APT36 Phishing Campaign Aims at Indian Defense with Credential-Stealing Malware

Executive Summary
The cyber espionage outfit APT36, also called Transparent Tribe, is based in Pakistan and has been using extremely complex phishing tactics to target Indian defense officials. The gang spreads phishing emails with infected PDF files that are painstakingly created to look like genuine government documents, according to News4Hackers’s findings.
Upon opening one of these PDFs, the receiver is presented with a blurred background and a button that mimics the National Informatics Center (NIC) login page. When a user clicks this button, a malicious executable file masquerading as a legal application is downloaded into a ZIP archive, and they are redirected to a fake URL.
APT36’s continued focus on credential theft and its strategic goal of creating long-term penetration within Indian defense networks are highlighted by this campaign. In order to counteract such focused cyberthreats, the operation emphasizes the critical necessity for strong email security measures, extensive user awareness campaigns, and proactive threat detection and monitoring systems.
Introduction
Nation-state actors are constantly changing their strategies to carry out targeted espionage in the increasingly complicated cyber threat scenario of today. One such threat actor is the Pakistani cyber-espionage organization “APT36” (also known as Transparent Tribe), which has drawn fresh attention for its intricate schemes to compromise India’s defense infrastructure.
With the intention of credential-harvesting for long-term access to sensitive networks, the gang disseminates malicious PDFs that imitate legitimate papers and direct visitors to fictitious NIC login sites, where they download disguised malware. This emphasizes how urgently user awareness training, robust email security, and ongoing threat monitoring are needed.
| Target Technologies | Windows Operating System |
| Threat Type | Phishing Campaign |
| Written In | C/C++ |
| File Types | PE (Portable Executable) |
| Key Malware Identifiers | PO-003443125.pdf, PO-003443125.pdf.7z |
| Observed First | 2025-05-07 |
| Impact | Credential Harvesting, Data Exfiltration |
| MD5 Hashes | PO-003443125.pdf “6ee3b0f4cb84e18751e7088043741e9a”
PO-003443125.pdf.7z“cdb9fb87dcb44d8f3040f4fb87d89508” PO-003443125.pdf.exe “154f4cdcd4b822314293ad566d7255fa” |
Phishing Campaign Analysis
The group’s campaign involves sending out phishing emails with the PDF file “PO-003443125.pdf” included.
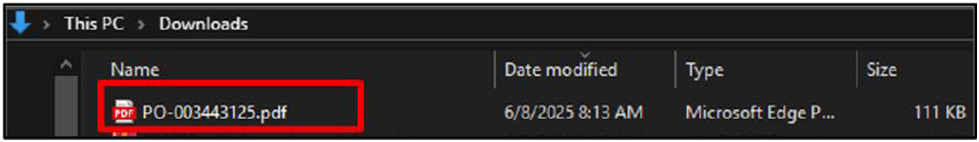
A PDF icon, the file name “PO-003443125.pdf,” a blurred backdrop (a purposeful technique used to give the appearance of authenticity), and the words “This is a protected document” are displayed when the document is opened. To view the material, click the button below. A button that reads “Click to View Document” is prominently placed to entice the recipient to interact.
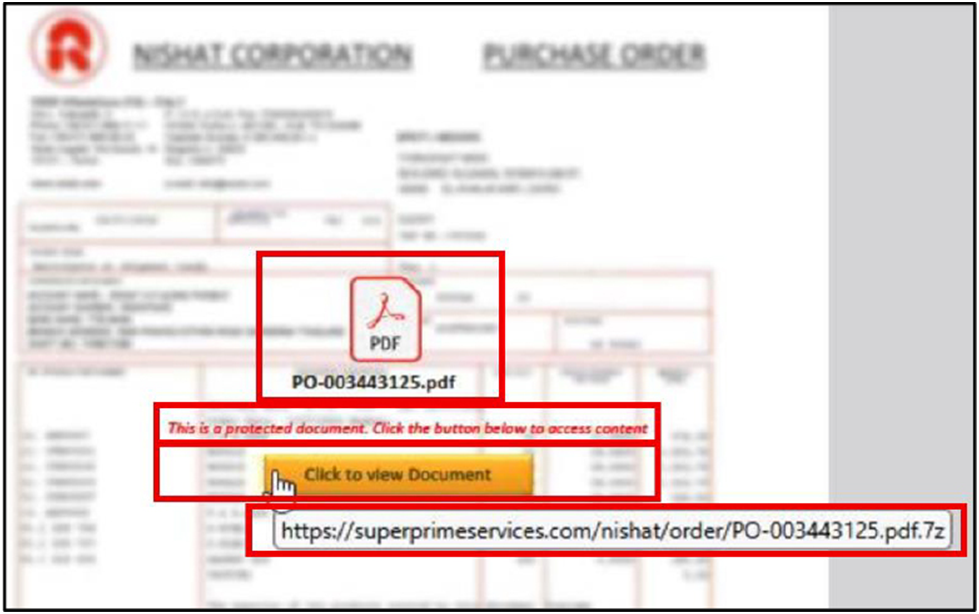
When the user interacts with the malicious URL “hXXps://superprimeservices[.]com/nishat/order/PO-003443125.pdf.7z,” an archive named “PO-003443125.pdf.7z” is downloaded.
