Recon-ng Tutorial for Beginners

Recon-ng Tutorial for Beginners
Recon-ng is an open-source reconnaissance framework written in Python. It is designed to facilitate information gathering and reconnaissance activities during penetration testing or security assessments. Recon-ng provides a modular approach to reconnaissance, allowing users to load different modules to perform various tasks such as DNS enumeration, WHOIS lookups, email harvesting, social media profiling, and much more.
The framework offers a command-line interface (CLI) with a variety of built-in commands and modules. Users can also write their own modules to extend its functionality. Recon-ng’s modular architecture makes it highly flexible and customizable, allowing security professionals to tailor their reconnaissance activities according to the specific needs of their engagements.
Some key features of Recon-ng include:
- Modular design: Recon-ng organizes its functionality into modules, allowing users to easily load and unload different modules as needed.
- Extensibility: Users can write their own modules to add custom functionality or integrate with other tools and APIs.
- Intelligence gathering: Recon-ng provides a wide range of modules for gathering information from various sources such as public databases, social media platforms, search engines, and more.
- Reporting: Recon-ng includes features for generating reports based on the gathered information, making it easier to document findings and share them with stakeholders.
- Integration: Recon-ng can be integrated with other tools and frameworks, enhancing its capabilities and interoperability within the security ecosystem.
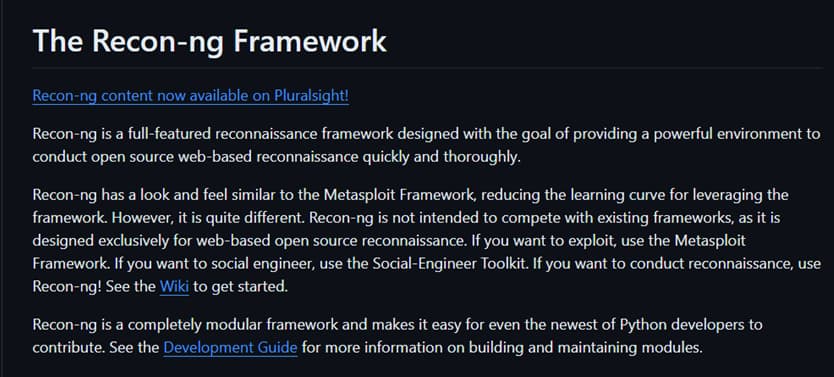
How to install the Recon-ng
- In Linux Distros we can install the recon-ng with just
{sudo apt install recon-ng}

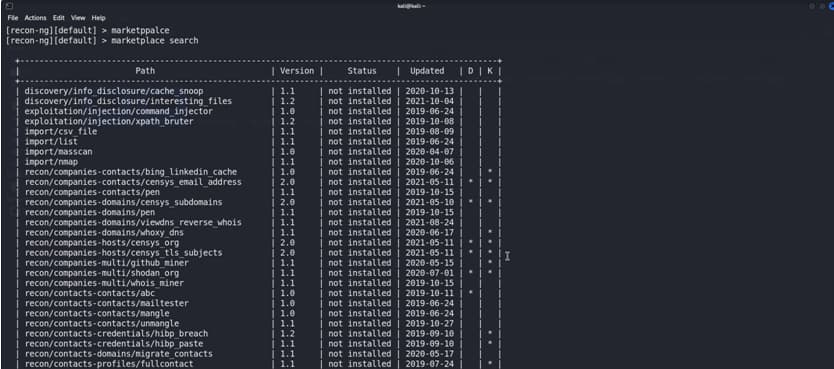
Recon-ng modules
Modules are grouped together under various categories and can be found searching on
Marketplace
– Discovery
– exploitation
– import
– recon
– reporting
Use marketplace search for a full table providing information on version, status (installed or not-installed), date updated, and dependencies or require keys.
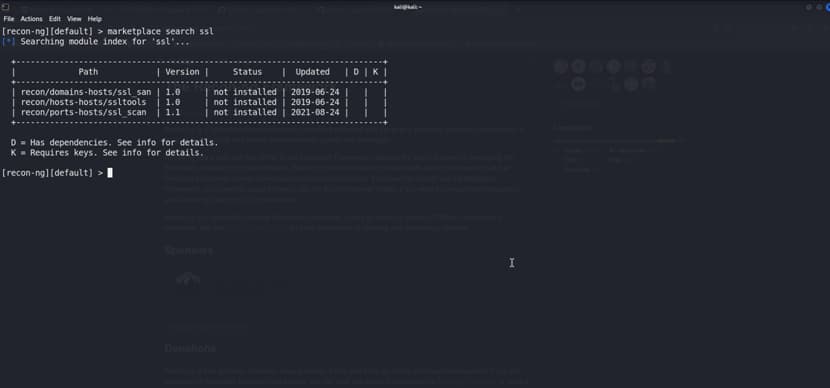
We can search for particular module.
