A Facebook Bug May Have Enabled an Attacker to Take Over Accounts.

A Facebook Bug May Have Enabled an Attacker to Take Over Accounts.
A Facebook vulnerability might have enabled an assailant to commandeer a user’s account without requiring the targeted individual to perform any actions.
A Nepalese bounty hunter named Samip Aryal discovered the vulnerability, which Facebook has since resolved.

The four-time recipient of the Meta Whitehat Award began his investigation of an account hijacking vulnerability by examining the uninstall and reinstall procedure on Android. Through the utilization of various user agents, he was able to elicit a noteworthy response during the password reset procedure.
Upon investigation, several attributes of the logon code were found to be intriguing as potential attack vectors:
- Two hours was the validity period of the code.
- It did not alter when requested during that time period.
- The absence of validation resulted from entering an incorrect authentication code.
In conjunction with the 6-digit nature of these codes, Samip identified potential avenues for a brute force attack, which involves an assailant iteratively attempting to obtain login credentials with the ultimate goal of infiltrating an account.

Following the disclosure of this information and utilizing his profound understanding of the Facebook authentication procedure, Samip determined that the process of seizing control of an account was comparatively uncomplicated:
- Choose any Facebook profile.
- Request a password reset by attempting to log in as the specified user (Forgot password).
- Make a selection of “Send code via Facebook notification” from the available reset options.
- Assemble a POST request with this. The body of the request message may contain an arbitrary quantity of data of any type as part of a POST request.
- Duplicate the aforementioned POST request and implement a method to evaluate each of the one hundred thousand potential outcomes. It should be noted that while 100,000 possibilities may seem like a lot, there are ample opportunities to accomplish that within the allotted two hours.
- A redirection status code of 302 is returned by the matching code to indicate that the inquiry was successful.
- By entering the accurate code to reset the account’s password, the assailant has gained control of the account.
Pending one caveat, however. The notification will be presented to the account holder on the device they are using to access the account. Surprisingly, the notifications were available in two distinct varieties.
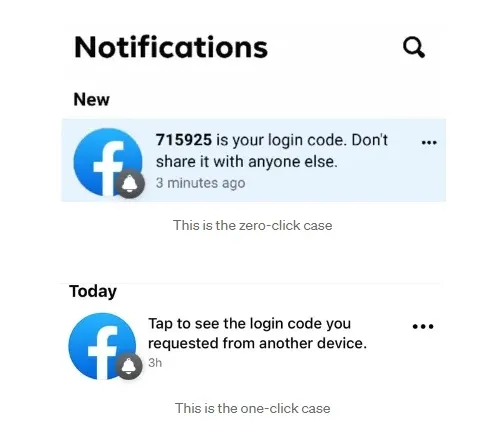
The first one functions as described previously, whereas the second one necessitates that the account holder select the alert prior to Facebook generating a login code. That significantly increases the difficulty of seizing control of the account.
The methodology by which Samip discovered the vulnerability is elaborated upon in his Medium post.

Samip was rewarded a bounty by Facebook for resolving the issue. Samip, in conjunction with other bounty hunters, filed Meta hundreds of reports, which the company subsequently resolved, thereby enhancing the security of Facebook and other platforms.
Paying Attention Pays Off.
There are several insights that users of Facebook, as well as other platforms, can potentially benefit from in relation to this approach.
- Observe the indications that a password request has been sent to you, such as notifications via email, messages, and so forth. Someone may be attempting to gain access to your account. If someone else is performing the password reset, adhere to the guidance provided in the update notification.
- It is strongly discouraged to utilize the Facebook login feature on any other platform, especially those that may contain sensitive financial or personal data.
- Enable Two-Factor Authentication on Facebook to increase the difficulty for hackers to compromise your account.
About The Author:
Yogesh Naager is a content marketer who specializes in the cybersecurity and B2B space. Besides writing for the News4Hackers blog, he’s also written for brands including CollegeDunia, Utsav Fashion, and NASSCOM. Naager entered the field of content in an unusual way. He began his career as an insurance sales executive, where he developed an interest in simplifying difficult concepts. He also combines this interest with a love of narrative, which makes him a good writer in the cybersecurity field. In the bottom line, he frequently writes for Craw Security.
Read More News