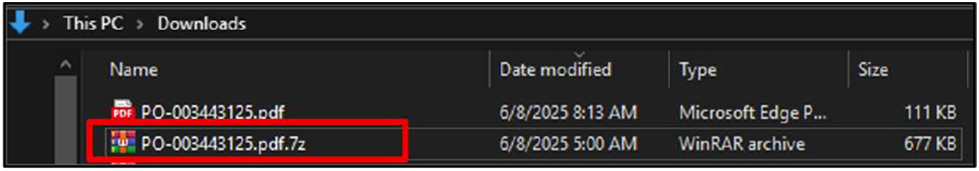
A malicious executable file called “PO-003443125.pdf.exe” is included in the archive; it poses as a valid PDF icon. This file is designed to deceive users and, if run, can allow unwanted access to the target system, compromising it.
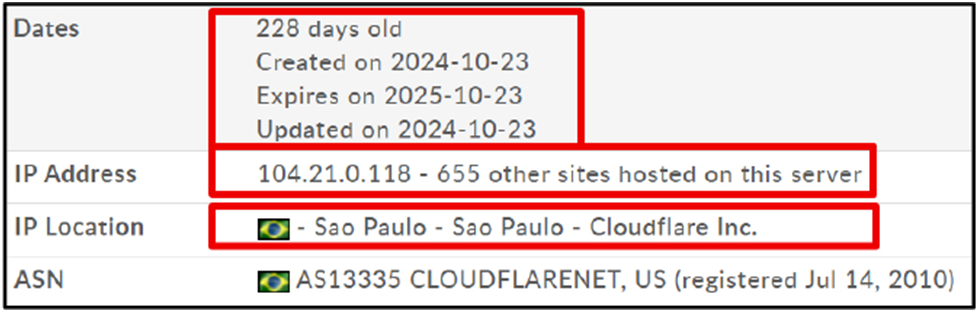
Due to its recent construction and possible short-term malevolent use, the domain in question was registered on October 23, 2024, and it expires on October 23, 2025. It resolves to the IP address 104[.]21[.]0[.]118, which is presently shared with over 655 other domains and is hosted by Cloudflare Inc. in São Paulo, Brazil.
Technical Analysis of “PO-003443125.pdf.exe”
Malware Functionalities
Further research reveals that a freeware programming language was used to create the executable file.
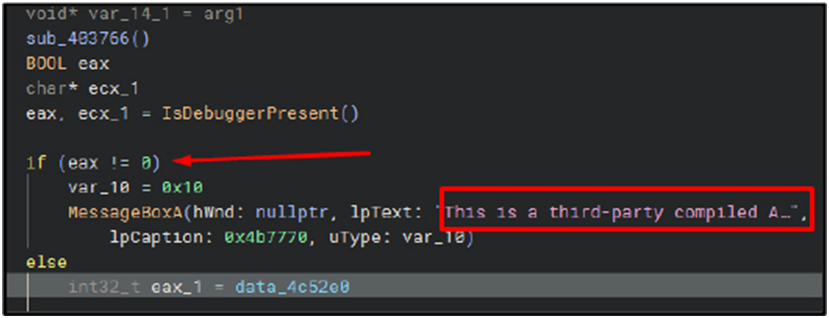
Anti-debugging and anti-reversing:
As an anti-analysis method, the Windows API function “IsDebuggerPresent” is frequently used to ascertain whether the program is running under a debugging environment like x64dbg, WinDbg, or OllyDbg. If the malware is found, it stops the process after displaying a warning that reads, “This is a third-party compiled script.”
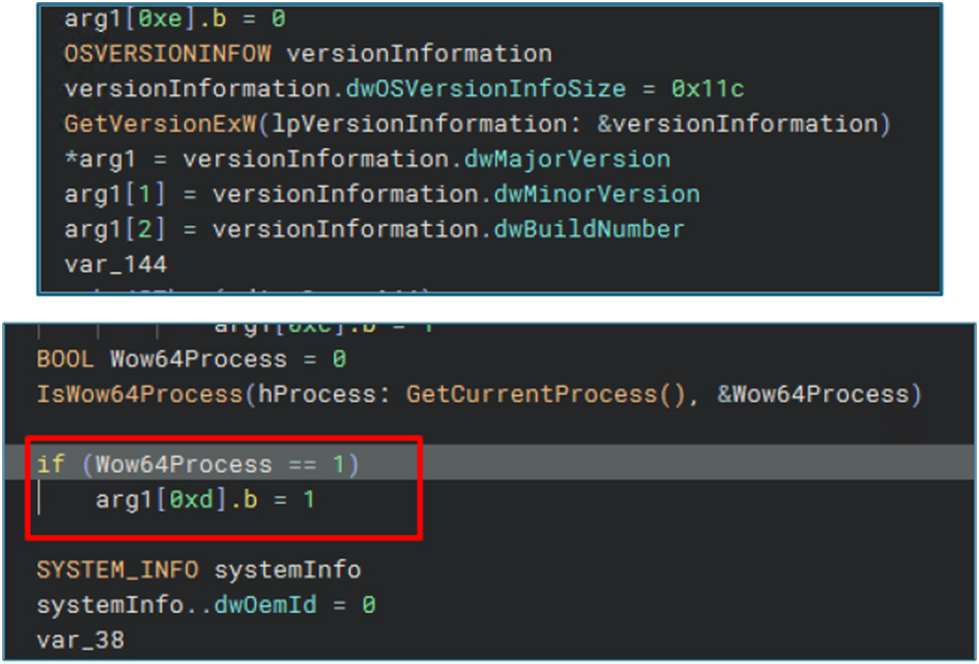
Anti-VM
In order to determine whether it is operating in a 32-bit process on a 64-bit system—a typical indication of a virtualized or analytic environment—the malware makes use of IsWow64Process.
