Malicious Google Ads Used By FIN7 to Deliver NetSupport RAT

Malicious Google Ads Used By FIN7 to Deliver NetSupport RAT
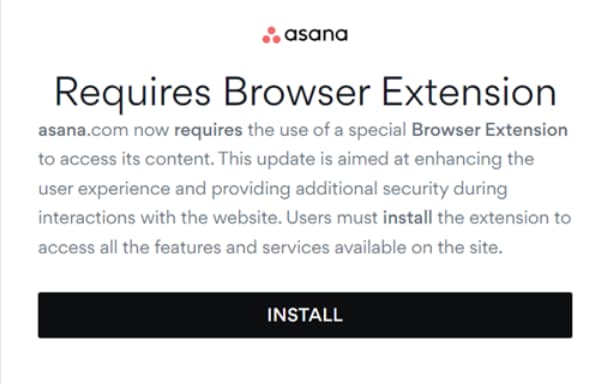
The financially motivated threat actor known as FIN7 has been seen distributing MSIX installers that ultimately lead to the deployment of NetSupport RAT by using malicious Google advertising that mimics reputable firms.
eSentire, Cybersecurity Firm, Report, This Week.
| “The threat actors used malicious websites to impersonate well-known brands, including AnyDesk, WinSCP, BlackRock, Asana, Concur, The Wall Street Journal, Workable, and Google Meet.” |
A persistent e-crime outfit that has been operating since 2013, FIN7 (also known as Carbon Spider and Sangria Tempest) first dabbled in attacks aimed at point-of-sale (PoS) devices to steal payment data before refocusing on ransomware campaigns to penetrate large firms.
The threat actor has improved its strategies and malware library over time, utilizing several unique malware families, including TERMITE, POWERPLANT, DICELOADER (also known as Lizar and Tirion), BIRDWATCH, Carbanak, and POWERTRASH.

The FIN7 virus is often introduced into a target network or host through spear-phishing efforts; however, in recent times, the organization has also employed malvertising tactics to start the assault chains.
Microsoft, December, 2023
| It has seen attackers using Google advertisements to trick people into downloading malicious MSIX application packages. This ultimately resulted in the execution of POWERTRASH, an in-memory dropper powered by PowerShell that loads Gracewire and NetSupport RAT. |
The Tech Giant noted.
| “Sangria Tempest […] is a financially motivated cybercriminal group currently focusing on conducting intrusions that often lead to data theft, followed by targeted extortion or ransomware deployment such as Clop ransomware.” |
Because MSIX can get beyond security measures like Microsoft Defender SmartScreen, it has been abused by several threat actors as a malware distribution vector. As a result, Microsoft disabled the protocol handler by default.
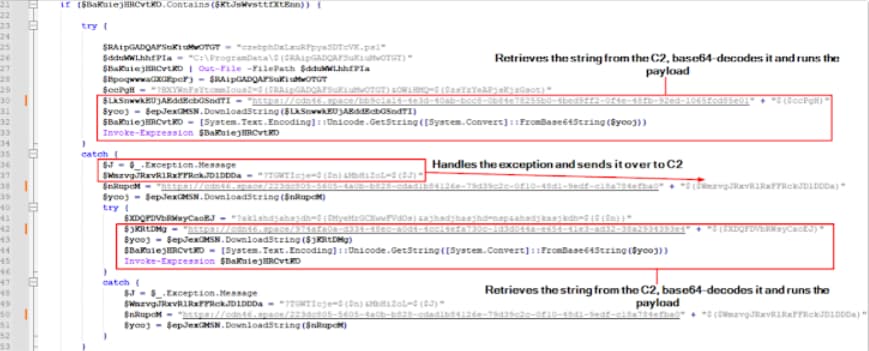
A pop-up message encouraging users to download a fake browser extension—an MSIX file containing a PowerShell script—is displayed to users who visit the bogus sites through Google ads in April 2024, according to eSentire’s observations of the attacks. This script collects system information and communicates with a remote server to retrieve another encoded PowerShell script.
To download and run the NetSupport RAT from an actor-controlled server, utilize the second PowerShell payload.
The Canadian cybersecurity firm claimed to have discovered the use of DICELOADER and other malware sent via a Python script by the remote access trojan.
eSentire
| “The incidents of FIN7 exploiting trusted brand names and using deceptive web ads to distribute NetSupport RAT followed by DICELOADER highlight the ongoing threat, particularly with the abuse of signed MSIX files by these actors, which has proven effective in their schemes.”
“Attackers used living-off-the-land techniques to collect sensitive credentials, and notably, configured web beacons in both email signatures and network shares to map out local and business-to-business relationships.” “This behavior would suggest an interest in exploiting these relationships to target business peers of interest.” |
Malwarebytes has separately revealed similar results, characterizing the activity as imitating well-known businesses including Asana, BlackRock, CNN, Google Meet, SAP, and The Wall Street Journal to specifically target corporate customers with harmful advertising and models. It did not, however, credit FIN7 with the initiative.
The disclosure of FIN7’s deceptive marketing tactics aligns with a surge of SocGholish, also known as FakeUpdates, malware intended to compromise business associates.
It also comes after a malware operation was uncovered that used exploits for well-known software to spread RATs and cryptocurrency miners among Windows and Microsoft Office users.
Broadcom-Owned Symantec
| “The malware, once installed, often registers commands in the task scheduler to maintain persistence, enabling continuous installation of new malware even after removal.” |
About The Author
Suraj Koli is a content specialist with expertise in Cybersecurity and B2B Domains. He has provided his skills for the News4Hackers Blog and Craw Security. Moreover, he has written content for various sectors Business, Law, Food & Beverage, Entertainment, and many others. Koli established his center of the field in a very amazing scenario. Simply said, he started his career selling products, where he enhanced his skills in understanding the product and the point of view of clients from the customer’s perspective, which simplified his journey in the long run. It makes him an interesting personality among other writers. Currently, he is a regular writer at Craw Security.
READ MORE ARTICLE HERE






