transformations through the commercial Transform Hub.
22. Apktool
Apktool is a software tool that enables users to perform reverse engineering on Android APK files. It deconstructs resources and offers a means to modify or examine the deconstructed application.
Features
- Resources, assets, and code are extracted.
- Enables the analysis of XML files, images, and layouts.
- Converts the code to APK format.
Pricing
Apktool is open-source and free to use.
23. SQLmap
Sqlmap is a tool used to identify and attack SQL injection vulnerabilities in web applications and databases. This program simplifies the process of identifying vulnerabilities and provides assistance in executing database server takeovers.
Features
- Manual and automated SQL injection testing.
- A variety of database management systems (DMS) are supported, including MySQL, PostgreSQL, MariaDB, SQLite, and Microsoft SQL Server, among others.
- Error-based, UNION query-based, boolean-based blind, time-based blind, stacked queries, and out-of-band SQL injection techniques are all supported.
- Recognition of password hash formats automatically.
- Assistance with removing database tables.
Pricing
SQLmap is open-source and free to use.
24. Dirb
Dirb is a software program designed to systematically and exhaustively search for directories and files on web servers using a brute-force approach. Dirb initiates a dictionary-based assault on a designated web server and examines the resulting feedback.
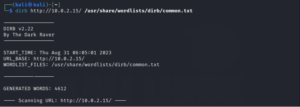
Features
- Resources that are concealed or unprotected are uncovered.
- Multiple HTTP methods and scanning protocols are supported.
- An adaptable scanning procedure.
- Wordlists for preconfigured attacks.
Pricing
Dirb is an open-source tool that is free to use.
25. Reaver
Reaver is a software application designed to attack vulnerabilities in the Wi-Fi Protected Setup (WPS) protocol. It operates by attempting to decipher the WPS PIN and gain unauthorized access to a Wi-Fi network, thereby exposing vulnerabilities in the system configuration.

Features
- Wordlists for preconfigured attacks.
- Tailored wordlists.
Pricing
Directory is an open-source, cost-free application.
Conclusion
This article provided an overview of 25 Best Kali Linux Tools that are often utilized on Kali Linux. It provided a comprehensive summary of the characteristics and editions of each tool. If you wish to know more about Kali Linux or any other cybersecurity related trends or technologies, you can join world-class cybersecurity training programs, such as 1 Year Diploma in Cyber Security Course by Craw Security, which is the leading cybersecurity training institute in India and the sister vertical of News4Hackers, the Best Cybersecurity Info, and News Portal.
For more detailed information, give them a call back at their official hotline mobile number, +91-9513805401, and have a word with authentic counselors to solve all your queries.
About The Author:
Yogesh Naager is a content marketer who specializes in the cybersecurity and B2B space. Besides writing for the News4Hackers blog, he’s also written for brands including CollegeDunia, Utsav Fashion, and NASSCOM. Naager entered the field of content in an unusual way. He began his career as an insurance sales executive, where he developed an interest in simplifying difficult concepts. He also combines this interest with a love of narrative, which makes him a good writer in the cybersecurity field. In the bottom line, he frequently writes for Craw Security.
READ MORE ARTICLE HERE