In order to avoid analysis, WOW64 sets a flag and stops execution if it is found.
This pattern suggests the adoption of anti-VM and anti-sandbox strategies to evade detection.
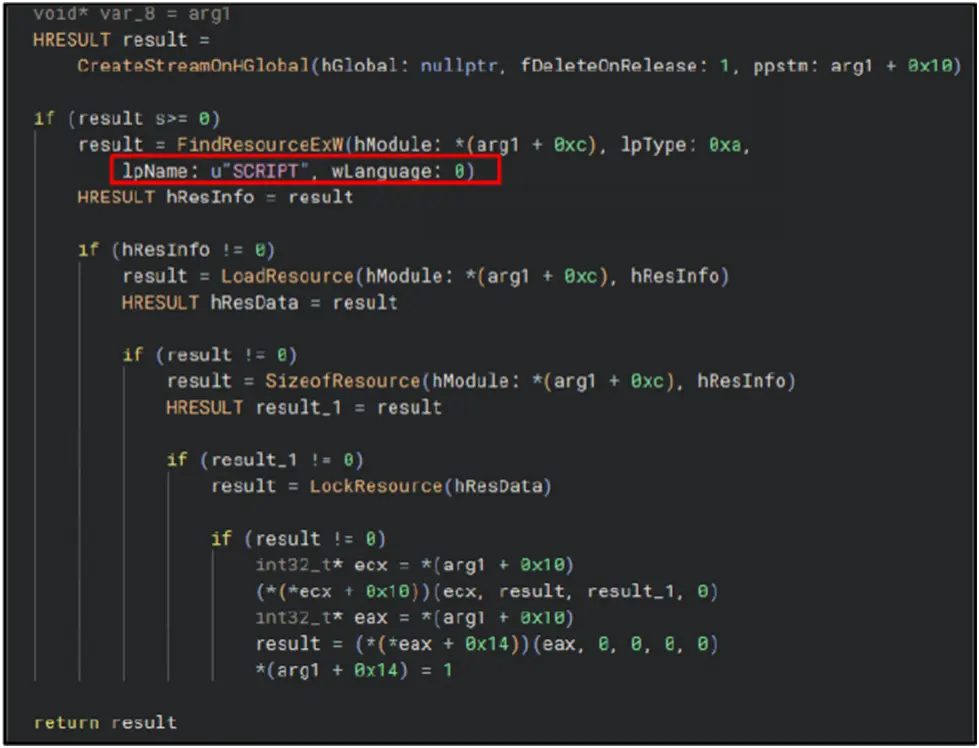
Loading Malicious Script from Resources:
FindResourceExW finds a resource in its own module with the name “SCRIPT” and type 0x0A. The resource’s size and data are then obtained by loading and locking it, and they are then written into a stream that was formed using CreateStreamOnHGlobal.
In order to run or interpret the embedded script and enable fileless or in-memory execution, it lastly calls method calls (probably COM or ActiveScript interfaces).
Process Creation and Execution:
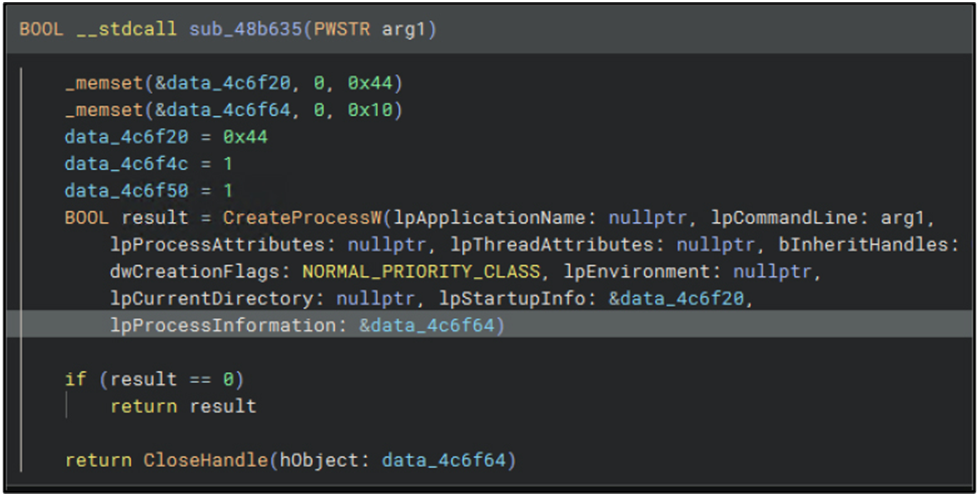
Using the command line supplied in arg1, the malware creates STARTUPINFO and PROCESS_INFORMATION structures and then uses CreateProcessW to spawn a new process, setting flags for normal priority and a default environment to indicate a covert launch. If it is successful, the process handle is closed, signaling that commands or payloads are being executed.
Execution:
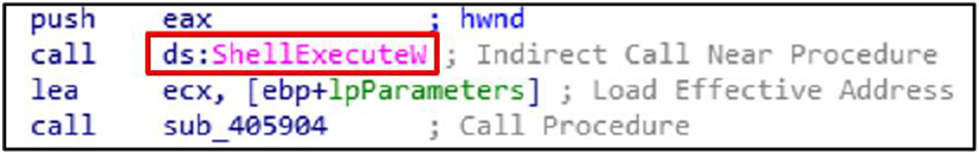
The secondary stages of an attack are initiated by ShellExecuteW.
