Describing Apple Lockdown Mode: What is it, and How Does it Prevent Spyware Attacks?
Describing Apple Lockdown Mode: What is it, and How Does it Prevent Spyware Attacks?
Using the tool should be restricted to people who consider themselves to be possible targets, according to Apple.
The potential of mercenary spyware attacks has been brought to the attention of customers in 92 countries, including India, through the distribution of warnings and alerts by Apple. According to a report that was published by a famous organization, sophisticated attacks pose a serious risk to the personal information and privacy of iPhone users.
‘Lockdown’ mode was first implemented in iPhones by Apple in 2022 when the company released iOS 16 to the public.

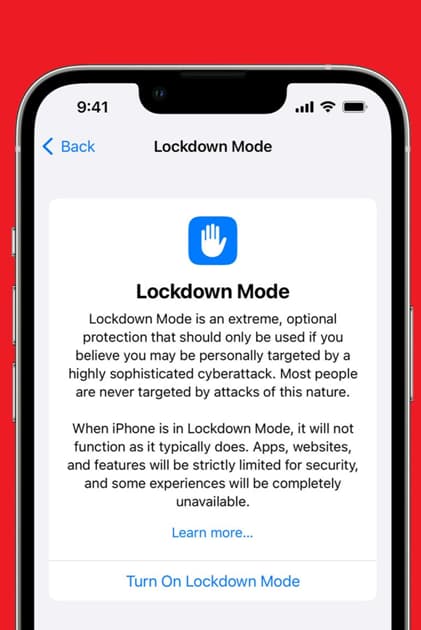
The Lockdown Mode
In this mode, iPhone users are protected from attacks by mercenary spyware and other risks of a similar nature. Apple suggests that iPhone owners who believe they could be used by others, such as government officials, activists, or journalists, should give serious consideration to utilizing the function.
The business stated that it is highly improbable that the majority of iPhone users will be the victim of such attacks; yet, the capability is available to all customers.
When the lockdown mode is activated on an iPhone, the device does not function in the normal manner. While the most fundamental features, such as making phone calls and sending plain text messages, continue to function without any problems, additional applications are restricted. For instance, according to a study from a famous organization, it is possible to restrict attachments in communications. These attachments can include specific kinds of photographs, videos, and audio files.
For example, according to Apple, if an iPhone user is using Safari as their primary browser, then there are certain “complex technologies” that could potentially be restricted. In certain instances, this may cause websites to take slower to load, and in other instances, it may even prevent specific websites from loading at all. It is also possible that certain photos will not display in the browser, and it is also possible that web fonts will not display properly.
Calls made using FaceTime are also affected when the ‘lockdown’ feature is active. You will not be able to initiate or receive FaceTime calls with a person unless that person is listed as a contact on your device or unless you have previously participated in a FaceTime call with that person. Additionally, additional tools that are offered within FaceTime calls, such as SharePlay and Live Photos, are neither available nor accessible.

Furthermore, when you share images with other people, the location data and information on such photos will not be disclosed. The user will no longer get any new invitations to join shared albums, and the Photos app will immediately remove shared albums. This is according to the article that was published by a famous enterprise.
According to News4Hackers, iPhone users will not be able to connect to a Wi-Fi network that is not secure while the ‘lockdown’ is in effect. Even if the Wi-Fi network is well-known but not secure, people will still be disconnected from being connected to it.
In order to activate the “lockdown” mode on an iPhone, the following actions need to be taken:
- Open the Settings app
- Tap on “Privacy & Security”
- Tap on “Lockdown Mode”
- Tap on “Turn On Lockdown Mode”
- Tap on “Turn On & Restart”
- Enter device passcode
About The Author:
Yogesh Naager is a content marketer who specializes in the cybersecurity and B2B space. Besides writing for the News4Hackers blog, he’s also written for brands including CollegeDunia, Utsav Fashion, and NASSCOM. Naager entered the field of content in an unusual way. He began his career as an insurance sales executive, where he developed an interest in simplifying difficult concepts. He also combines this interest with a love of narrative, which makes him a good writer in the cybersecurity field. In the bottom line, he frequently writes for Craw Security.
READ MORE ARTICLE HERE