We will search for ssl scanner
We will install the hack target
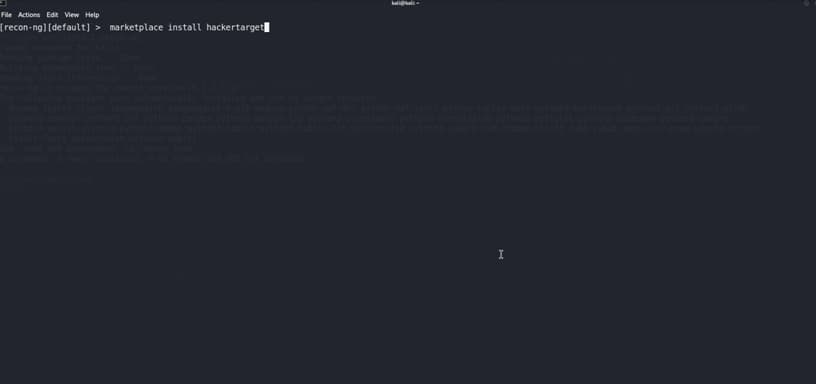
We will use the hacktarget
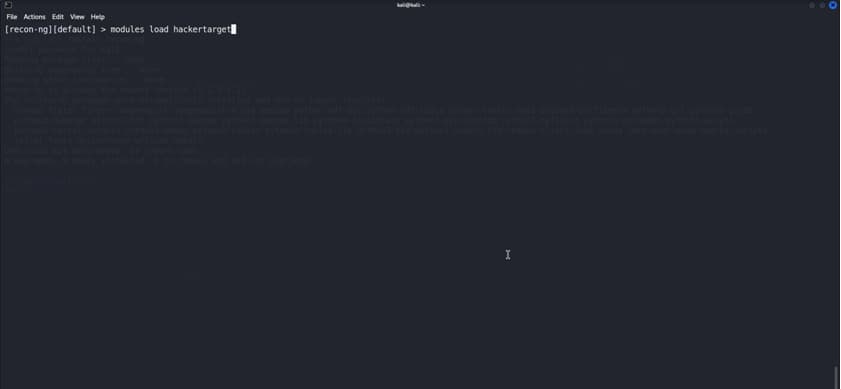
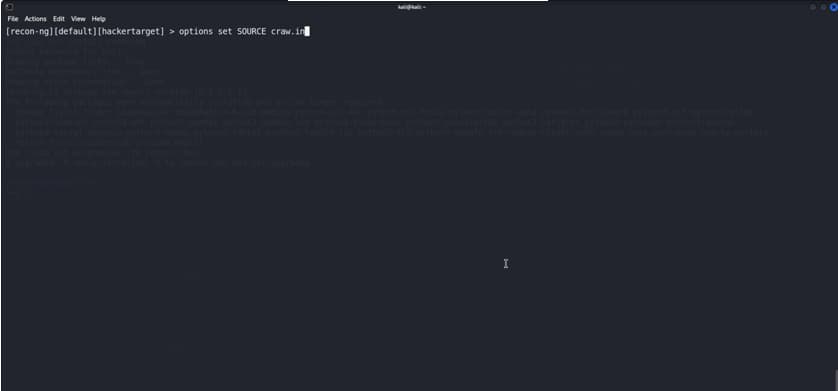
We will set the target
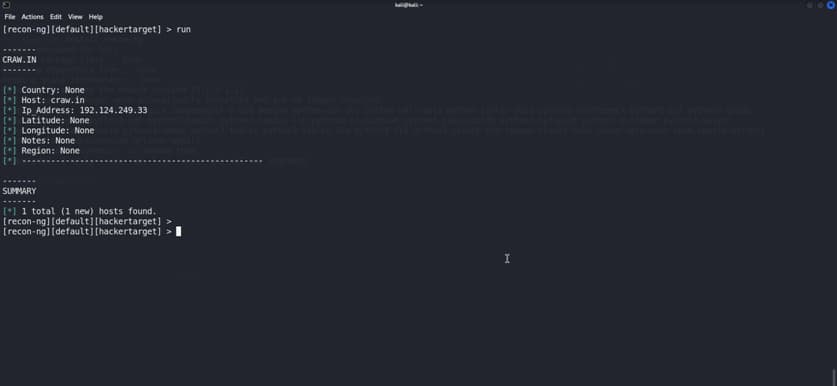
We will run the hacktarget
READ MORE ARTICLE HERE