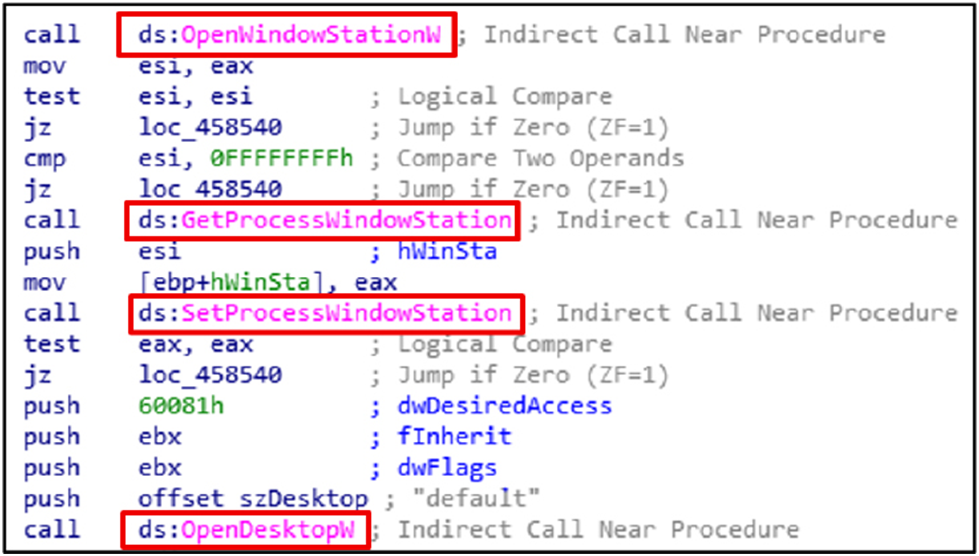
The malware can interact with user sessions, inject code, avoid detection, and remain persistent in targeted environments by using the OpenWindowStationW, GetProcessWindowStation, SetProcessWindowStation, and OpenDesktopW functions to access and manipulate window stations and desktops.
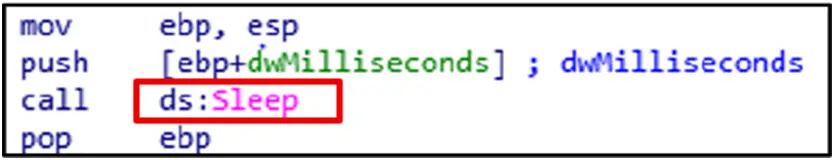
Defense Evasion:
The Sleep function momentarily halts operation. It is used by the malware to postpone actions, elude discovery, and evade analysis.
GetCurrentProcess and TerminateProcess are used by the malware for code injection, privilege escalation, process control, and anti-analysis.
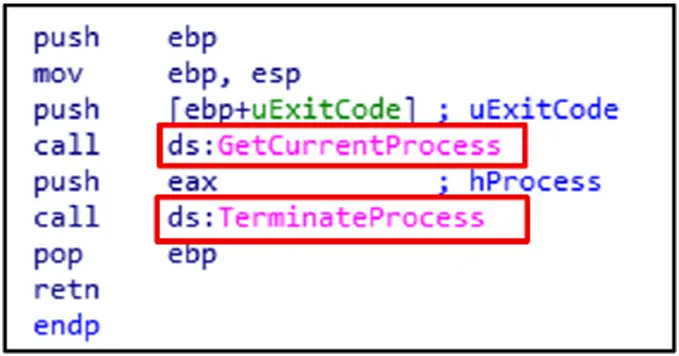
By loading unauthorized libraries through legitimate apps, attackers can use DLL side-loading to execute malicious code. The LoadLibraryExW function loads a DLL into a process address space.
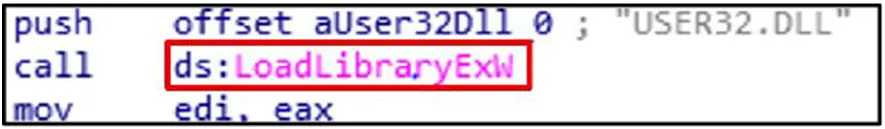
The malware supports persistence, configuration, and evasion strategies by modifying and accessing system environment variables with SetEnvironmentVariableA and GetEnvironmentVariableW.
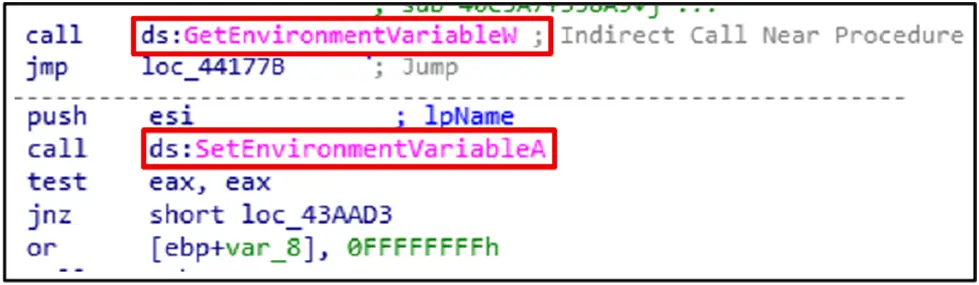
Persistence:
Process startup parameters are obtained using the GetStartupInfo function. It is used by the malware to improve stealth and modify execution.
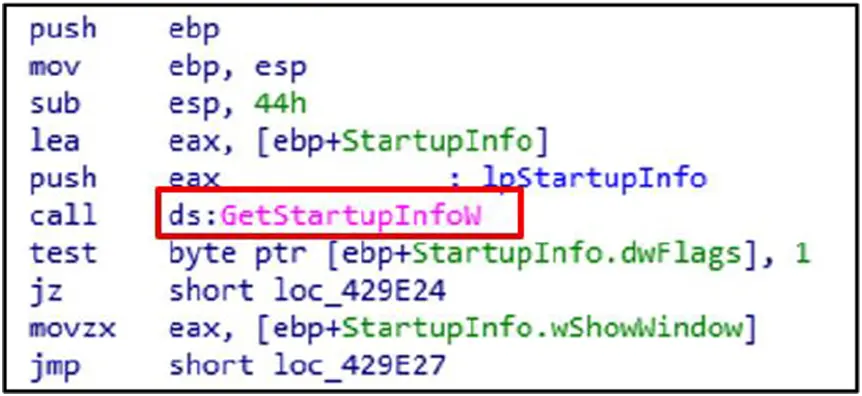
Data Discovery:
Attackers utilize GetDriveTypeW to determine which network or detachable drives to target.

The directory’s files are searched for data exfiltration using FindNextFileExW.

The file enumeration initiated by FindFirstFileExW is continued by FileNextFilew.
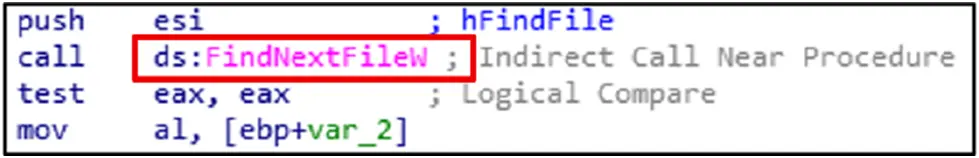
The handle is released from FindFirstFileExW using FileClose.
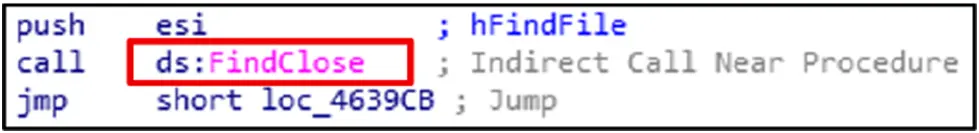
Credential Access:
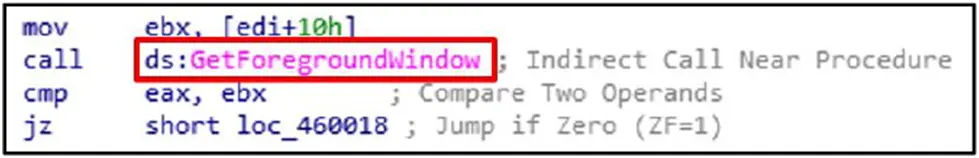
The current window is identified using the GetForegroundWindow function, which is frequently used to record user activities.
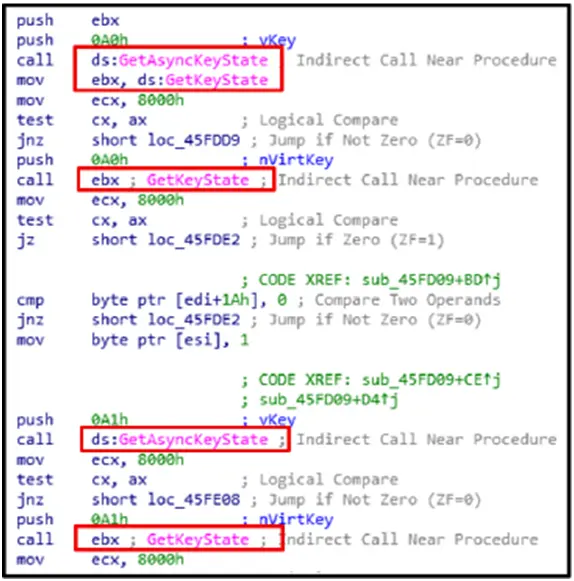
Keystrokes are tracked and recorded in real time using the GetAsyncKeyState and GetKeyState methods. By using these APIs to identify user input, the malware makes it easier to keylog users and steal private information like login passwords and private messages.
To access clipboard contents and steal private data, including cryptocurrency wallet addresses or copied passwords, utilize OpenClipboard, IsClipboardFormatAvailable, and GetClipboardData.

The application embeds an “edit” control as its child and generates a hidden window with a specified class name. Standard window manipulation functions (e.g., ShowWindow with the SW_HIDE flag) are used to hide both the parent and child windows. By imitating the operations of genuine apps, this setup enables the script to surreptitiously mimic user interactions and maybe avoid detection by automation or simple keylogger systems.
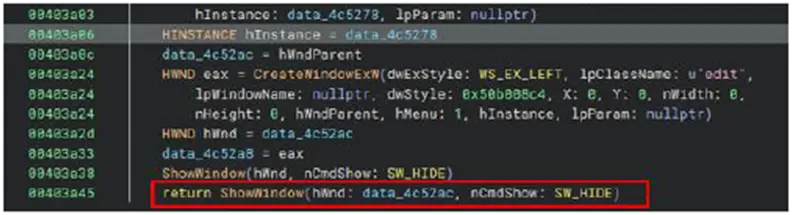
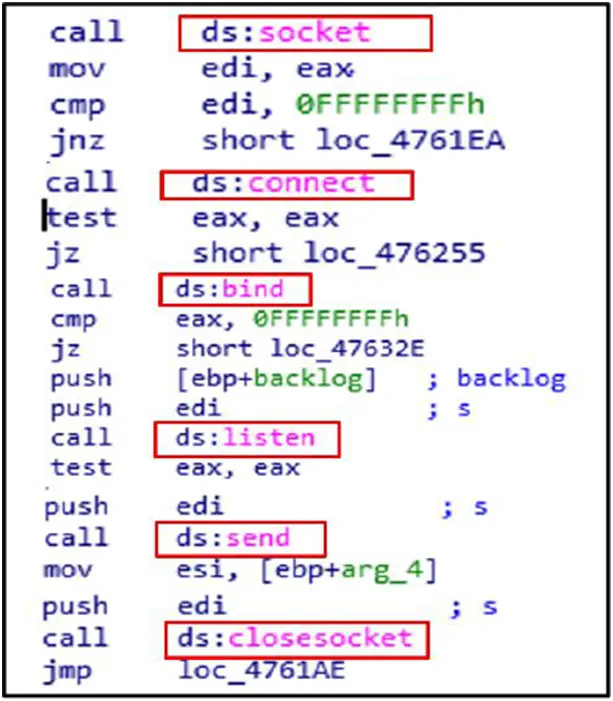
Command and Control:
Malware establishes, controls, and ends network communications by using the socket, connect, bind, listen, send, and closesocket capabilities. These features make remote access, data exfiltration, and command-and-control (C2) interactions easier.
Malware Behaviors
Anti-Analysis Behavior: By posing as a genuine PDF document, the executable PO-003443125[.]pdf[.]exe engages in anti-analysis behavior. The purpose of this purposefully deceptive naming scheme is to deceive users and avoid accidental detection by analysts or entry-level security programs that might not show whole file extensions. Furthermore, starting a Windows process (svchost.exe) that seems authentic as a child may be an attempt to blend in with regular system operations and evade detection during automatic monitoring or manual inspection.
Process Activity: PO-003443125[.]pdf[.]exe is a parent process that launches svchost.exe as a child, according to the process tree. This is unusual since the Windows operating system, not user-launched apps, normally launches svchost.exe. When a parent process uses up all of a CPU core, it could be a sign of resource-intensive malicious activity like network beaconing, crypto mining, or keylogging. This erratic pattern of activity is a reliable predictor of possible malware execution.
Obfuscation: The file appears harmless by using the traditional obfuscation approach of a double extension (.pdf.exe). This method makes use of a common Windows user setting that conceals recognized file extensions, making the file appear to be a harmless PDF. This method is commonly used to increase the likelihood of successful execution by avoiding user scrutiny and basic file-type filters.
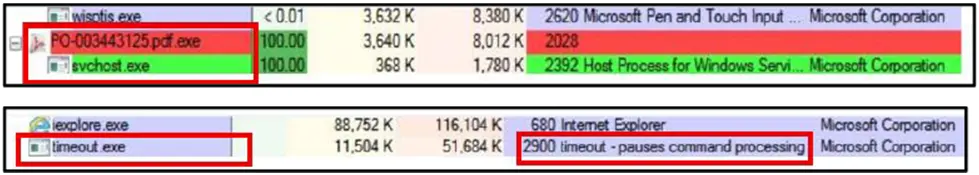
Credential and Data Theft: The malware targets saved credentials, form inputs, email client credentials, system clipboard contents, and browser data cookies. It uses clipboard monitoring, keylogging through API hooks, and form-grabbing tactics to steal confidential information before it is hidden or encrypted by trustworthy apps.
Network Communication: DNS queries to several malicious and low-reputation domains are seen, many of which use dubious TLDs like.xyz,.buzz,.ru, and.sbs.
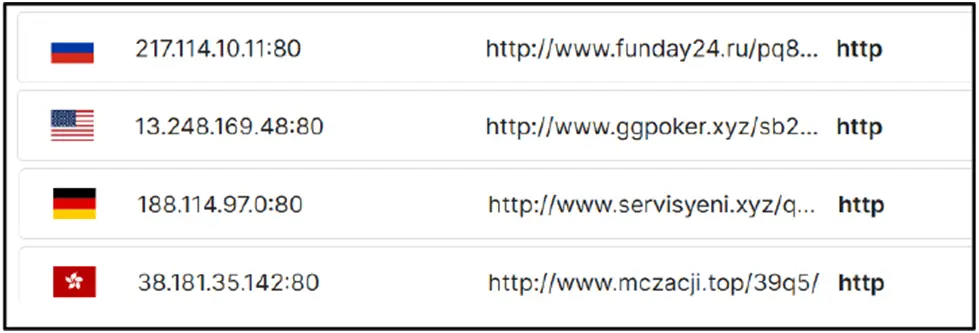
With infrastructure housed on well-known CDN providers (like Cloudflare and AWS), encrypted HTTP(S) connection with C2 servers is discovered. This is probably done for delivery reliability and camouflage.
MITRE ATT&CK Framework
The widely recognized MITRE ATT&CK Framework is mentioned in the following table:
| MITRE MAPPING | ||
| Tactic | ID | Technique Name |
| Initial Access | T1566 | Phishing |
| T1566.001 | Spear phishing Attachment | |
| Execution | T1203 | Exploitation for Client Execution |
| T1059 | Command and Scripting Interpreter | |
| Persistence | 1542 | Pre-OS Boot |
| T1542.003 | Bootkit | |
| T1574 | Hijack Execution Flow | |
| T1574.002 | DLL Side-Loading | |
| T1112 | Modify Registry | |
| T1547 | Boot or Logon AutoStart Execution | |
| T1547.009 | Shortcut Modification | |
| Privilege Escalation | T1055 | Process Injection |
| T1574 | Hijack Execution Flow | |
| T1574.002 | DLL Side-Loading | |
| T1134 | Access Token Manipulation | |
| T1134.001 | Token Impersonation/ Theft | |
| T1547 | Boot or Logon AutoStart Execution | |
| T1547.009 | Shortcut Modification | |
| Defense Evasion | T1014 | Rootkit |
| T1036 | Masquerading | |
| T1055 | Process Injection | |
| T1542 | Pre-OS Boot | |
| T1542.003 | Bootkit | |
| T1564 | Hide Artifacts | |
| T1564.001 | Hidden Files and Directories | |
| T1564.003 | Hidden Window | |
| T1497 | Virtualization/Sandbox Evasion | |
| T1562 | Impair Defenses | |
| T1562.001 | Disable or Modify Tools | |
| T1027 | Obfuscated Files of Information | |
| T1027.002 | Software Packing | |
| T1112 | Modify Registry | |
| T1134 | Access Token Manipulation | |
| T1134.001 | Token Impersonation/ Theft | |
| T1222 | Files and Directory Permission Modification | |
| T1497.002 | User Activity Based Checks | |
| T1574 | Hijack Execution Flow | |
| T1574.002 | DLL Side-Loading | |
| Credential Access | T1003 | OS Credential Dumping |
| T1056 | Input Capture | |
| T1056.001 | Keylogging | |
| Discovery | T1012 | Query Registry |
| T1057 | Process Discovery | |
| T1083 | Files and Directory Discovery | |
| T1010 | Application Window Discovery | |
| T1082 | System Information Discovery | |
| T1497 | Virtualization/Sandbox Evasion | |
| T1518 | Software Discovery | |
| T1518.001 | Security Software Discovery | |
| T1016 | System Network Configuration Discovery | |
| T1018 | Remote System Discovery | |
| T1614 | System Location Discovery | |
| T1033 | System Owner/User Discovery | |
| T1087 | Account Discovery | |
| T1497.002 | User Activity Based Checks | |
| T1614.001 | System Language Discovery | |
| Collection | T1005 | Data from Local System |
| T1114 | Email Collection | |
| T1057 | Input Capture | |
| T1056.001 | Keylogging | |
| T1113 | Screen Capture | |
| T1115 | Clipboard Data | |
| T1185 | Browser Session Hijacking | |
| Command and control | T1071 | Application Layer Protocol |
| T1095 | Non-Application Layer Protocol | |
| T1573 | Encrypted Channel | |
| T1105 | Ingress Tool Transfer | |
| Impact | T1485 | Data Destruction |
| T1496 | Resource Hijacking | |
| T1529 | System Shutdown/Reboot | |
Conclusion
APT36, which targets Indian defense infrastructure in particular, is a serious and persistent cyberthreat to national security. The group’s employment of sophisticated phishing techniques and credential theft is a prime example of how sophisticated current cyber espionage has become. Implementing a thorough, multi-layered cybersecurity system that includes strong email security safeguards, ongoing user education, and alert threat detection and response capabilities is necessary to meet this problem.
Recommendations
Based on a thorough examination of the APT36 campaign, which used phishing emails and malware masquerades to target Indian defense professionals, News4Hackers suggests the following mitigation techniques and recommendations that are especially suited for the Indian defense industry:
Enhance Email Security Infrastructure
- Deploy Government-Grade Email Security Solutions: For government communication platforms (such as NIC mail), use enhanced risk protection, which checks PDF, 7Z, and exe files for embedded malware.
- Strict Attachment Handling Policies: Emails with questionable file formats (such as.pdf.7z or.exe files with fake icons) should be blocked or quarantined.
- Implement Email Authentication Protocols: Enforce DKIM, SPF, and DMARC on official defense email domains to stop APT36 from impersonating and spoofing them.
User Awareness and Training
- Mandatory Cyber Hygiene Training: All military and civilian staff should receive frequent, required training on how to spot phishing attacks, particularly those that imitate official NIC documents.
- Simulated Phishing Exercises: Using formats and methods similar to those employed by APT36, conduct red team exercises with phishing simulations on a regular basis (e.g., fake protected PDFs).
- Clear Reporting Protocols: Provide simple avenues for reporting alleged phishing emails and anomalous activity.
Network and Endpoint Security
- Endpoint Detection and Response (EDR): Deploy EDR solutions on all defense endpoints to detect and respond to file-based threats such as:
- PO-003443125.pdf – MD5: 6ee3b0f4cb84e18751e7088043741e9a
- PO-003443125.pdf.7z – MD5: cdb9fb87dcb44d8f3040f4fb87d89508
- PO-003443125.pdf.exe – MD5: 154f4cdcd4b822314293ad566d7255fa
- Block Malicious Domains and URL: hXXps://superprimeservices[.]com/nishat/order/PO-003443125[.]df[.]7z
Access Control and Authentication
- Mandate Multi-Factor Authentication (MFA): Reduce the usefulness of stolen credentials by requiring MFA for all access to NIC systems and sensitive defensive networks.
- Regular Password Rotation and Audits: To identify misuse, establish stringent password regulations, and conduct regular credential audits.
Infrastructure and Threat Intelligence Monitoring
- Monitor Cloudflare-Hosted Traffic: Keep an eye out for connections to recently registered Cloudflare-hosted domains in defense-related network logs—APT36 regularly employs this provider to conceal infrastructure.
- Integrate Threat Feeds: To prevent signs of compromise (IOCs), sign up for real-time intelligence on APT36 and other regional threats.
Incident Response Preparedness
- Establish Sector-Specific IR Teams: Create defense units with specialized cyber incident response teams that have received training on APT36 TTPs.
- Run Tabletop and Live Drills: Test defense units’ preparedness for phishing attacks and post-compromise actions such as lateral movement or credential harvesting on a regular basis.
To efficiently identify new TTPs, improve situational awareness, and provide prompt threat mitigation pertinent to your sector and area, stay up to speed with News4Hackers’s threat intelligence sharing platform.
Utilize News4Hackers’s Indicators of Compromise (IOCs) and YARA rules to improve the identification of malicious files and activity through behavioral analysis and file integrity monitoring. Update them on your SIEM platform on a regular basis.
Indicators of Compromise (IoCs)
To exercise control over your security systems, please consult the IOCs section.
| S.No | Indicator | Remarks |
| 1 | f03ac870cb91c00b51ddf29b6028d9ddf42477970eafa7c556e3a3d74ada25c9 | Block |
| 2 | 55b7e20e42b57a32db29ea3f65d0fd2b2858aaeb9307b0ebbcdad1b0fcfd8059 | Block |
| 3 | 55972edf001fd5afb1045bd96da835841c39fec4e3d47643e6a5dd793c904332 | Block |
| 4 | SuperPrimeServices[.]com | Block |
| 5 | Advising-Receipts[.]com | Block |
| 6 | FunDay24[.]ru | Block |
| 7 | slotgacorterbaru[.]xyz | Monitor |
| 8 | servisyeni[.]xyz | Monitor |
| 9 | chillchad[.]xyz | Monitor |
| 10 | ggpoker[.]xyz | Monitor |
| 11 | boldcatchpoint[.]shop | Monitor |
| 12 | zhangthird[.]shop | Monitor |
| 13 | vipwin[.]buzz | Monitor |
| 14 | wholly-well[.]info | Monitor |
| 15 | rapio[.]site | Monitor |
| 16 | 55cc[.]info | Monitor |
| 17 | megasofteware[.]net | Monitor |
| 18 | worrr19[.]sbs | Monitor |
| 19 | kp85[.]cyou | Monitor |
| 20 | mczacji[.]top | Monitor |
| 21 | 59292406[.]xyz | Monitor |
| 22 | 76[.]223[.]54[.]146 | Monitor |
| 23 | 188[.]114[.]97[.]7 | Monitor |
| 24 | 13[.]248[.]169[.]48 | Monitor |
| 25 | 84[.]32[.]84[.]32 | Monitor |
| 26 | 217[.]114[.]10[.]11 | Monitor |
| 27 | 207[.]244[.]126[.]106 | Monitor |
| 28 | 172[.]67[.]148[.]140 | Monitor |
| 29 | 198[.]252[.]111[.]31 | Monitor |
| 30 | 15[.]197[.]148[.]33 | Monitor |
| 31 | 162[.]254[.]38[.]217 | Monitor |
| 32 | 104[.]21[.]41[.]144 | Monitor |
YARA Rule
rule APT36_IOCs_Indicators
{
meta:
author = “News4Hackers Research”
description = “Detects known APT36-related indicators (hashes, IP, domains)”
date = “2025-06-08”
threat_group = “APT36 / Transparent Tribe”
strings:
// SHA256 file hashes (can be used for memory or file scan)
$hash1 = “f03ac870cb91c00b51ddf29b6028d9ddf42477970eafa7c556e3a3d74ada25c9”
$hash2 = “55b7e20e42b57a32db29ea3f65d0fd2b2858aaeb9307b0ebbcdad1b0fcfd8059”
$hash3 = “55972edf001fd5afb1045bd96da835841c39fec4e3d47643e6a5dd793c904332”
// Domains used by APT36
$domain1 = “SuperPrimeServices.com”
$domain2 = “Advising-Receipts.com”
$domain3 = “FunDay24.ru”
$domain4 = “slotgacorterbaru.xyz”
$domain5 = “servisyeni.xyz”
$domain6 = “chillchad.xyz”
$domain7 = “ggpoker.xyz”
$domain8 = “boldcatchpoint.shop”
$domain9 = “zhangthird.shop”
$domain10 = “vipwin.buzz”
$domain11 = “wholly-well.info”
$domain12 = “rapio.site”
$domain13 = “55cc.info”
$domain14 = “megasofteware.net”
$domain15 = “worrr19.sbs”
$domain16 = “kp85.cyou”
$domain17 = “mczacji.top”
$domain18 = “59292406.xyz”
// IPs used by APT36
$ip1 = “76.223.54.146”
$ip2= “188.114.97.7”
$ip3= “13.248.169.48”
$ip4= “84.32.84.32”
$ip5= “217.114.10.11”
$ip6= “207.244.126.106”
$ip7= “172.67.148.140”
$ip8= “198.252.111.31”
$ip9= “15.197.148.33”
$ip10= “162.254.38.217”
$ip11= “104.21.41.144”
condition:
any of ($hash*) or any of ($domain*) or any of ($ip*)
}
About The Author:
Yogesh Naager is a content marketer who specializes in the cybersecurity and B2B space. Besides writing for the News4Hackers blogs, he also writes for brands including Craw Security, Bytecode Security, and NASSCOM.







